Push Security resources:
Search our content library


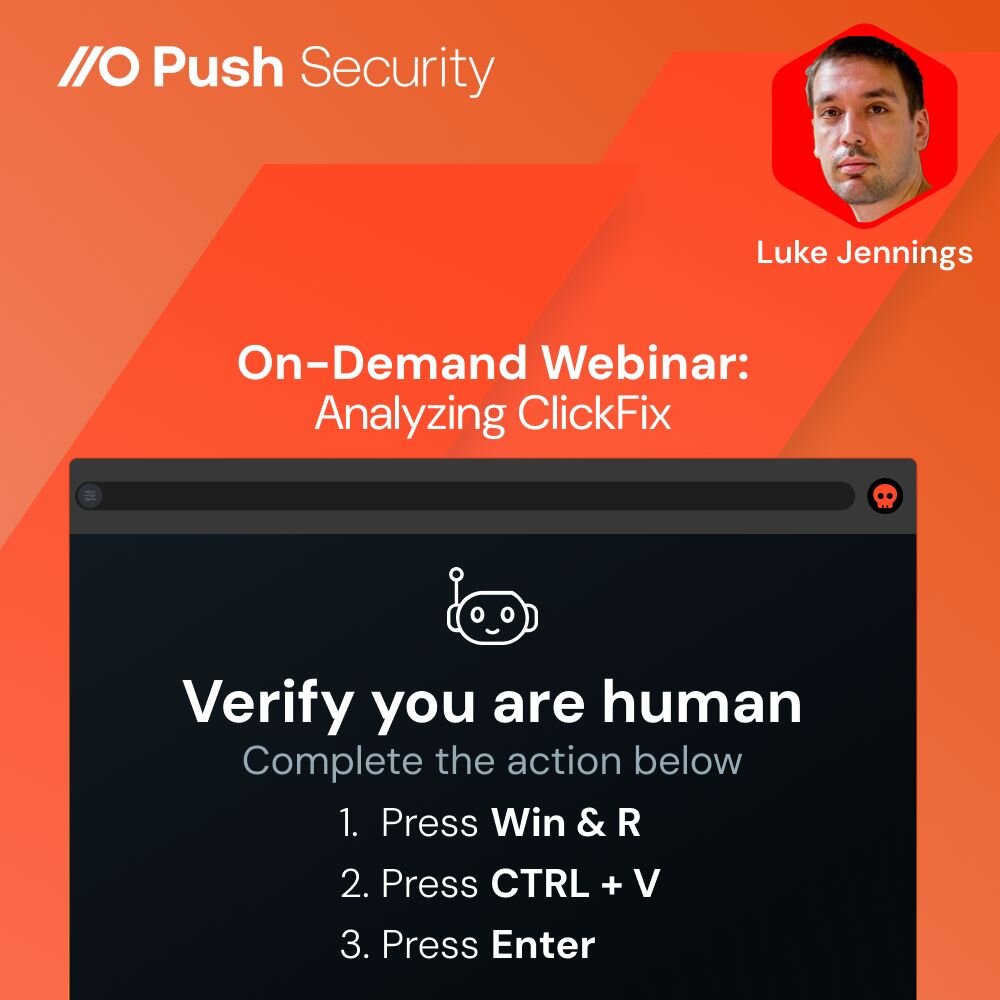



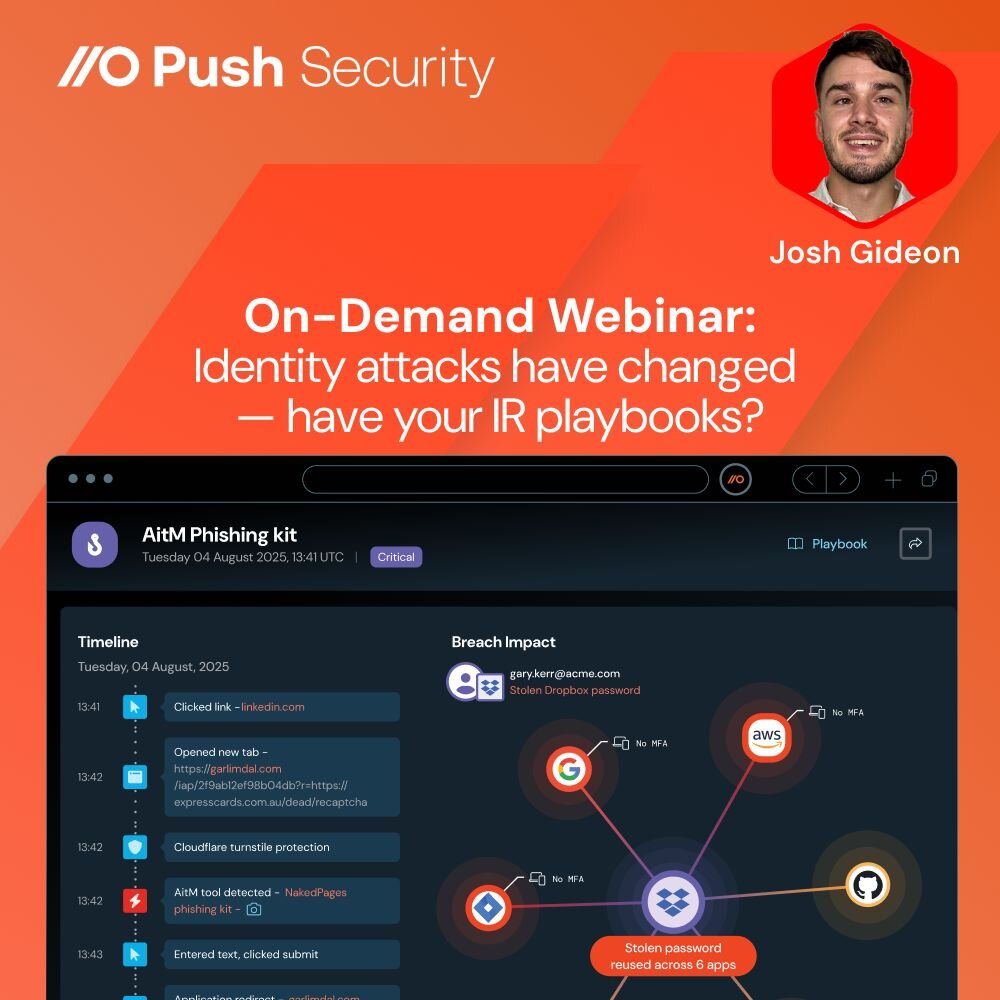





































New Webinar: Malicious Browser Extensions —
A Threat Modeling & Mitigation Playbook
Attackers are doubling down on malicious browser extensions as their method of choice. Recent campaigns like ShadyPanda, ZoomStealer, and GhostPoster all highlight the threat posed by malicious extensions. Join us for a teardown of malicious extension functionality, where you’ll learn how to defend your organization from this new attack vector.