Getting started
Overview
Push Security is a browser-based detection and response platform that stops adversary-in-the-middle (AiTM) phishing, malicious copy-paste attacks like ClickFix, malicious browser extensions, and other modern browser-based attacks that lead to account takeover, ransomware, and infostealer malware.
Push uses an agent deployed as an extension to employee browsers to perform real-time on-page analysis that provides full context of both user and attacker behavior, stopping attacks early in the killchain.
Stream Push telemetry to your SIEM, SOAR, or other automation platform to investigate potential threats, correlate with additional log sources, or automate response actions.
In addition to its detection and response capabilities in the browser, Push also provides full visibility of your attack surface of corporate identities, apps and accounts. With this information, you can:
Proactively enforce end-user security controls that reduce the risk of account takeover, malware delivery, and endpoint compromise.
Map and monitor your attack surface by observing all logins to managed and unmanaged apps, including local password accounts, non-SSO apps, free-tier apps, and other shadow IT.
Uncover and automatically harden vulnerable workforce identities, including those using stolen, leaked, weak, or reused credentials; password logins instead of SSO; and accounts without MFA.
Get visibility of all browser extensions in use across your workforce, and block malicious or unwanted extensions.
See all AI tools in use across your workforce and enforce AI usage rules directly in the browser.
Key features
Browser extension: Push is deployed as a browser extension using an MDM, Google Admin console, Microsoft Group Policy, or manual enrollment. This agent detects and responds to browser-based attacks using readymade controls, and also observes employee logins and signups to cloud accounts using federated and unfederated identities. Using this telemetry, the extension enforces your configured controls, raises detections, guides end-users to self-remediate issues, and provides inventories of your workforce apps, accounts, and browser extensions.
Identity provider integration: You can also integrate Push via API with your identity provider to sync data on employees, SSO-supported apps, third-party OAuth integrations, and OIDC logins.
API / webhooks: Integrate Push’s browser telemetry into your existing tools such as SIEM, SOAR, XDR, automation, and case management platforms using the Push REST API and webhooks.
Admin console: Administrators can configure and manage the Push platform through an admin console, which provides a dashboard for reporting, a table of detected security events for quick triage, as well as detailed inventories for all your apps, accounts, OAuth integrations, browser extensions, and employees and their associated security findings.
Chat platform integration: Receive real-time notifications in Slack or Microsoft Teams of new detections, new security findings, newly discovered apps and accounts.
Where to begin
The following steps apply to new administrators of Push. If you use Push as an employee end-user, refer to our employee documentation for help.
Setting up Push takes about 10 minutes. Complete your setup with these four steps:
1. Install the Push browser extension on employee browsers. You can deploy the extension silently to selected groups using an MDM and automatically license employees to enroll them in Push. The extension supports all major browsers, including Chrome, Edge, Firefox, Opera, Safari, Brave, Arc, Island, and Prisma Access.
2. Configure Push’s security controls. Block modern browser-based attacks like AiTM phishkits, ClickFix, malicious browser extensions, and others; then enable employee guardrails to guide users to self-remediate account security vulnerabilities and to correctly adhere to app usage policies.
3. Integrate with your identity provider to enrich the data provided by the extension and to provide a view into SSO apps, third-party OAuth integrations, and MFA usage on your core platform. You can also sync employees to Push using this integration and manually assign licenses if you prefer. Push integrates via API with Microsoft 365, Google Workspace, and Okta.
4. Turn on real-time notifications for your security team using Push’s ChatOps feature to send alerts on detections, security findings and changes to your app and account attack surface.
You’ll see some data immediately after completing a setup task. Other data will populate as your employees log into apps. Here’s what to expect as a new administrator on the Push platform:
The browser extension observes real-time activity. You’ll see inventories for employee accounts and apps when logins are observed.
The identity provider integration will immediately import third-party OAuth integrations and MFA usage data, as well as employee records if you are licensing employees via the IdP integration. If integrating with Okta, you’ll also see a list of apps behind SSO. After the initial integration, Push checks once an hour to update this data in the Push admin console.
When you’re ready, integrate Push with your existing security and IT tooling, such as SIEM, SOAR, or other automation platforms, and create your own custom detections and response actions.
Initial login
Once your Push tenant is provisioned, you can access your Push admin console.
We recommend you use a Microsoft 365 or Google Workspace social login when signing up to use Push, or use multi-factor authentication (MFA) protection for your administrator account if you are using a username and password.
You can also configure SAML authentication for the admin console. Go to Settings > SAML configuration to get started.
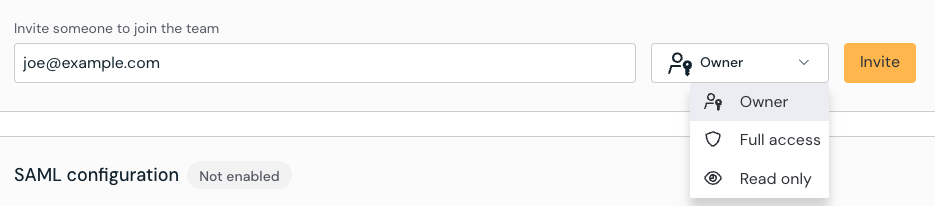
Inviting administrators
Push will assign the Owner role to the first signed-up admin on a given team (e.g. tenant). There must be at least one Owner role assigned per tenant; you will not be able to remove the only Owner in your organization without adding a new one.
To invite other administrators to the admin console, go to Settings > Organization to send an invitation via email. When you invite a new admin, you’ll need to set their role: Owner, Full access, or Read only.
Only Owners can edit roles, delete your team (e.g. tenant), change default SAML roles, or update your team name.
Full access admins have full access to the Push console and can make configuration changes to controls or other features not limited solely to Owners.
Read-only admins can only view the Push console and cannot make any changes.
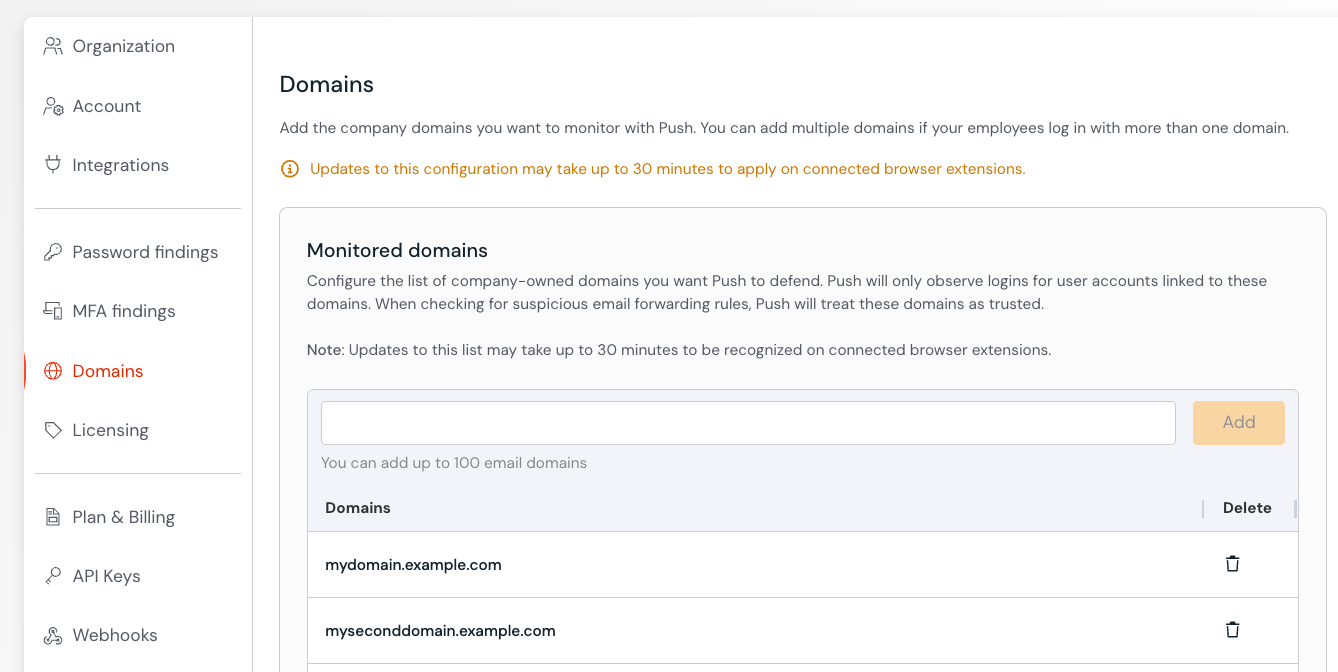
Enter your company domains
When creating your inventories of apps, accounts, and browser extensions, you can configure Push to monitor for either:
Your specified company-owned domains only.
All domains used by employees to access work apps, including personal accounts.
By default, Push does not monitor for logins by personal accounts.
Company domain logins to any apps that Push does not recognize as work apps appear in a separate list in the Push admin console for investigation. If you find apps you use for work in this list, request support for them by contacting the Push team.
To configure your monitored domains, go to Settings > Domains.
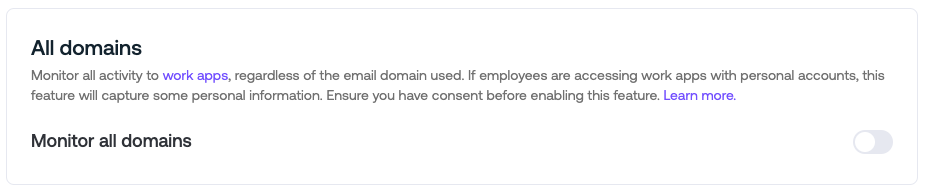
All domains option: If you wish to monitor all activity for work apps used in your environment, regardless of the email domain used, you can enable monitoring of all domains. Ensure you have consent before enabling this feature. Learn more.
Privacy and security
The sole reason Push exists is to improve security, so protecting your personal data is a top priority. We make considerable efforts to secure your personal information and we aim for full transparency on how we gather and use your personal information within our service.
Refer to our privacy policy for more details.
API and webhooks
Push provides a REST API to programmatically administer the platform, as well as webhooks to support real-time updates for platform events. Refer to our developer documentation for details.
Help
We’re always happy to hear from customers and are here to help. To find answers yourself, check out our Help Center articles. Or contact us to talk to a human.