Install the browser extension
Overview
Deploy the Push browser extension to prevent, detect, and block browser-based attacks.
The browser agent detects attack techniques such as AiTM phishing toolkits, malicious copy-paste attacks like ClickFix, cloned login pages, and others.
The browser agent also provides contextual telemetry on all your workforce identities, whether they’re managed by your identity provider or not.
Over time, the extension also provides a full accounting of the cloud apps and accounts your employees are actively using by observing logins that match your configured monitored domains and helping to harden your security posture by surfacing and fixing risks such as:
Compromised passwords
Reused passwords
Shared account credentials
Leaked passwords
Weak passwords
Lack of password manager use
No MFA
What data is collected?
Once installed, the extension sits in the background of your employees’ browsers and collects the following information:
Browser name
Browser version
Device OS
Push browser extension version
The extension enrollment method (via a managed deployment or self-enrollment)
When the extension last checked in
Push only monitors logins that match the company email domains you specify on the Settings page of the Push admin console. You can enable monitoring of all domains used by your employees to access work apps (including personal accounts) if you choose. Ensure you have consent before using this feature. Learn more.
When employees log into SaaS applications using their work account, the extension collects:
The URL of the platform
The account username
The login method
If a password is used, Push generates a shortened salted hash of the password, which is stored locally in the browser and never sent anywhere.
Their MFA registration status and MFA method, for supported apps
Using the shortened salted hash of the password, Push can then perform password comparisons and analysis, such as blocking passwords from being entered on websites that do not belong to the application, or surfacing leaked and shared account credentials. All comparisons are done locally in the browser, not server-side.
If the extension observes an employee visiting an OAuth consent screen for an Microsoft 365 or Google Workspace app integration, it also collects basic telemetry about the integration that Push uses to research the integration, such as establishing whether it has a verified publisher. The data the extension collects in this case is:
The platform the app was observed on
The app identifier
The grant type requested
The reply URL
The scopes requested
If Push observes employee logins for apps it doesn’t recognize as work apps, it collects the URL of the platform and the login method (password or social login).
The extension will also collect data based on your configured security controls, such as when employees visit a blocked URL.
Learn more and see examples of the data collected by the extension in this related help article.
Verify your monitored domains
Push only monitors logins that match the company email domains you specify on the Settings page of the Push admin console. You can enable monitoring of all domains used by your employees to access work apps (including personal accounts) if you choose. Ensure you have consent before using this feature. Learn more.
In addition, the extension will never send passwords anywhere. All password security checks are performed locally in the browser.
If you need to restrict the extension from running on specific websites, you can configure an ignore list in the Advanced tab of the Settings page. Learn more.
Customize extension behavior
In addition to configuring which domains you want to monitor, the behavior of the Push browser extension can be customized in the following ways:
Check for leaked passwords: The extension can connect to an external API, Have I Been Pwned, to identify passwords exposed in a data breach. This setting is enabled by default. You can configure it by going to Settings > Password checks. Learn more.
Define custom words to flag: The extension can check passwords against a list of custom terms you define, such as company names that are often used in weak passwords. You can configure the list of custom words by going to Settings > Password checks. Learn more.
The extension also powers Push’s security controls, including in-browser banners and password guidance, password protection, phishing tool detection, and more.
Learn more about security controls.
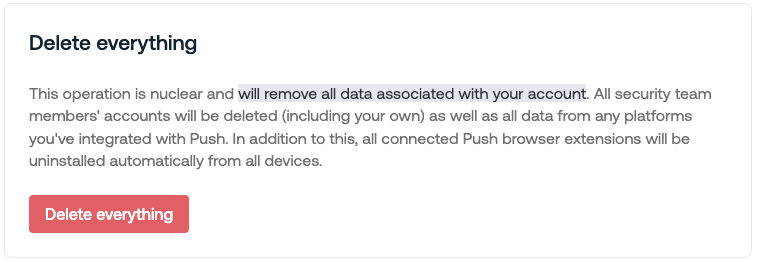
Installation options
There are four ways to install the extension and enroll employee browsers:
Managed: Perform a managed installation to deploy the extension to employee machines using device management software. This is the recommended method.
Email: Allow employees to self-enroll by sending them a link to install the extension via email.
Landing page: Direct employees to a landing page to self-enroll after they confirm their identity by authenticating.
Managed installation
Perform a managed installation of the Push browser extension to add the extension to your employees’ browsers without any action required from them.
Enrolling an employee’s browser in Push via a managed deployment is a two-step process:
First, you install the Push browser extension.
Next, the extension waits for user login activity to help identify the user of the browser and complete enrollment. If you are using the automatic licensing option, Push will also license the identified user and add them as an enrolled employee on the Push platform.
Supported browsers:
Google Chrome
Microsoft Edge
Firefox
Brave
Arc
Island
Prisma Access
Deployment options:
Google Admin Console managed Chrome
Microsoft Group Policy managed Chrome, Edge, and Firefox
Device management software on Windows for Chrome, Edge, Firefox, and Brave. Documented example is for Microsoft Endpoint Manager (Intune).
Device management software on macOS for Chrome, Edge, Firefox, Brave, Arc, and Safari
Prisma Access enterprise browser
Self-enrollment via email
Send instructions to employees via email to install the extension and complete enrollment of their browser in a single step. This process takes about a minute.
Prerequisites: You must complete an integration with your identity provider first in order to sync in employee records and assign licenses to add those users to Push — or add those users manually. Then you’ll be able to send them email self-enrollment links for the browser extension.
Supported browsers:
Google Chrome
Microsoft Edge
Safari
Firefox
Opera
Brave
Arc
Island
Prisma Access
Send enrollment emails:
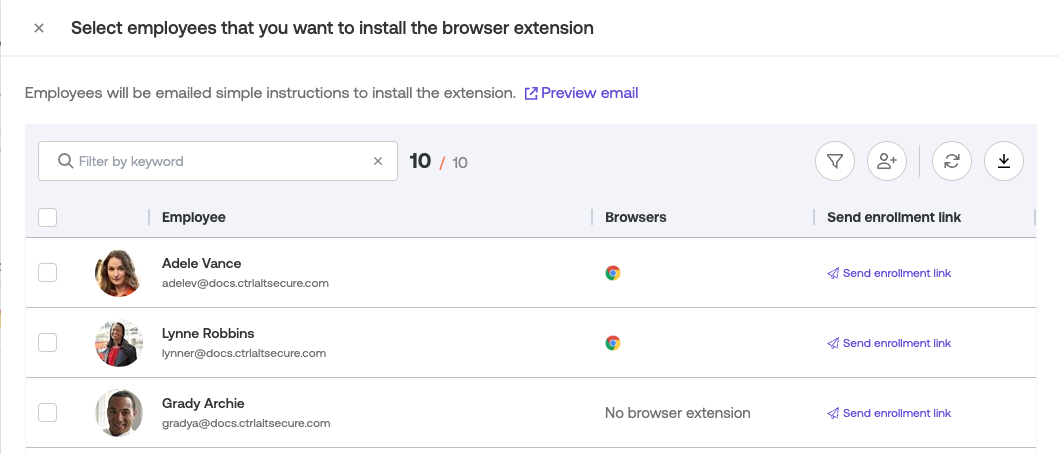
1. Log into the Push admin console.
2. Go to the Browsers page in the left sidebar and then select Manage > Email as the enrollment option.
3. You’ll be taken to a view of all your employees with a license in Push. Select who you’ll send an email enrollment link to. You can also preview the enrollment email on this page by clicking on Preview email.
4. Emails will be sent immediately. To complete installation of the extension, employees should click on the Secure your browser link in the email on each browser they use for work.
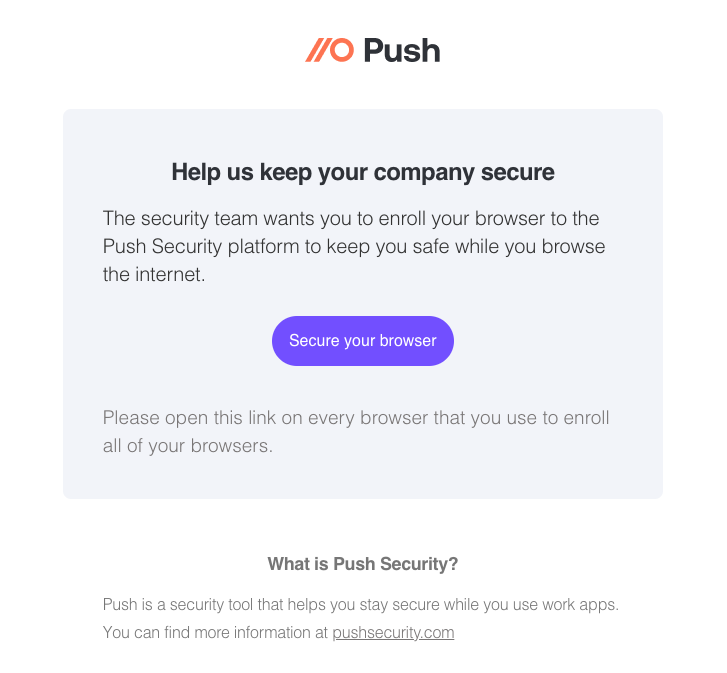
5. The link will take them to the extension installation page for their browser where they can install the extension, completing enrollment of their browser in Push.
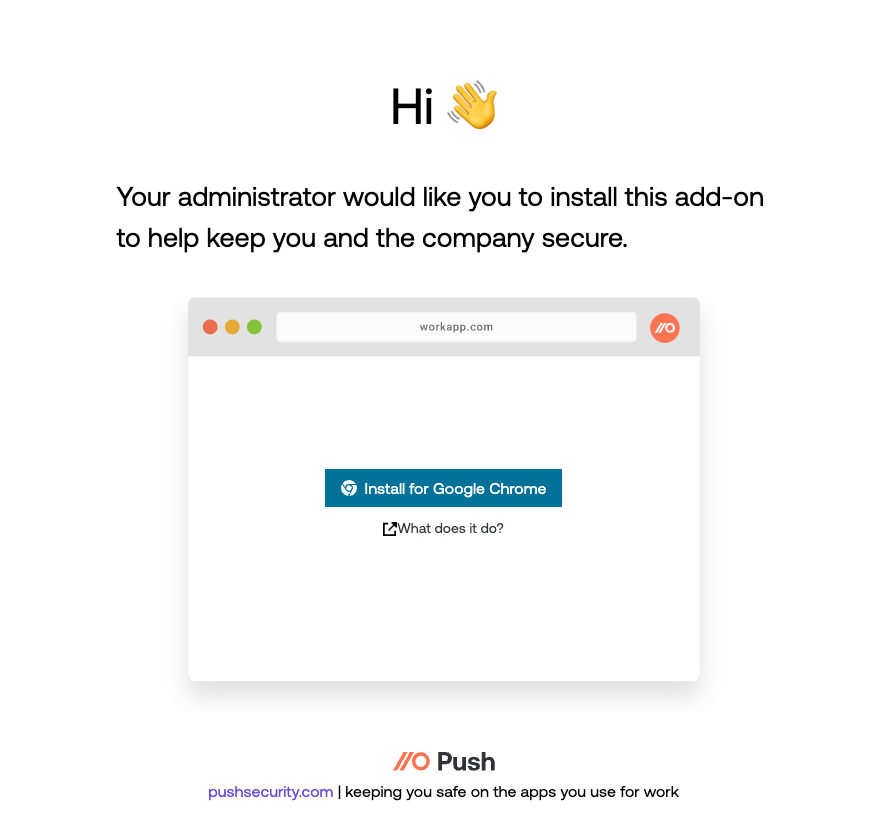
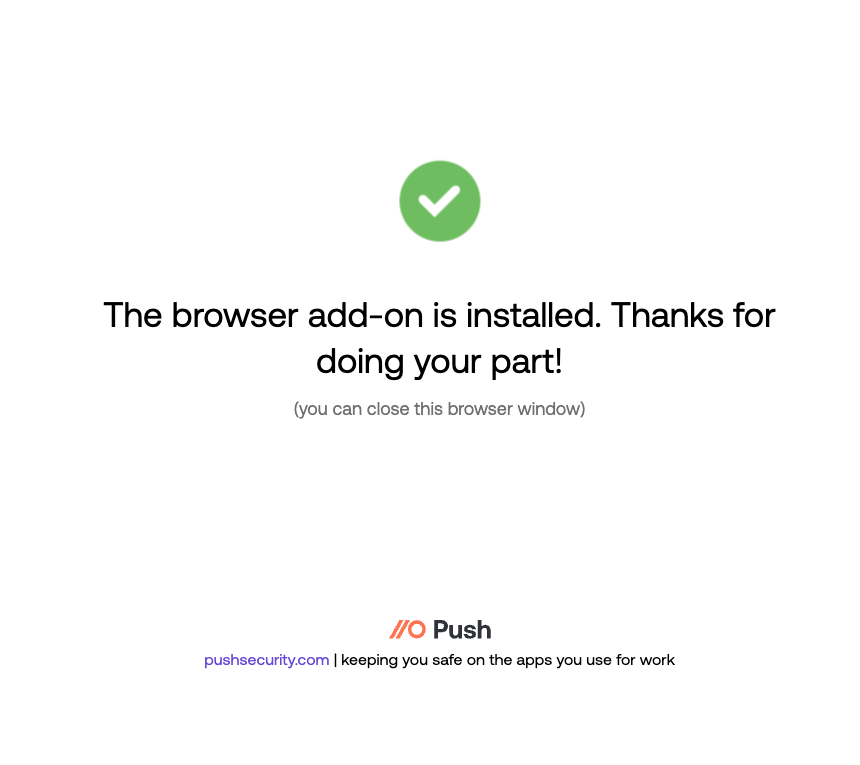
6. After they install the extension, they’ll see a confirmation message.
Self-enrollment via landing page
You can invite employees to self-enroll in Push and install the browser extension themselves by directing them to a unique landing page. Once employees visit the landing page, they will be prompted to authenticate via OIDC using your identity provider in order to confirm their identity. Once confirmed, they will be prompted to install the Push browser extension and enrolled in Push.
Note: You must use Microsoft 365 as your identity provider for this option. In order for employees to be able to self-enroll via the landing page, they must successfully complete an OIDC login using a user principal name (UPN) that includes a domain that matches your Monitored domains on the Settings page in Push. In addition, you must have licenses available in your Push account in order for employees to be automatically enrolled.
Supported browsers:
Google Chrome
Microsoft Edge
Safari
Firefox
Opera
Brave
Arc
Island
To use the enrollment landing page:
1. Log into the Push admin console.
2. Go to the Browsers page and select Manage > Landing page as the enrollment option.
3. Send the unique URL provided on the slideout to the employees you wish to enroll in Push.
4. Once employees visit the URL, they’ll be prompted to verify their identity by performing a Microsoft 365 OIDC authentication.
5. After that, they’ll follow the steps described above to install the Push browser extension.
Version updates
The Push browser extension automatically updates when new versions are released. You do not need to take any action to apply these updates.
Removing the extension
You can temporarily disable the browser extension without needing to uninstall it if you need to do some troubleshooting. On the Settings page, select Advanced and add an ignore list of websites that the extension should not monitor. You can also disable the extension on all sites by entering an * (asterisk or star character) in the ignore list. Learn more.
If you want to remove the browser extension, you have two options:
For self-enrolled extensions completed via email or landing page by the employee, the employee will need to manually delete the extension from their browser. Removing the extension this way does not delete their activity data from the Push admin console. If you wish to delete their activity data, you can revoke their account license. This will remove all their data from the Push platform, including data collected via API integrations and the browser extension. Note: If you delete your team on the Settings page of the admin console, this will cause all these browser extensions to unenroll and delete themselves.
For extensions installed via a managed deployment, you can use your device management software to remove the extension. Depending on the software, this method may remove the extension without deleting it on the Push side. In that case, the browser will still be associated with the employee record and will still appear in the admin console. It will expire and be removed after 90 days, which is the usual inactivity period for browsers. Note: If you delete your team on the Settings page of the admin console, this will also cause all these browser extensions to unenroll. You will need to remove the extension from your managed policy in order to delete the extension from managed browsers.
You can also unenroll a given browser profile for an employee by going to the Browsers page and finding the browser profile for a given employee that you want to remove. Select the trash icon for that browser profile under the Action column in the table to unenroll the extension from that profile.
Note that deleting a company domain from your Settings page will not remove or unenroll the extension. The domain setting only controls what data the extension monitors.
The Delete everything feature also deletes all your data.