The most advanced security tool in the browser
The Push browser extension gives security teams real-time detection, investigation, and response power in the browser.
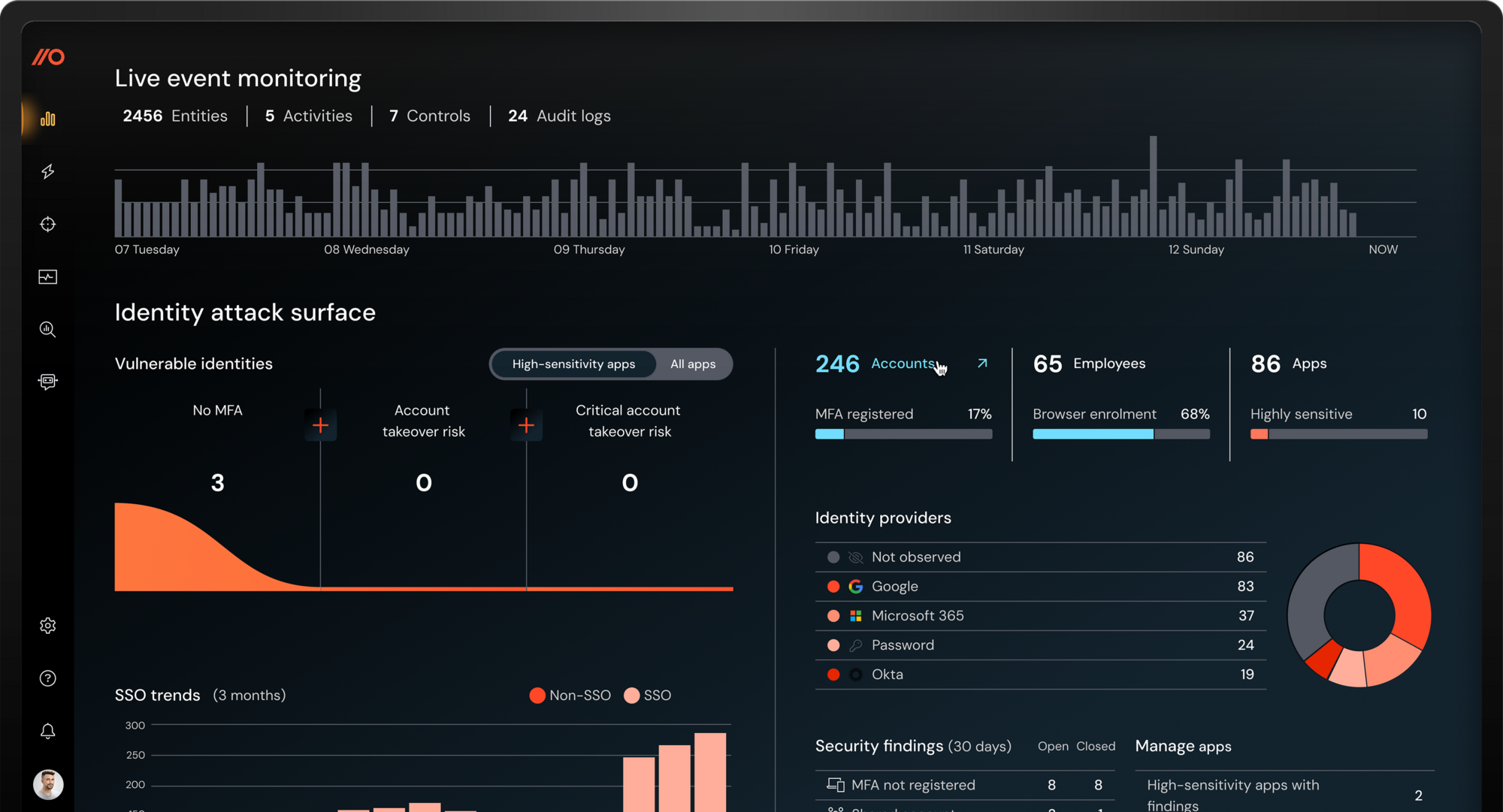
See the bigger picture of what's happening in the browser
Modern attacks happen in the browser
From credential phishing to token theft and shadow SaaS, attackers exploit in browser activity that most tools can't see.
Push changes that
By operating directly in the browser, Push captures the full story — user behavior, page structure, and attacker actions — to power higher-fidelity detections, faster investigations, and controls that actually stop attacks.
This gives defenders a real advantage:
Higher-fidelity detections.
Faster investigations.
Controls that actually stop attacks.

The modern SecOps stack
Tools focused on the endpoint, network, and inbox are foundational. But attackers opened a new front inside the browser session, a layer those tools weren't built to inspect.
Your CNAPP and ITDR platforms secure your cloud infrastructure and your IdP, but not the browser session. Push secures access to your cloud resources via the browser.
Push Security provides blue teams with net-new visibility of browser-based attacks to complement your existing threat detection & response stack.
EDR doesn’t provide security in the browser layer. Push works alongside your EDR deployment to give you protection at the new layer for attackers.
Proxy based solutions like SSE, SWG, and CASB, see traffic, not what your users see. Push provides in-tab visibility into page structure, scripts, and user interaction.
Hear what people are saying about Push
Today’s security leaders know that defending the browser is key to the future of cyber defense.
Using the Push Platform
Stop attacks
Secure your organization via the browser
Detect and block in-browser threats in real time: phishing kits, token theft, and session hijacking. Push inspects page structure, content, and user interaction to spot cloned logins, malicious scripts, and credential misuse as the user sees them.
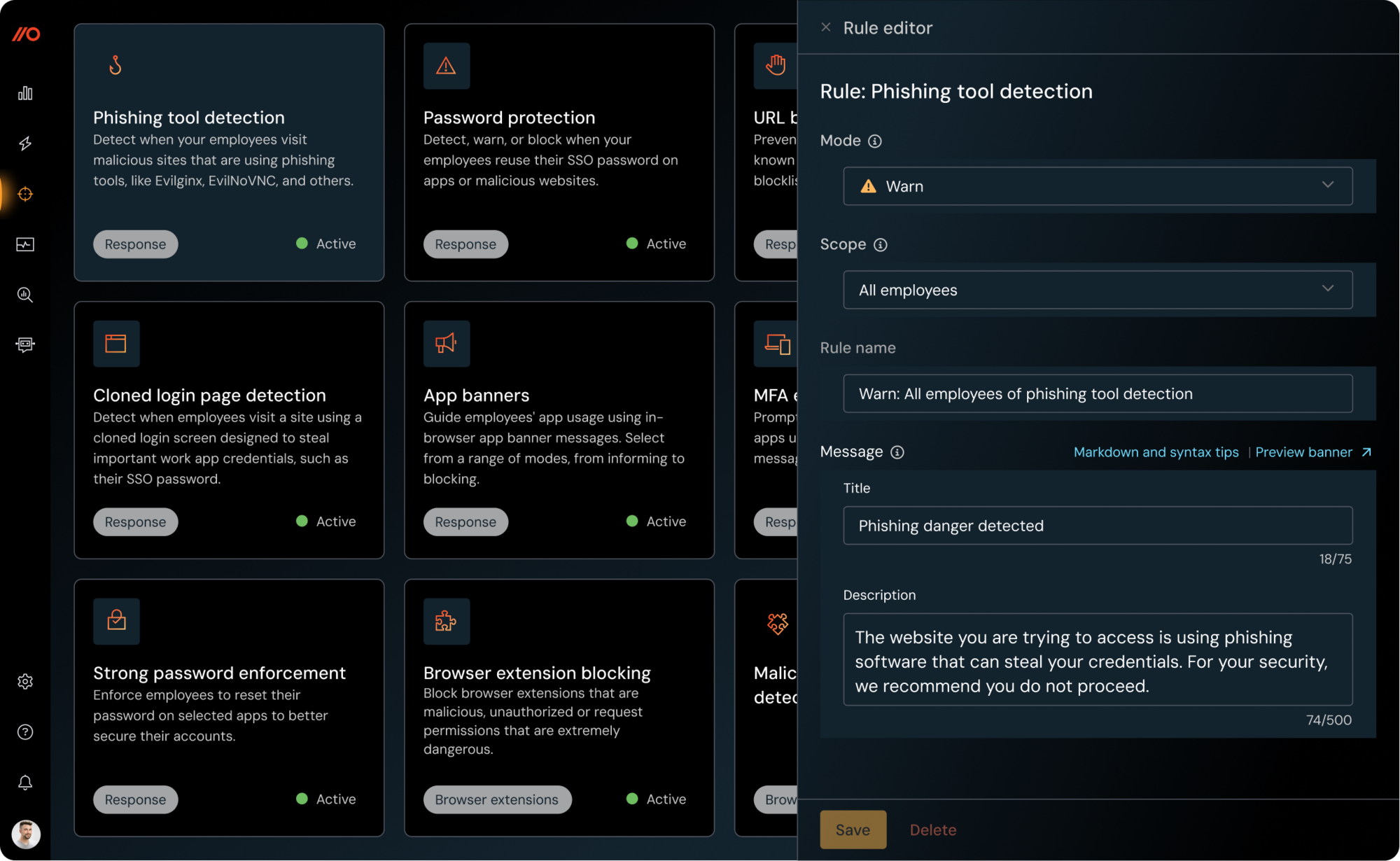
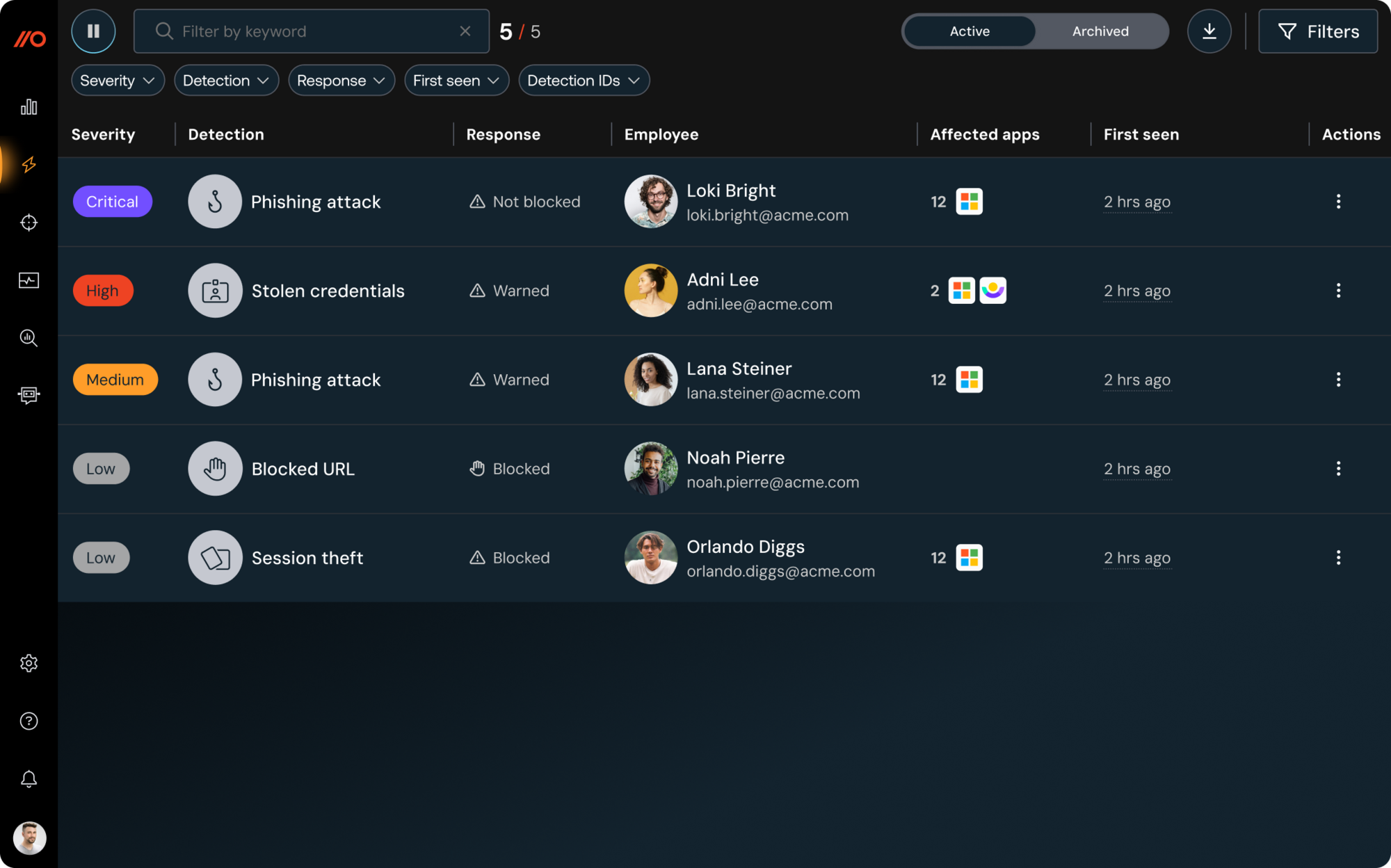
Investigate faster
Detect and respond like never before
Reconstruct what happened, fast. Push captures page loads, click paths, credential use, and token activity to build user/session timelines, revealing attacker behavior, blast radius, and OAuth exposure.
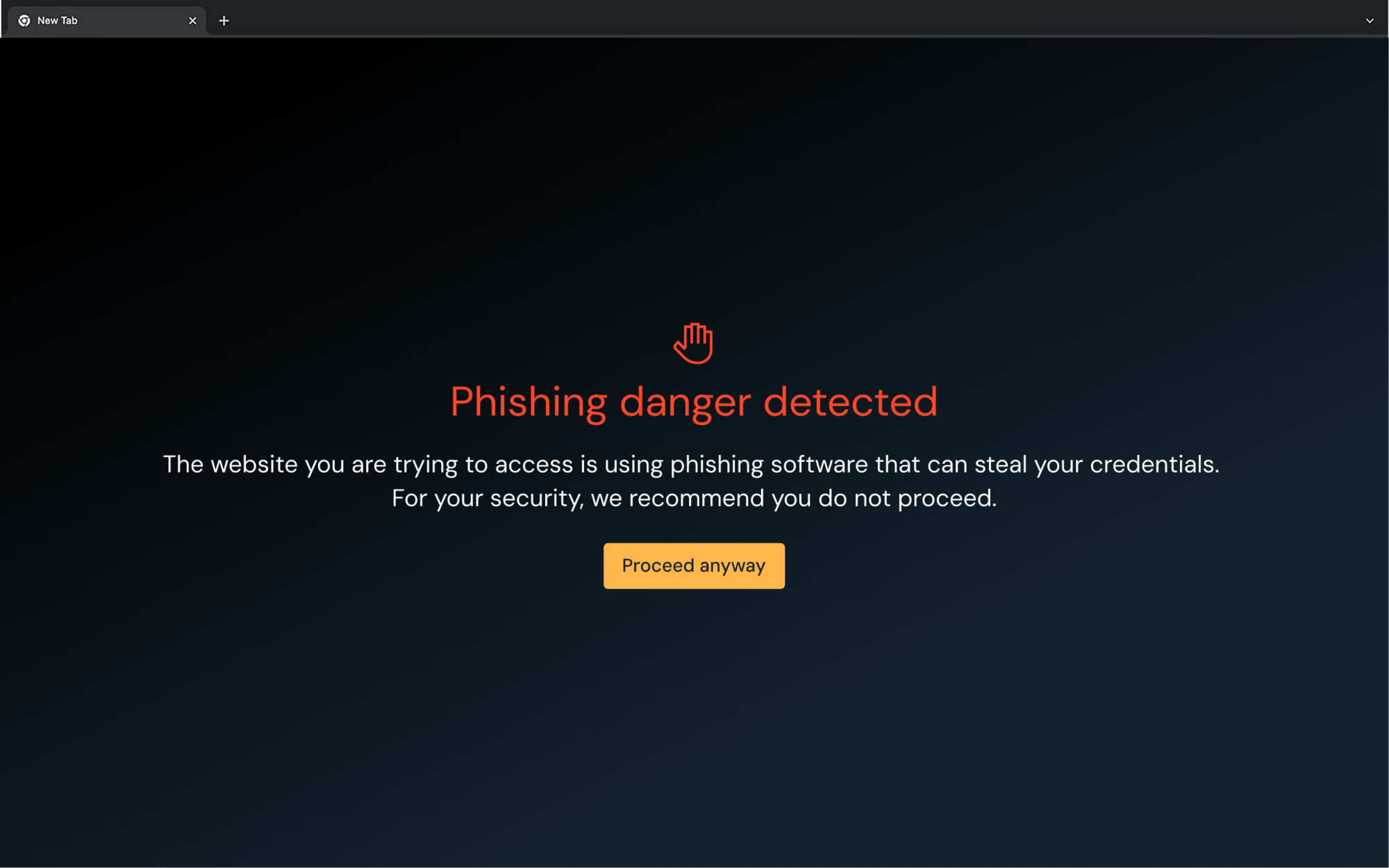
Protect users
Gaps are everywhere, and attackers are looking for them
Close common gaps before they're abused. Push flags missing MFA, password reuse, non-SSO logins, shadow apps, and risky extensions, then guides users to remediate or enforces policy in the browser.
One week in and already ahead of attackers
Day Zero
Rapid deployment via MDM, to every browser
Our record: 100k users in 1 hour during normal office hours.

Day One
Instant protection and insights for your users
Stop phishing, session theft, and malware delivery from day 1
Week One
Operationalize with 1st class IdP & SIEM integrations
Harness the power of browser telemetry to fix vulnerabilities and respond to incidents.








