Manage security controls
Overview
Use the Push browser extension to detect and block browser-based attacks and enforce your security controls by requiring MFA and strong passwords, blocking unwanted apps and extensions, and more.
You can configure these options on the Controls page in the Push admin console. Note that employees must be enrolled in Push and using the Push browser extension for controls to be enforced.
Configure app banners
Use app banners to apply guardrails to your employees’ use of apps. This control allows you to place a message directly in the browser on an app’s login and signup pages, or on specific URLs or URL patterns.
You can configure app banners from the Controls page by selecting the App banners tile and then configuring a rule for the app banner.
For each rule, you’ll select the banner Mode (see examples below); the Scope (all employees, specific employees, or employee groups); and whether the rule applies to all apps, specific apps, or app attributes (e.g. sensitivity and approval status or custom labels). Then customize the banner text.
There are four modes for app banners.
Set the mode to Inform for a smaller, dismissible message at the top of the page.
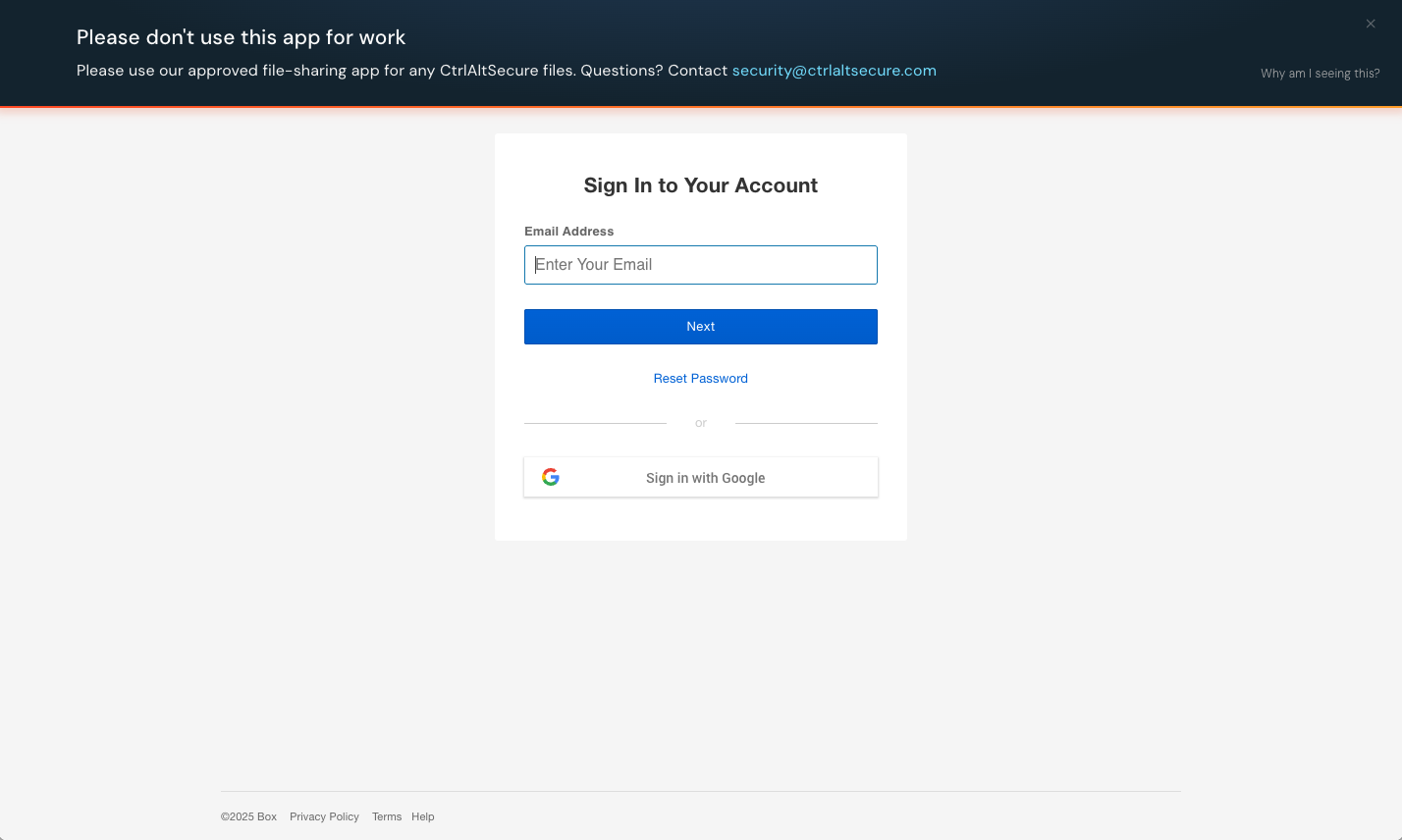
Set the mode to Acknowledge for a larger banner that covers the middle of the page and requires that end-users click a button to acknowledge the message before they can sign up or log in.
Push will also emit a webhook event if you wish to track when app banners are displayed and acknowledged.
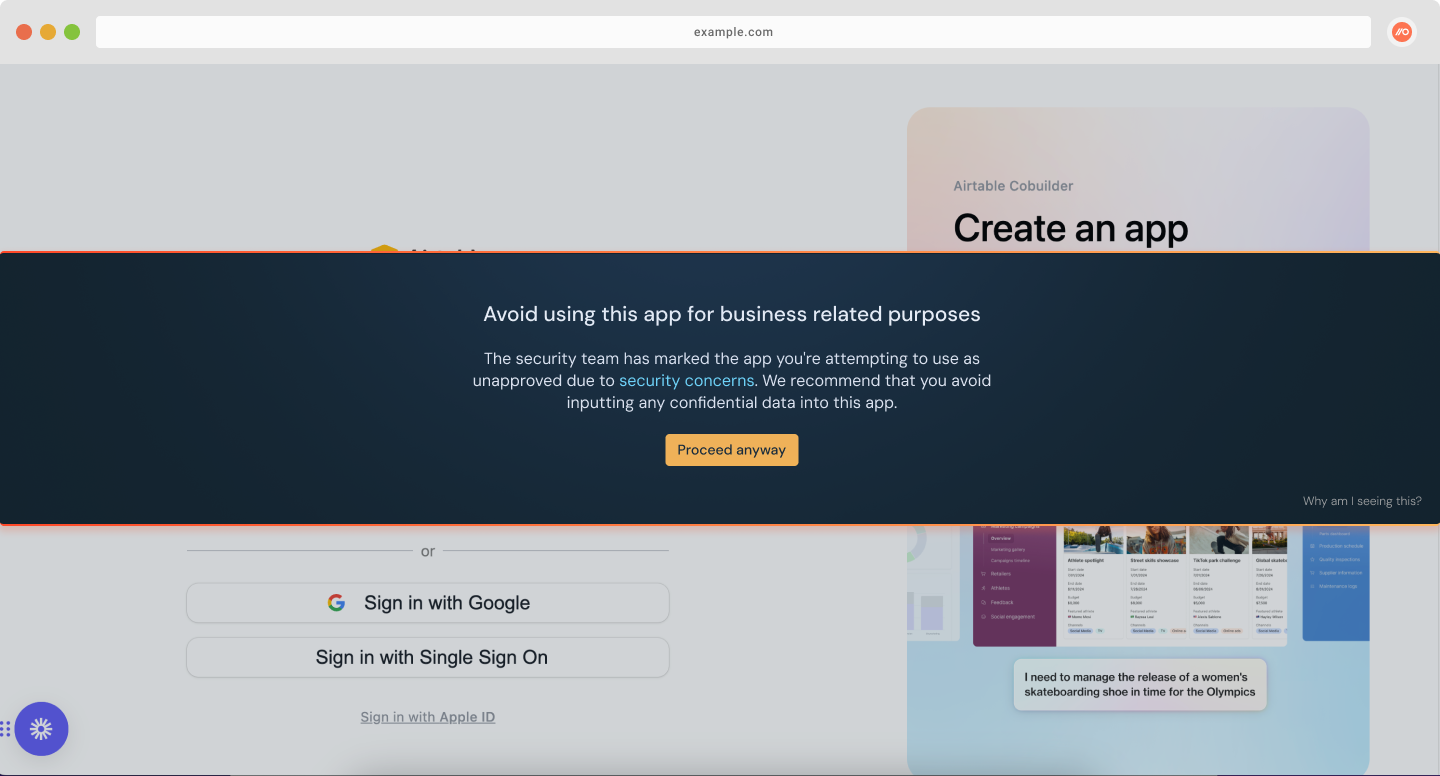
Set the mode to Reason for a large banner that covers the middle of the page and requires end-users to submit a reason for using an app before they can sign up or log in. Push will also emit a webhook event to capture the submitted text from the end-user.
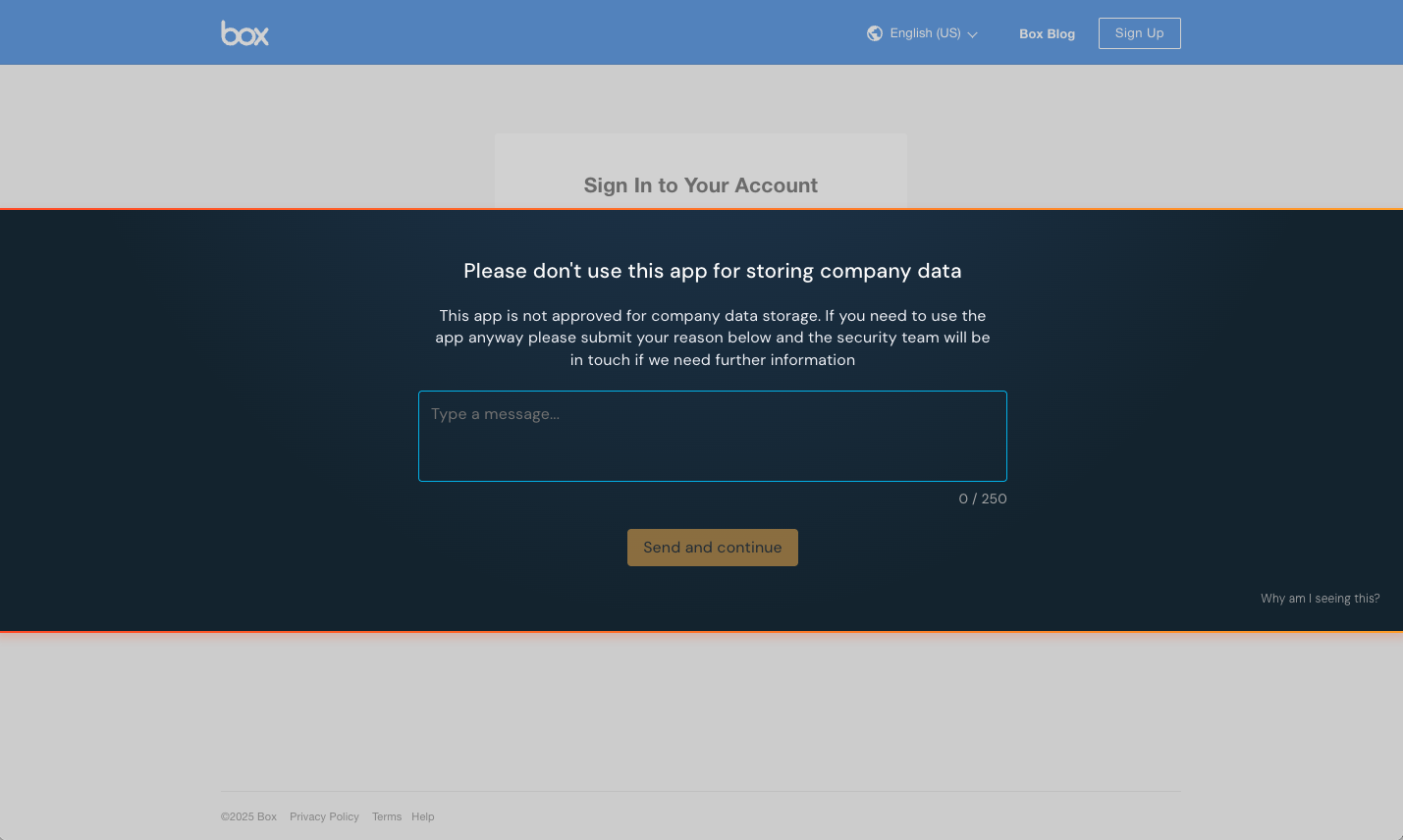
Set the mode to Block for a larger banner that covers the middle of the page and prevents the end-user from signing in to the app. Optionally, you can also allow end-users to submit a request to use a blocked app directly from the banner. Push will emit a webhook event to capture the submitted text.
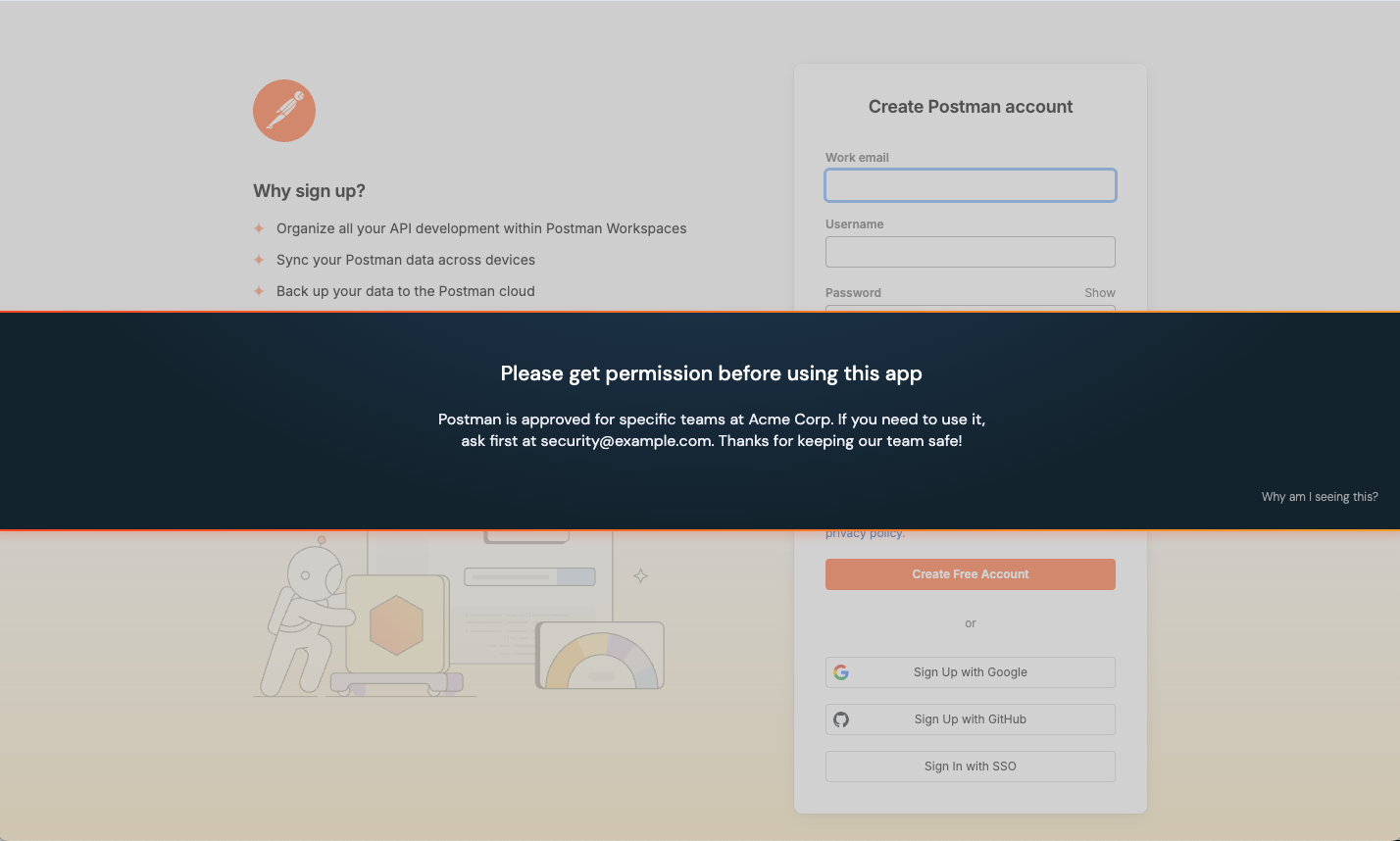
You can preview the app banner in your browser right in the Push admin console, and publish it when you’re ready.
Use app banners to:
Block a recently breached app while you investigate.
Block unapproved apps.
Encourage employees to use a preferred app over an alternative.
Remind employees not to enter sensitive information or company data into GenAI tools.
Ask employees not to use an app until it can be reviewed by the security team.
Restrict use of high-sensitivity apps to certain teams or roles.
Or anything else you want!
For more examples of how to use app banners, refer to this help article.
Configure URL blocking
Prevent employees from visiting malicious websites by configuring a blocklist of URLs. If employees try to visit a blocked URL, they will see your custom block message instead of the site.
This feature allows you to respond to phishing incidents by blocking the phishing URL across your entire workforce. You can also implement blocks for known-bad websites.
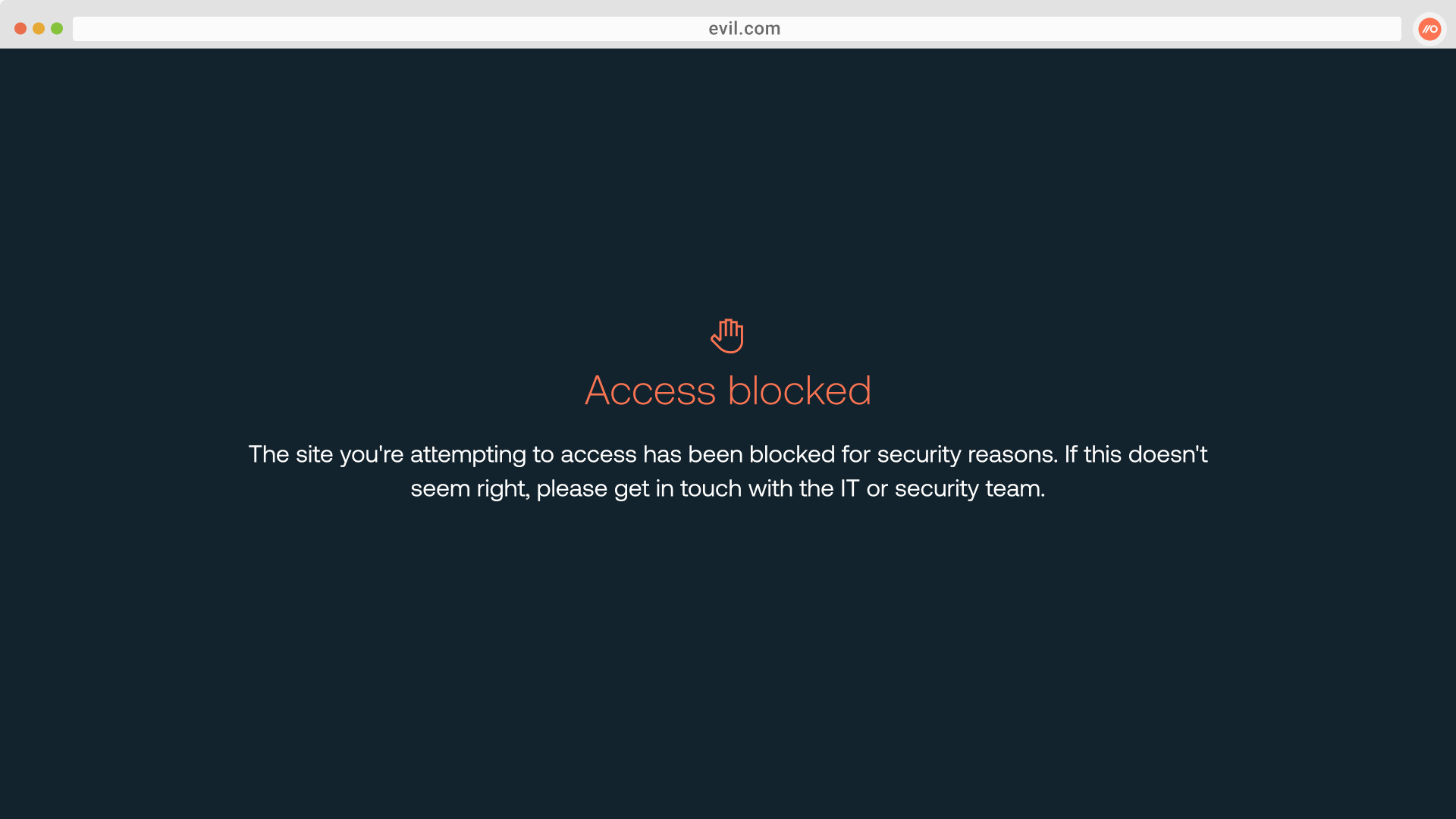
Push will also emit a webhook event when a blocked URL is visited.
You can configure URL blocking on the Controls page of the admin console. You can programmatically manage URL blocking as part of responding to an attempted phishing incident by using the Push REST API to automatically add URLs to the blocklist or to sync with other threat intelligence sources of known-bad sites.
When adding URLs to your blocklist, you can use a wildcard * (star / asterisk character) to partially match website domains.
For example, *.example.com will catch any subdomains in example.com.
Note: URL match patterns do not support the syntax *.example.* You must use the syntax *.example.com or *.example.org if you wish to have a wildcard for subdomains.
To catch all pages on a domain, use the syntax example.com/*. You can combine these two approaches to catch all pages and all subdomains by using the syntax *.example.com/*
You can configure URL blocking on the Controls page of the admin console.
Configure password protection
Warn or block employees from entering their important passwords into unauthorized or malicious sites, and display a custom message.
There are three modes for Password protection.
In Monitor mode, Push will silently report when and where protected passwords were used without alerting the user.
In Warn mode, Push will display a customizable warning message to users that they’ve re-used their protected password on another site. The user can ignore the warning to continue if they know the site is trustworthy.
In Block mode, Push will prevent users from logging in with their protected password on any webpage except those belonging to the app and display a customizable block message.
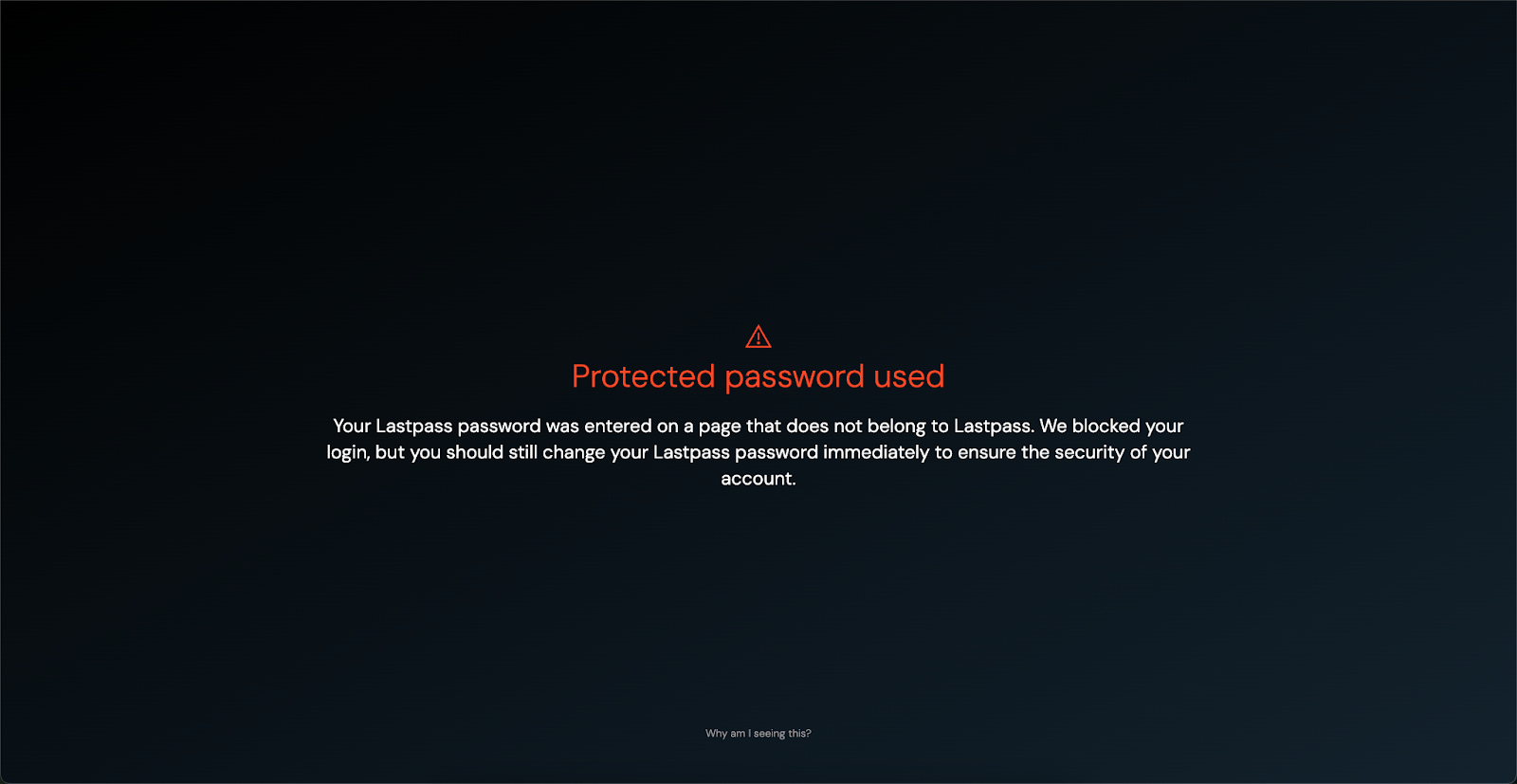
Push will emit a webhook event when a protected password is used, and if the employee clicks through the warning screen.
You can configure a list of domains to ignore when enforcing this control. Learn more in this related help article.
You can configure Password protection on the Controls page of the admin console.
Configure phishing tool detection
Detect when employees visit websites that are using phishing tools such as Evilginx, which can mimic legitimate login screens in order to steal credentials and MFA codes. Then warn or block employees from accessing those sites.
Push will emit a webhook event when signatures for these phishing tools are detected on sites visited by your employees. Consider adding those malicious websites to a blocklist to enforce URL blocking.
You can configure phishing tool detection in Monitor, Warn, or Block modes.
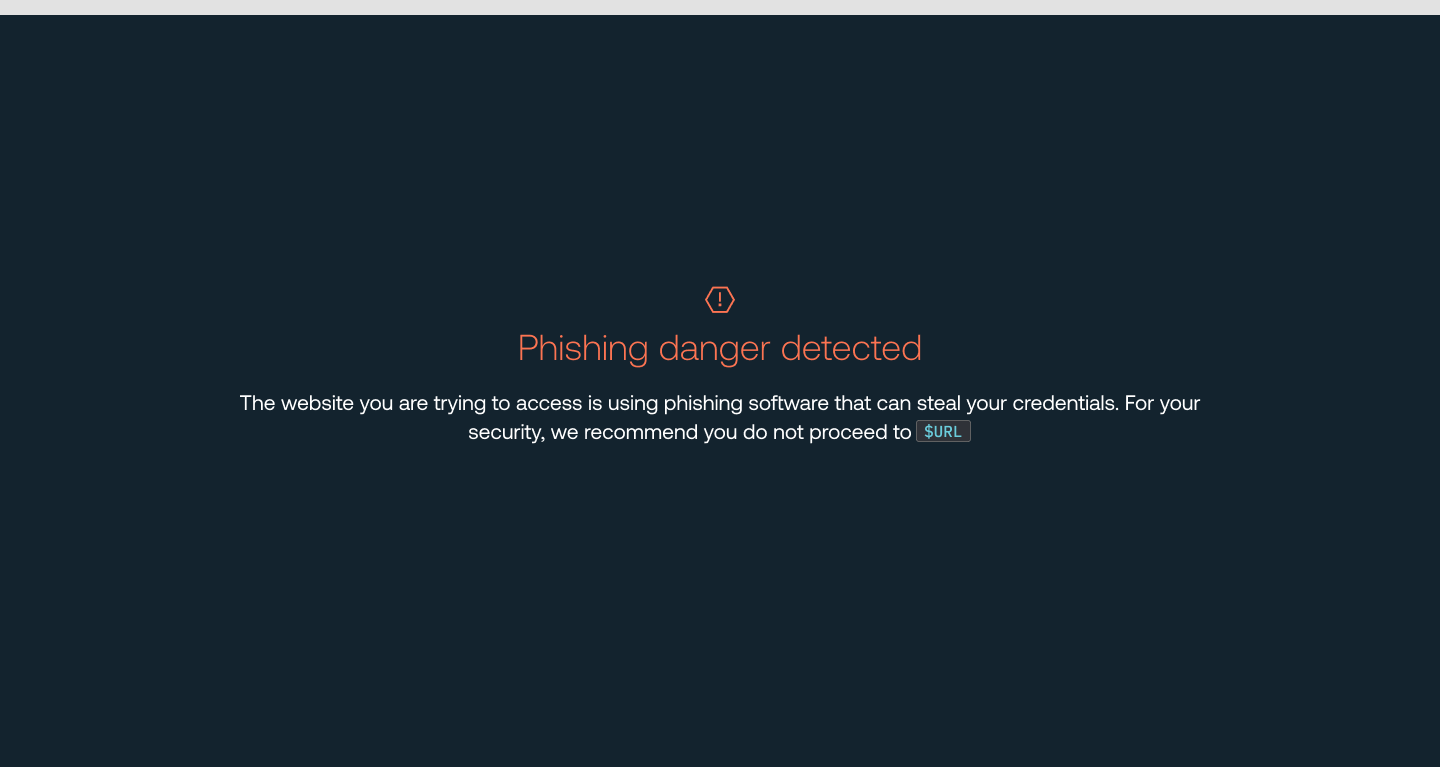
Learn more in this related help article.
You can enable phishing tool detection on the Controls page of the admin console.
Configure session theft detection
Push provides a security control configurable by administrators that allows you to inject a unique marker into the User Agent string of sessions that occur in browsers enrolled in Push. This feature is powered by the Push browser agent.
By analyzing logs in the target app, you can identify sessions that both have the Push marker and that lack the marker, indicating the session is being used from both a machine with the extension and a machine without and therefore the session token may have been stolen.
Note: While Push can inject the unique marker into sessions on any domains you specify, the identity provider or application must provide a server-side session identifier so that you can determine which activity belongs to the same session, and then identify whether a marker is absent from activity on Push-enrolled browsers where you expect it to be present.
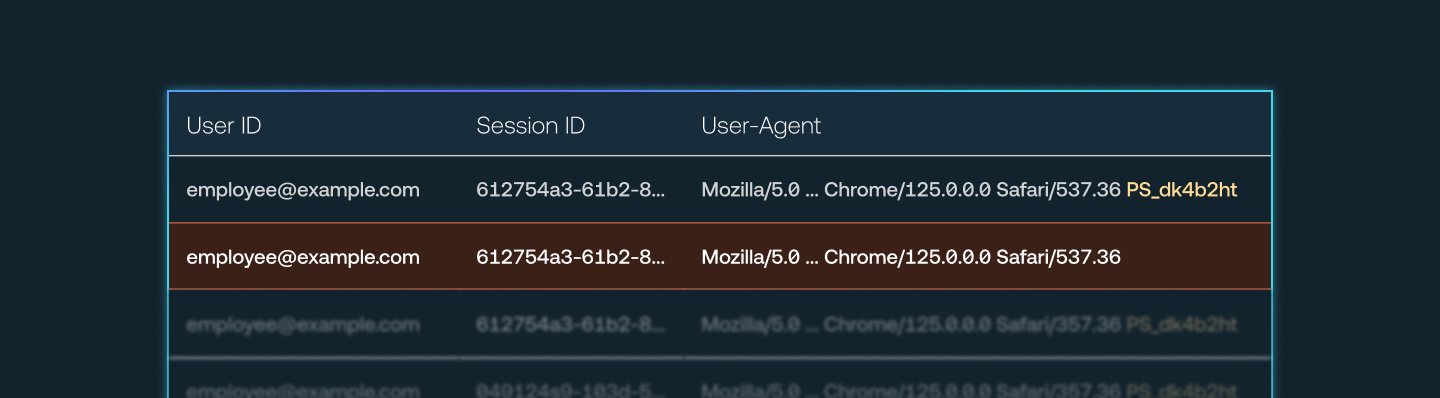
Any “unmarked” activity in the same session should be treated as a high-fidelity signal of session token theft, also known as session hijacking.
Learn more in this related help article.
You can enable session theft detection on the Controls page of the admin console.
Configure cloned login page detection
Detect when employees visit sites using cloned login screens that may be used to mimic identity provider login pages in order to steal credentials.
Once you enable Cloned login page detection, Push will emit a webhook event when it detects that an employee has visited a page that appears to be a clone of a legitimate login page.
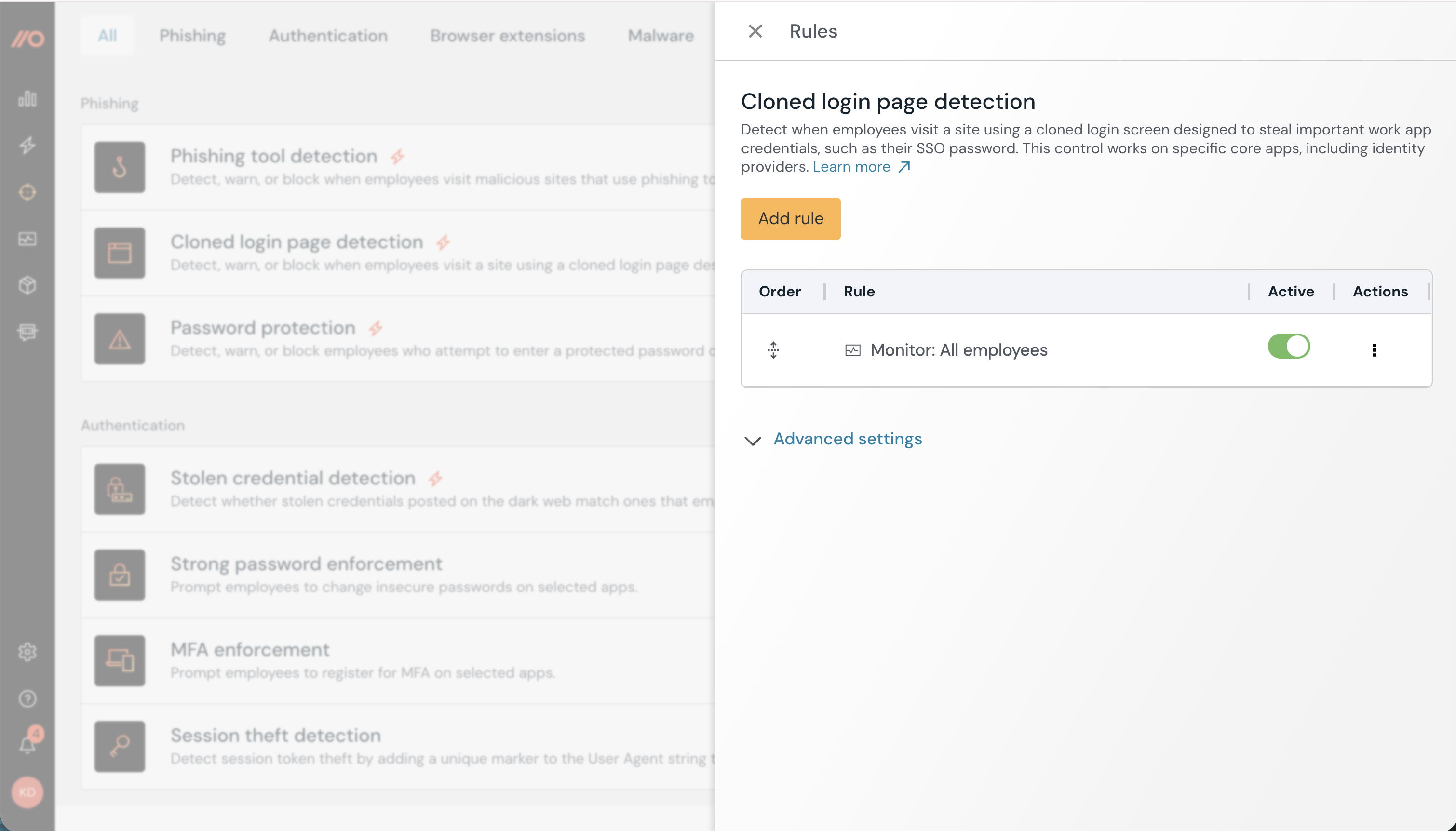
It does this by fingerprinting the page structure and resources of your legitimate login pages and monitoring for pages that appear to be very similar.
Learn more about cloned login page detection in this help article.
Important! Be sure to add any custom login URLs that you use to your Settings page to ensure they are detected.
Configure stolen credential detection
Detect stolen credentials in use across your workforce identities. Push does this by ingesting threat intelligence data and then verifying which credentials flagged by TI sources are still being used by employees, performing comparisons of hashed, salted, and truncated credentials using the Push browser extension.
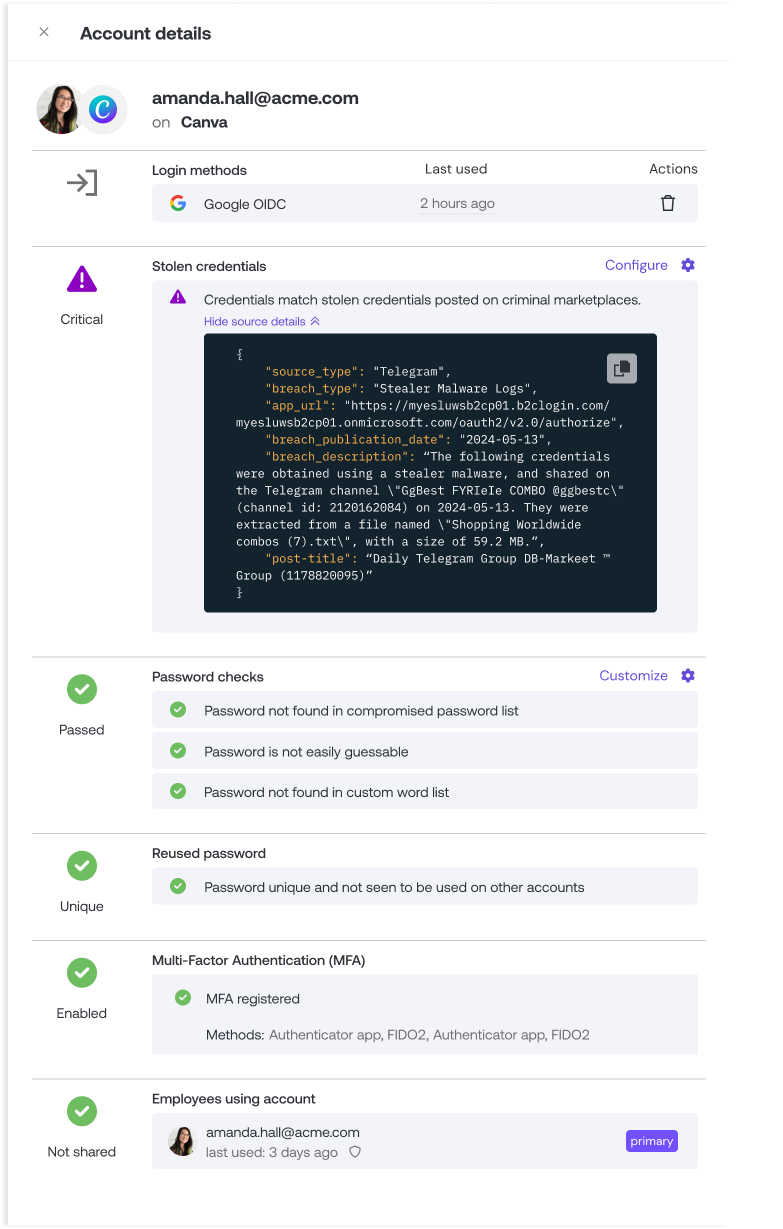
You can choose to receive alerts for this detection via webhook, ChatOps notification, or in the Push admin console.
Learn more about stolen credential detection in this help article.
Configure MFA enforcement
Prompt employees to register for MFA on apps where they lack it, using MFA enforcement. This control allows you to display a customized banner that end-users will see when they use accounts that are missing MFA protection. You can select which apps to enforce MFA on when configuring the control.
Learn more in this related help article.
Configure strong password enforcement
Prompt employees to change an insecure password using Strong password enforcement. This control allows you to display a customized banner that end-users will see when they use accounts with password issues such as stolen credentials, weak, or reused passwords. You can select which apps to enforce strong passwords on when configuring the control, as well as which specific type of password issues you want to remediate.
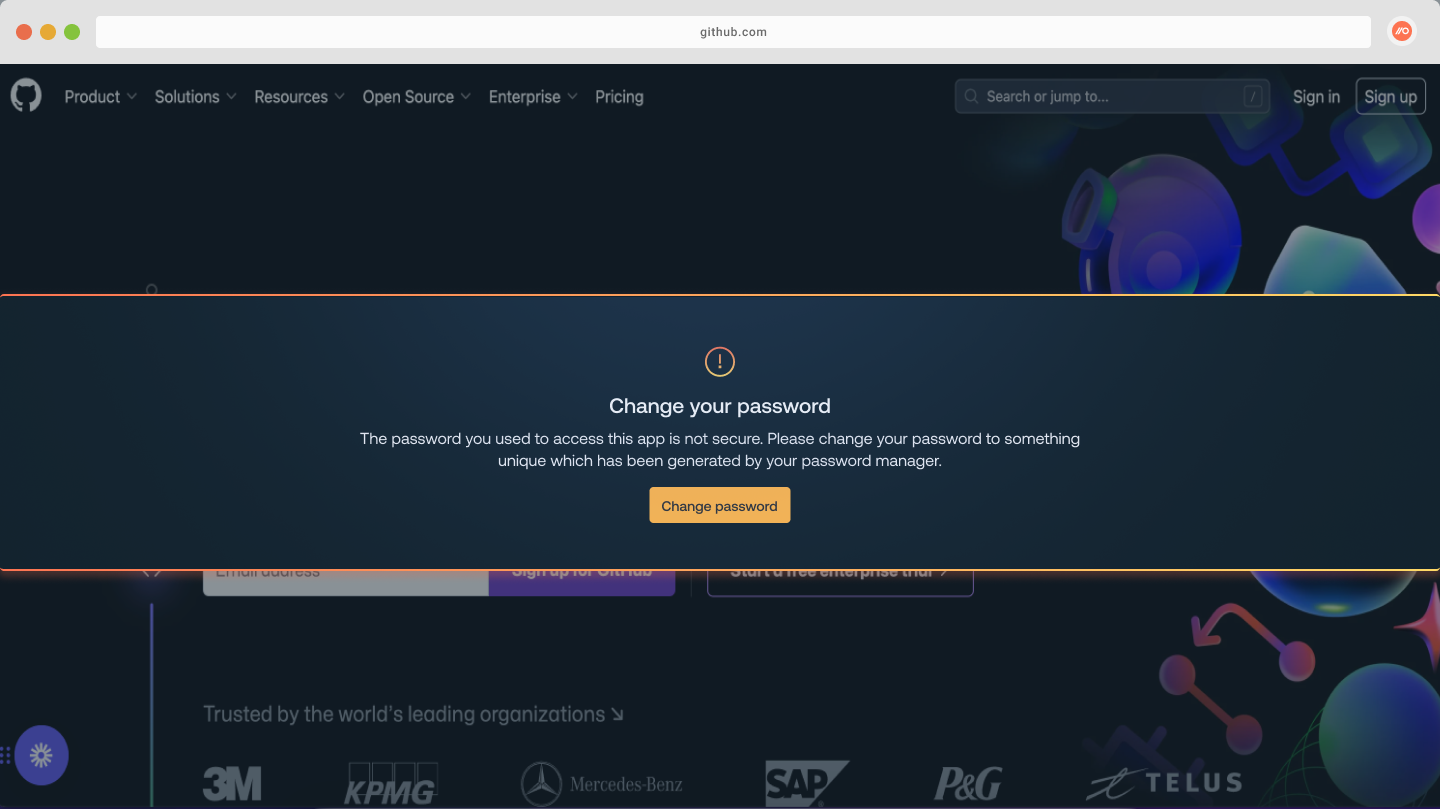
Learn more in this related help article.
Configure malicious copy and paste detection
Detect when webpages visited by employees are using an attack technique that relies on malicious scripts being copied onto a user’s clipboard — common examples include ClickFix and FileFix. Detections will appear on the Detections page.
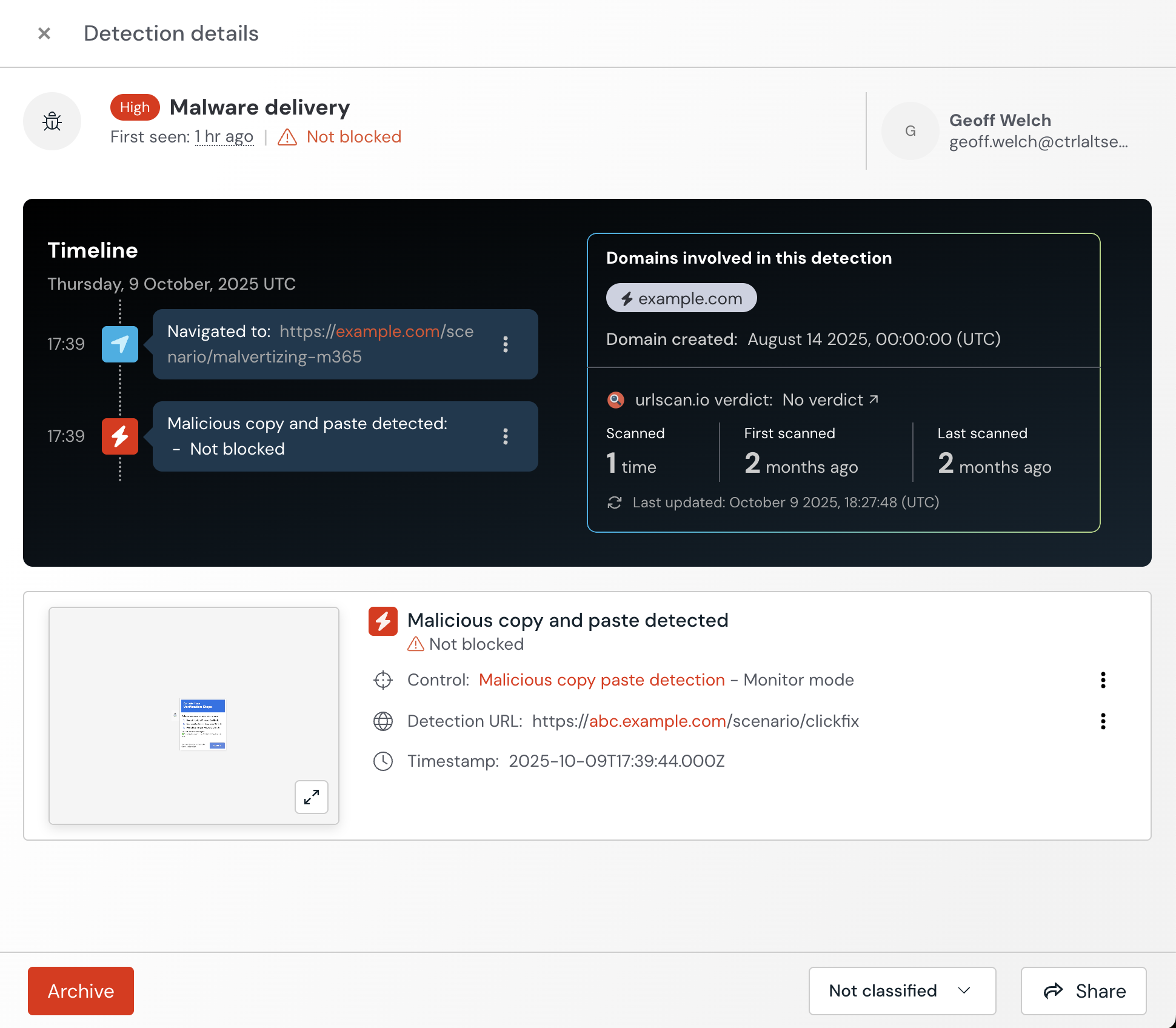
Learn more in this related help article.
Configure browser extension blocking
Block malicious or unwanted browser extensions, or create an allowlist of acceptable extensions using configuration rules.
Learn more in this related help article.