Connect to SIEM or SOAR
Overview
Send Push telemetry to external systems to create custom detections, correlations, and automations using a SIEM, SOAR, or other workflow tool.
You can use this data to:
Investigate phishing and account compromise incidents.
Harden identities and reduce account compromise, such as alerting you when passwords are identified in public data breaches or when employees are using an unapproved app or when an SSO app is accessed via local account.
Monitor for suspicious activity or high-risk changes, such as checking for MFA method changes, or flagging when employees reuse corporate passwords or visit sites running phishing malware.
Investigate indicators of compromise, such as correlating login events with platform logs, searching for recent signups to risky apps, or identifying post-compromise lateral movement opportunities.
Automate a workflow showing you all the accounts and apps used by an offboarded employee, and their account login methods.
Automate a workflow to revoke licenses on SaaS after a period of inactivity, saving money.
Build an approved apps list in your company wiki, synced from Push’s source of truth.
Force-reset an IdP password if Push finds a compromised password on an employee account.
Note: Push already provides preconfigured detections and security controls you can enable directly from the Controls page in the Push admin console. This section of documentation focuses on how to extend these capabilities using external integrations for detection and automation.
Using the Events page
The Events page in the Push admin console provides a rolling 7-day snapshot of all the events generated in your environment. You can use the Events page to help you understand event attributes and gauge event volume before sending events to a third-party tool.
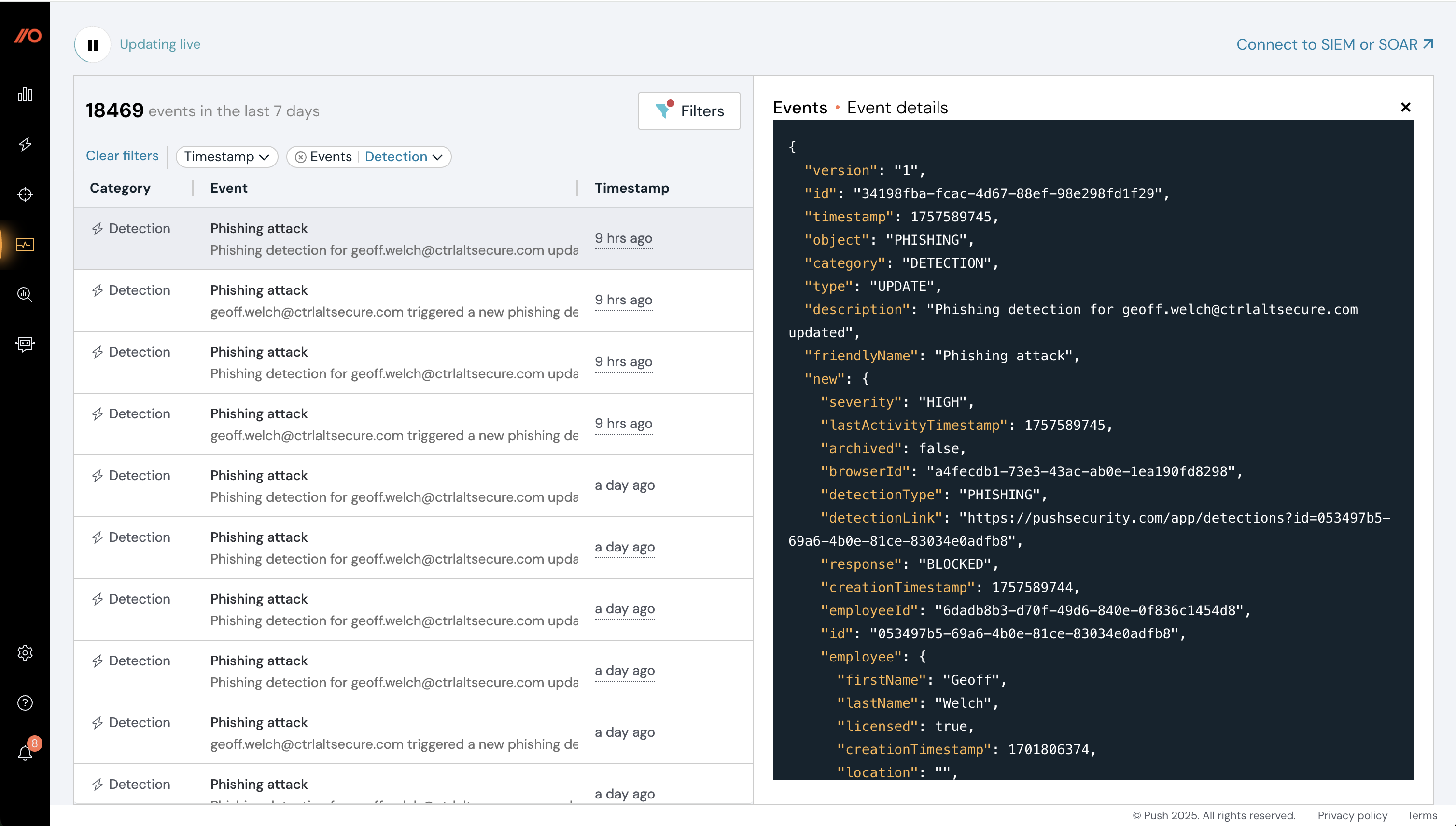
Click on an event on the left to view event details. You can also use the filter icon in the top right corner of the event list to filter by specific event types. You can filter events by timestamp, event type, and entity type (for example, you can view all events for a given employee).
Generic setup steps for SIEM or SOAR
Send Push events to your SIEM or SOAR by setting up a webhook receiver log type that will provide you with a webhook destination URL.
Note: This method works only if your SIEM supports ingestion where the authentication method is “none.”
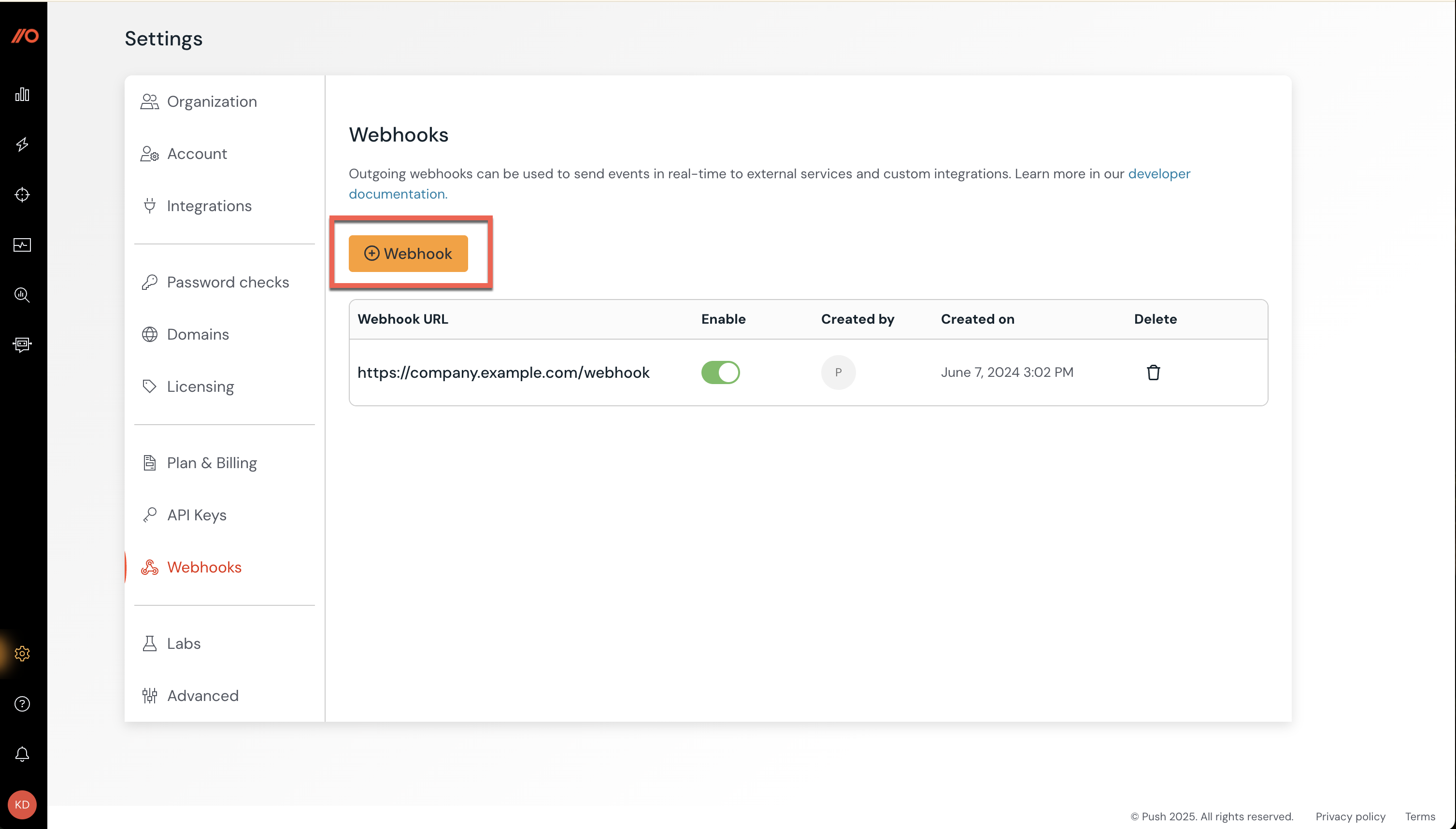
1. In the Push admin console, select Settings in the left navigation.
2. Go to the Webhooks tab and click the +Webhook button.
3. In the URL field, input the webhook destination URL provided by your SIEM, then click Generate Webhook in Push. Optionally, configure custom headers and select which events to send.
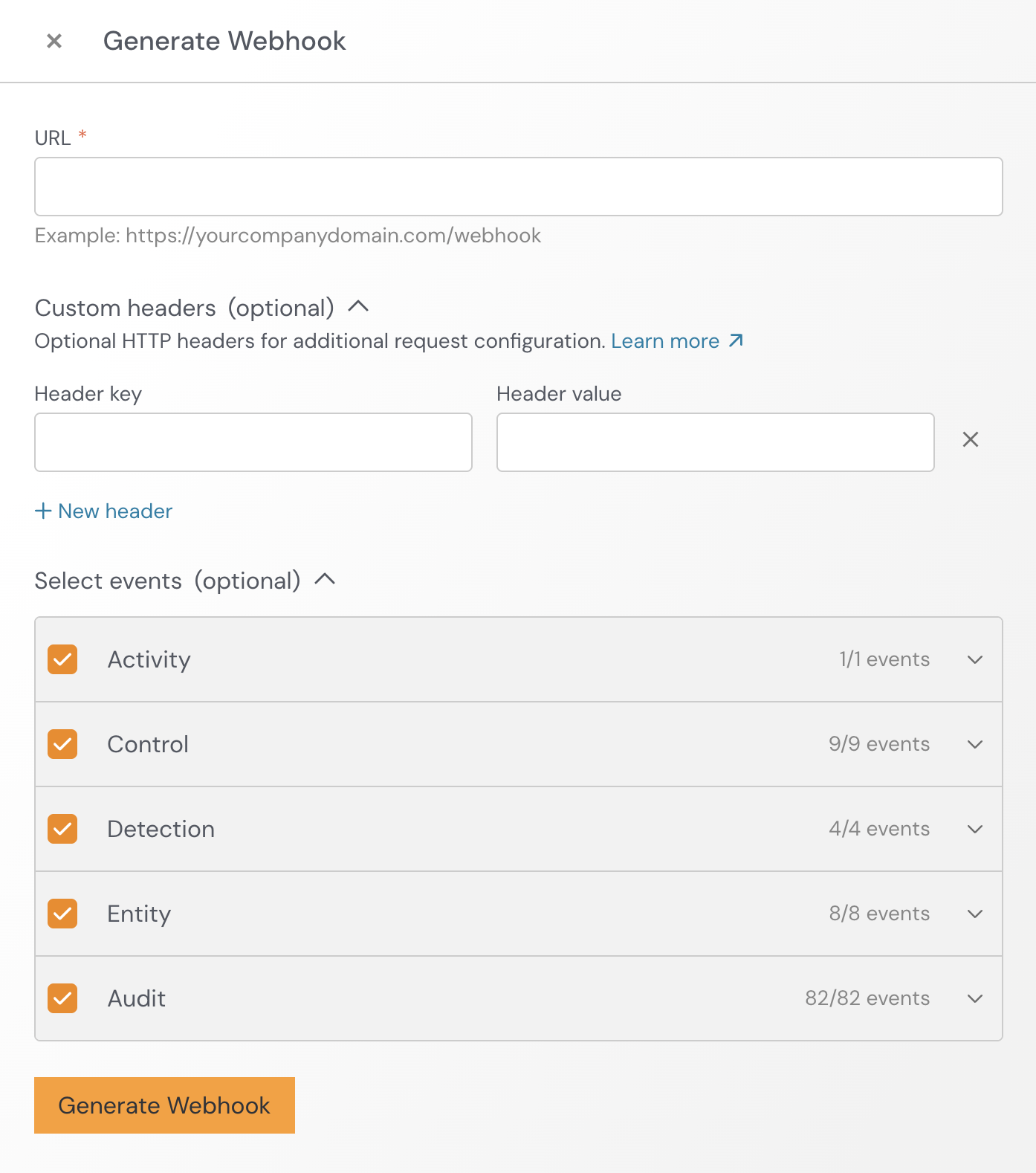
4. Important! Save your webhook secret key in a safe place to refer to later if needed.
5. Once you select Generate Webhook, Push will provide you with a webhook secret key. While this is not part of the example, you can use it to perform signature verification in webhook events.
After completing these steps, Push will start sending webhook events generated by user activities. You can also generate events for testing purposes by logging out and back into apps, or interacting with Push security controls configured via the Push admin console.
You can view the webhook events generated by Push in our webhooks documentation.
What IP ranges does Push use?
Push uses the EC2 AWS public IP range for eu-west-1. We recommend that rather than allowlisting specific IP addresses, you implement signature verification.
Platform-specific setup steps for SIEM and SOAR
Find instructions for specific SIEM platforms below. If you have a request for documentation for a specific SIEM platform, let us know.
Use Microsoft Sentinel SIEM
Send Push logs to your Microsoft Sentinel SIEM using Sentinel and Azure Monitor.
Find step-by-step instructions in our Sentinel documentation.
Use Panther SIEM
Ingest Push logs into Panther. Find step-by-step instructions in our Panther documentation.
Use Datadog SIEM
Ingest events into Datadog. Find step-by-step instructions in our Datadog documentation.
Use Cribl Cloud
Ingest events into Cribl Cloud. Find step-by-step instructions in our Cribl Cloud documentation.
Use Splunk Cloud
Ingest events into Splunk Cloud. Find step-by-step instructions in our Splunk Cloud documentation.
Use Tines
Ingest events into Tines. Find step-by-step instructions in our Tines documentation.
Send alerts directly to Slack
If you don’t have a SIEM, you can use Push’s webhook events to send alerts directly to Slack or other chat platform.
Review our webhooks documentation for a list of events.
We recommend that you gauge event volume by monitoring the Events page in the admin console for several days. Push does not currently provide a method for ingesting only specific events via webhook.
Find step-by-step instructions in our Slack webhook documentation.