Managed deployment using an MDM on macOS
Overview
Deploy the Push browser extension in Google Chrome, Microsoft Edge, Firefox, Brave, Safari, or Arc on macOS using a mobile device management (MDM) solution.
Push provides a standard config that can be imported and deployed via any MDM solution that supports provisioning custom configuration profiles to macOS endpoints. The directions below are not specific to a particular MDM. You should consult the documentation of your MDM solution to determine the best way to deploy the profile.
Here are a few popular MDM solutions and their instructions on deploying custom configuration profiles for macOS:
Generate the configuration profile
Before configuring your MDM, we need to generate a config file in the Push admin console. Skip to the next step if you've already done so.
1. In the Push admin console, head to the Browsers page, and click on Enrollment options.
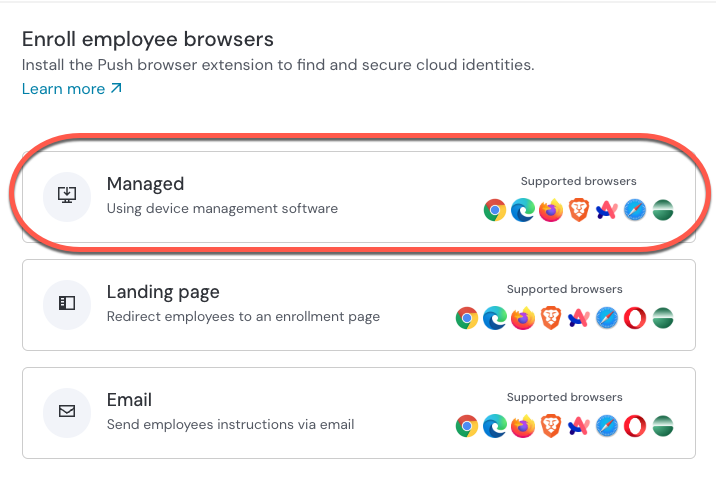
2. Select a Managed enrollment.
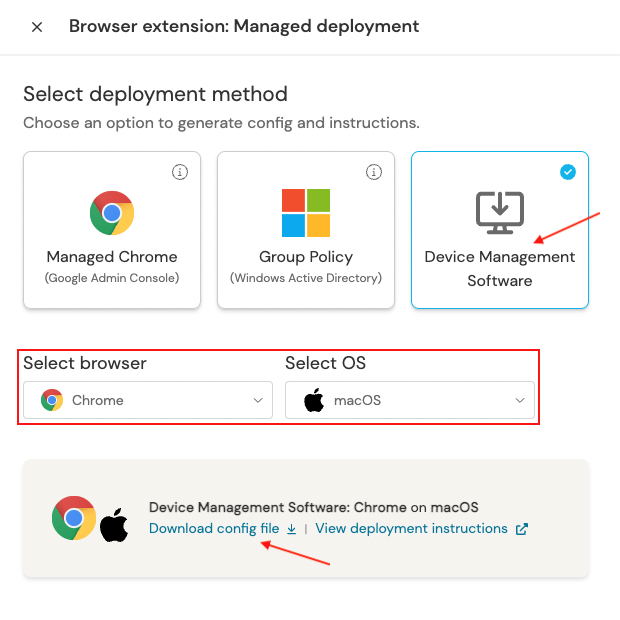
3. Click on Device Management Software, then choose Chrome, Edge, Firefox, Brave, Safari, or Arc as the browser and macOS as the OS. Then select Generate config. This will allow you to download a config file specific to your team.
4. Download and extract the zip file.
Configure your MDM
Instructions for Chrome, Edge, Firefox, Brave, and Arc
Note that Safari requires a few extra steps than other browsers. We'll cover that in the next section. These instructions apply to Chrome, Edge, Firefox, Brave, and Arc.
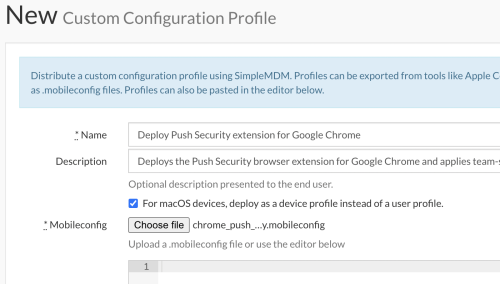
1. In your MDM, create a custom configuration profile and provide a name and description.
2. Provide the config file included in the zip file from the previous step:
chrome_push_security.mobileconfig
edge_push_security.mobileconfig
firefox_push_security.mobileconfig
brave_push_security.mobileconfig
arc_push_security.mobileconfig
3. Once the profile has been created, assign it to a device or group of devices.
When the settings propagate, the Push browser extension will be installed on devices in your organization and automatically enrolled in Push.
Instructions for Safari
Deploying the Push extension to Safari via MDM requires a few additional steps. You'll need to:
Configure the extension token using a configuration profile.
Configure managed Safari extension settings.
Deploy the extension to endpoints using Apple's Volume Purchasing Program (VPP).
Prerequisites: You'll need to use macOS 15 or newer. Apple introduced managed Safari extension settings with macOS 15 (Sequoia). Devices also need to be supervised for the Safari extension settings to apply.
1. Generate a managed deployment configuration file in the Push admin console, as described in step 1 under Generate the configuration profile, above.
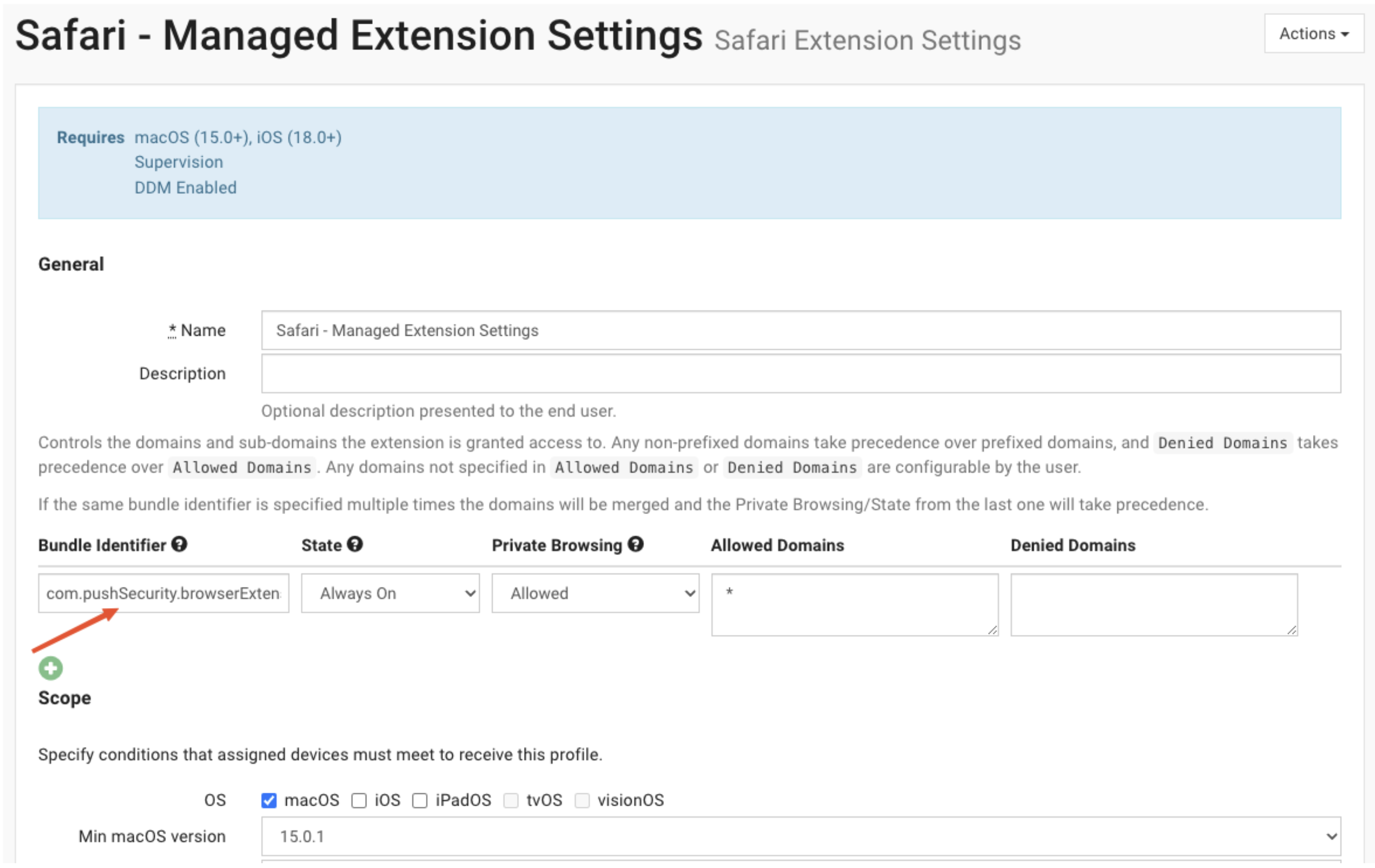
2. Configure the managed Safari extension settings by creating a managed Safari extension settings profile in your MDM. If you already have a profile, you'll need to apply the settings described in this section. This process varies by MDM. Consult your MDM documentation for guidance.
To configure the Push Security extension, you need to provide a bundle identifier and a team identifier. The values you need are:
Bundle identifier: com.pushSecurity.browserExtension.Extension
Team identifier: 834Y38V48U
Your MDM may require this information to be provided as a single string, such as:
com.pushSecurity.browserExtension.Extension (834Y38V48U)Then configure the Allowed Domains setting. We recommend setting it to * (star / asterisk) to ensure full coverage. However, you can specify domains the Push extension should be denied access to, if desired.
Here is an example of what this configuration looks like:
3. Finally, deploy the extension to your endpoints. You'll need to acquire enough licenses using Apple's Volume Purchasing Program (VPP) to cover all the endpoints you're deploying the extension to. VPP is part of Apple Business Manager. These licenses are free and are used merely to deploy the extension. You'll manage your Push platform licenses separately.
Once the licenses have been added to your account and synced to your MDM, you can assign the extensions to be deployed to endpoints. Again, this step varies according to your MDM, so consult your MDM's documentation.
A few common MDM solutions provide the following documentation:
Note: Jamf Pro version 11.15 is required to configure the extension permissions. Refer to the instructions for Jamf Blueprints.