Using Push, you can now see which password managers your employees are storing their work credentials in. Make sure sensitive corporate credentials don’t leave your corporate environment and end up in personal password managers.
Using Push, you can now see which password managers your employees are storing their work credentials in. Make sure sensitive corporate credentials don’t leave your corporate environment and end up in personal password managers.
Which password managers are my employees using?
Tens of millions of people now use password managers, both at work and at home. And it probably won’t come as much of a surprise that most of Push’s security-savvy customers also provide their users with a corporate password manager.
Up until now, Push has been able to show you whether or not your employees are using a password manager to log into their work apps. But now, we can actually show you which password managers they’re using.
There’s more than first meets the eye with this detection
There’s a couple of reasons why you’ll want to know which password managers your employees are using.
The obvious one is to make sure all your employees are using, and benefiting from, the password manager you're providing them with. They’re not cheap and you’ll want to get the best bang for your buck.
The second reason speaks to a specific concern a lot of security teams have around attackers compromising users’ personal password managers containing corporate passwords, and then being able to pivot into the organization's corporate environment. This is a very valid concern given the rise in attacks using infostealers following the Snowflake breach earlier this year.
Using this feature, you can now detect which password managers are storing credentials for your most sensitive systems and stop this attack scenario from happening.
Why corporate passwords in personal password managers is a big no-no
Remote working, BYOD, and users having both personal and professional accounts on the same platforms (Google, Microsoft etc.) have all blurred the line between people’s work lives and their home lives. It’s not uncommon for one to spill over into the other, and one place we see evidence of this is in password managers.
Creds for personal accounts end up getting stored in corporate password managers, and corporate creds end up getting stored in personal password managers.
The big risk when the latter happens is that a sensitive corporate asset (a users’ Microsoft account password for example) is effectively being exfiltrated out of the corporate environment by the user, and placed out of reach of your security team.
This creates new opportunities for attackers:
Your average user’s personal laptop isn't going to be as well protected as their company laptop. So they offer an easier target for attackers using traditional endpoint compromise techniques.
An attacker can compromise a personal laptop with infostealer malware that targets password managers in the browser. If corporate credentials are stored in that personal password manager then they are also going to be stolen.
Now the attacker is in possession of the user's Microsoft account credentials, they can potentially pivot from a personal laptop to one of your organization's core platforms over the internet.
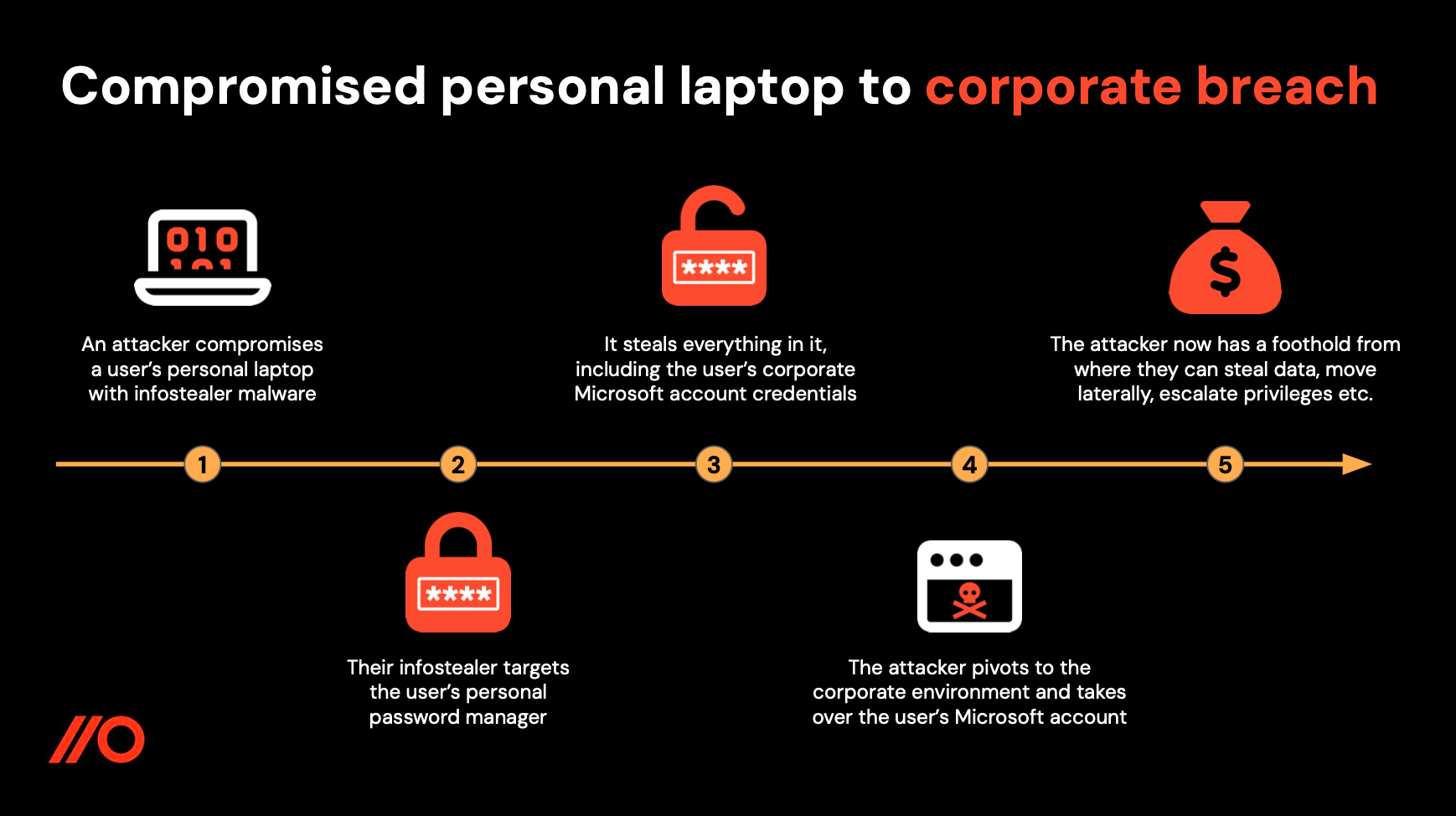
Using Push, you can now make sure that sensitive corporate credentials stay in your corporate password manager and don’t leave your corporate environment.

All powered by the Push browser extension
Push detects which password managers your employees are using with our browser extension. It observes all your employees logins using their work identities. The telemetry the browser extension generates shows you what employees are logging into, when they’re logging in, how they’re logging in, and if any aspect of that login process is risky or potentially malicious.
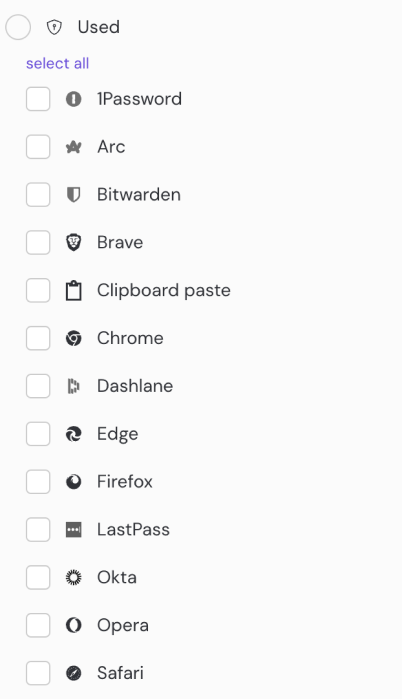
The password managers (and browsers with built-in password managers) supported by this detection are:
When a login using one of those password managers is observed by Push, it appears in your events feed. This data can be sent to your SIEM using Push’s webhooks.
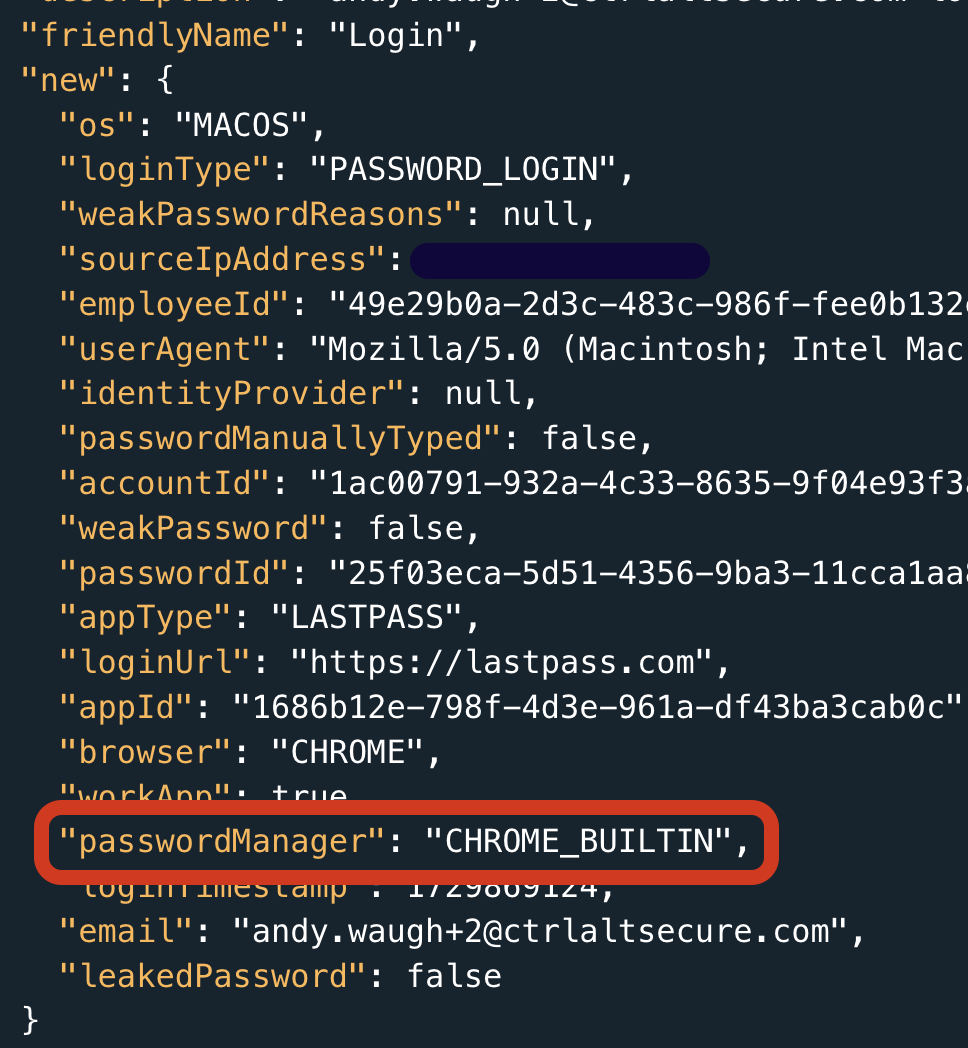
The password manager user will also appear on the corresponding account on the accounts page. Here you can see every workforce account and the login methods used to access them.
Bonus feature — detecting clipboard pasting
The eagle-eyed among you might have seen that in the list of supported “password managers” is one called Clipboard paste.
You’ll see this when we observe users pasting a password into the password field. This detection is really useful for a couple of reasons:
Copying passwords from a password manager and pasting them into a login page is bad practice. Password managers typically also store which page the password is for so they won't auto-populate on a phishing page. Pasting your password manually makes you more susceptible to being phished.
Or, it could indicate that the user is storing their passwords in a notes app, word doc, spreadsheet etc. Obviously these are all low hanging fruit for any attacker so you want to get the user to move their passwords into their password manager and set fire to whatever doc they had been using.
Try it out for yourself
If you have any question about this feature or any other of our detection use cases, book a meeting with one of our team.

