Browser extension security
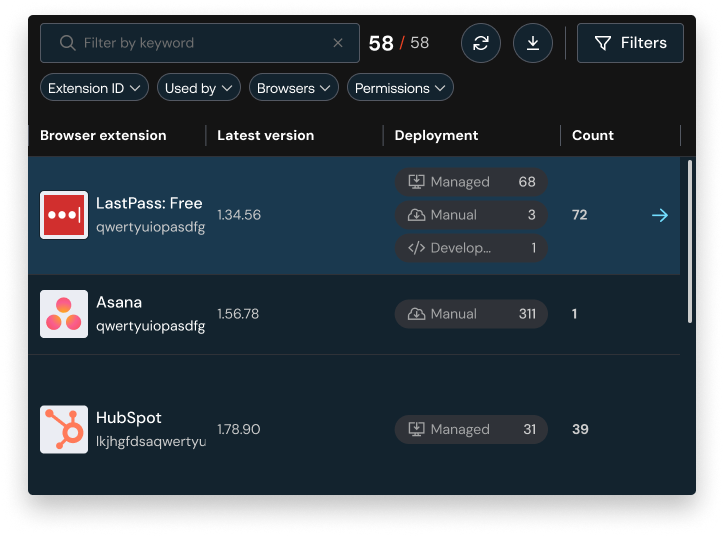
Browser extensions introduce new code, new permissions, and new potential for risk. Most go completely unnoticed. Push gives you full visibility into every extension used across your workforce, across major browsers, so you can uncover shadow IT, assess risky permissions, and block unsafe tools before they lead to compromise.
Take control of browser extensions
Attackers are increasingly using malicious browser extensions to gain access to data processed and stored in the browser. And the problem is, most security teams have no visibility into what extensions are being used. Push changes that. With browser-native telemetry, the Push extension continuously inventories browser extensions across your environment, flags the risky ones, and gives you intelligence to act.
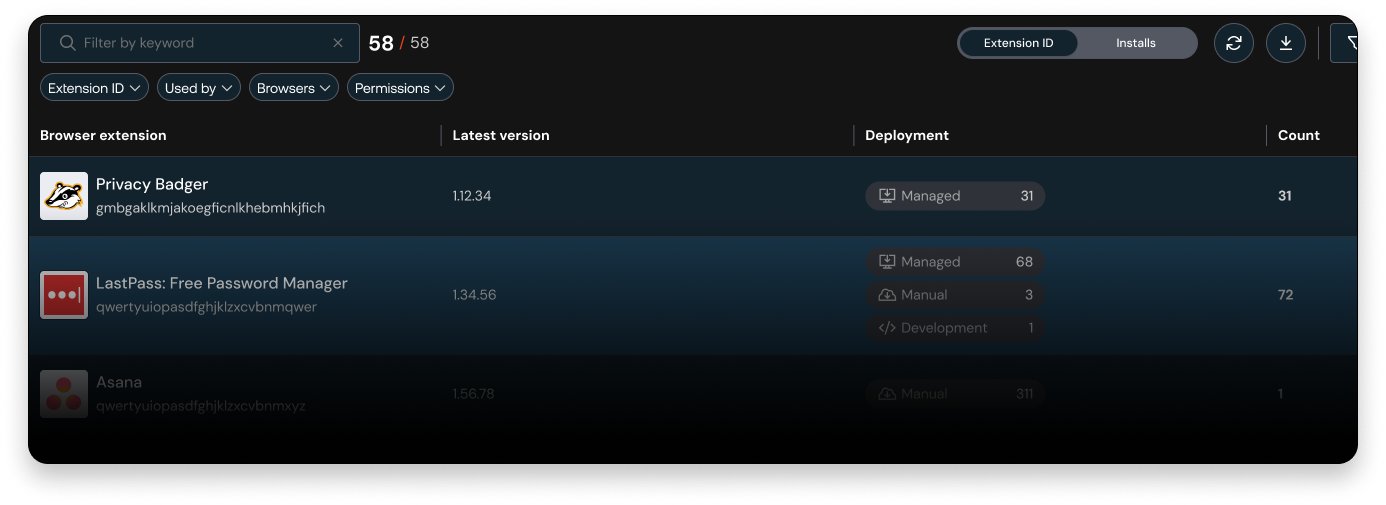
Discover every extension in use
Push gives you structured, searchable data about every extension in your environment, so you’re not just seeing what’s there, but also understanding how it got there, what it can do, and who it affects. It’s the kind of granular insight that’s nearly impossible to get from traditional tools, and it lays the groundwork for better policy decisions and faster investigations.
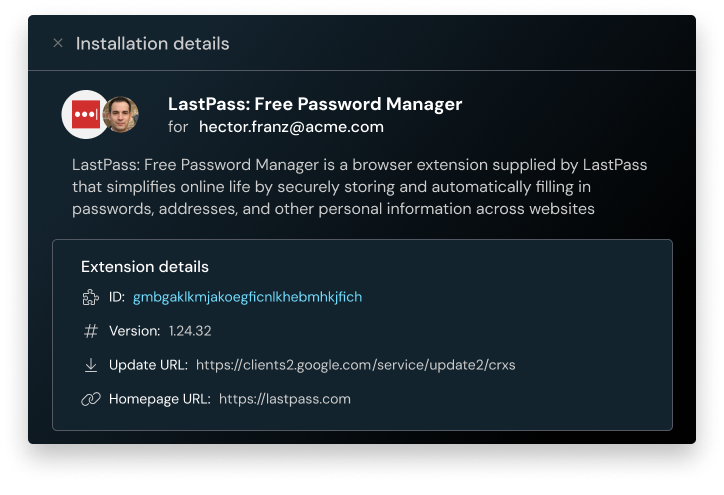
Spot risky or malicious extensions
Push highlights extensions with dangerous permissions, broad access, or poor reputations. You can quickly detect sideloaded, manually installed, or development-mode extensions that bypass normal controls. And because Push shows you who’s using them and where, you can respond precisely and effectively.
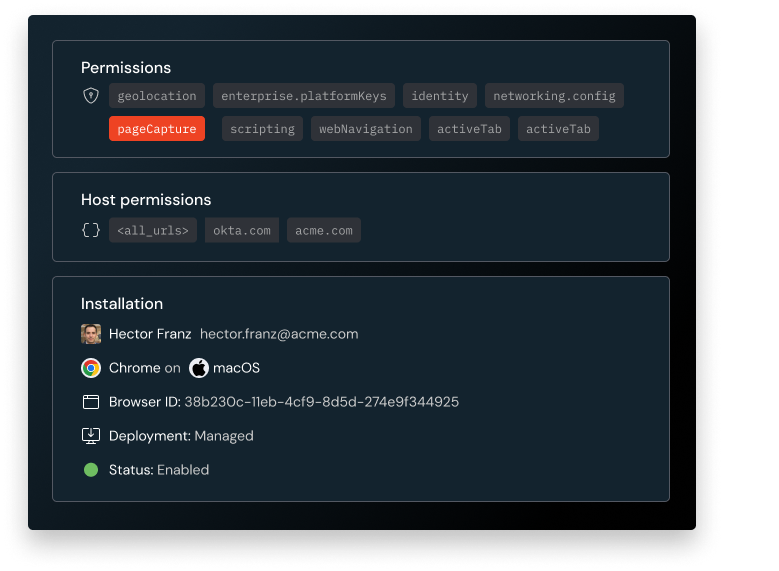
Accelerate security reviews
Most teams have extension policies, they just don’t have the data to enforce them. Push reveals how each extension entered your environment, whether it was installed manually, sideloaded, or deployed in dev mode. You’ll see which users are running what, and where, so you can surface violations, investigate quickly, and respond with confidence.