Administering Push
Overview
Administer Push using the admin console available at https://pushsecurity.com/app/.
From the admin console, you can monitor and investigate detections, add and manage users and administrators, configure security controls and platform settings, complete integrations, and view a dashboard and other data on your employees, apps, and accounts.
You can also programmatically administer most features of Push using the Push REST API. To share Push data with other systems, such as SIEM / SOAR, compliance platforms, or ticketing systems, use Push’s webhooks.
Navigation
Dashboard
The Dashboard provides a snapshot of your detections, identities and security findings, as well as important trends across your deployment.
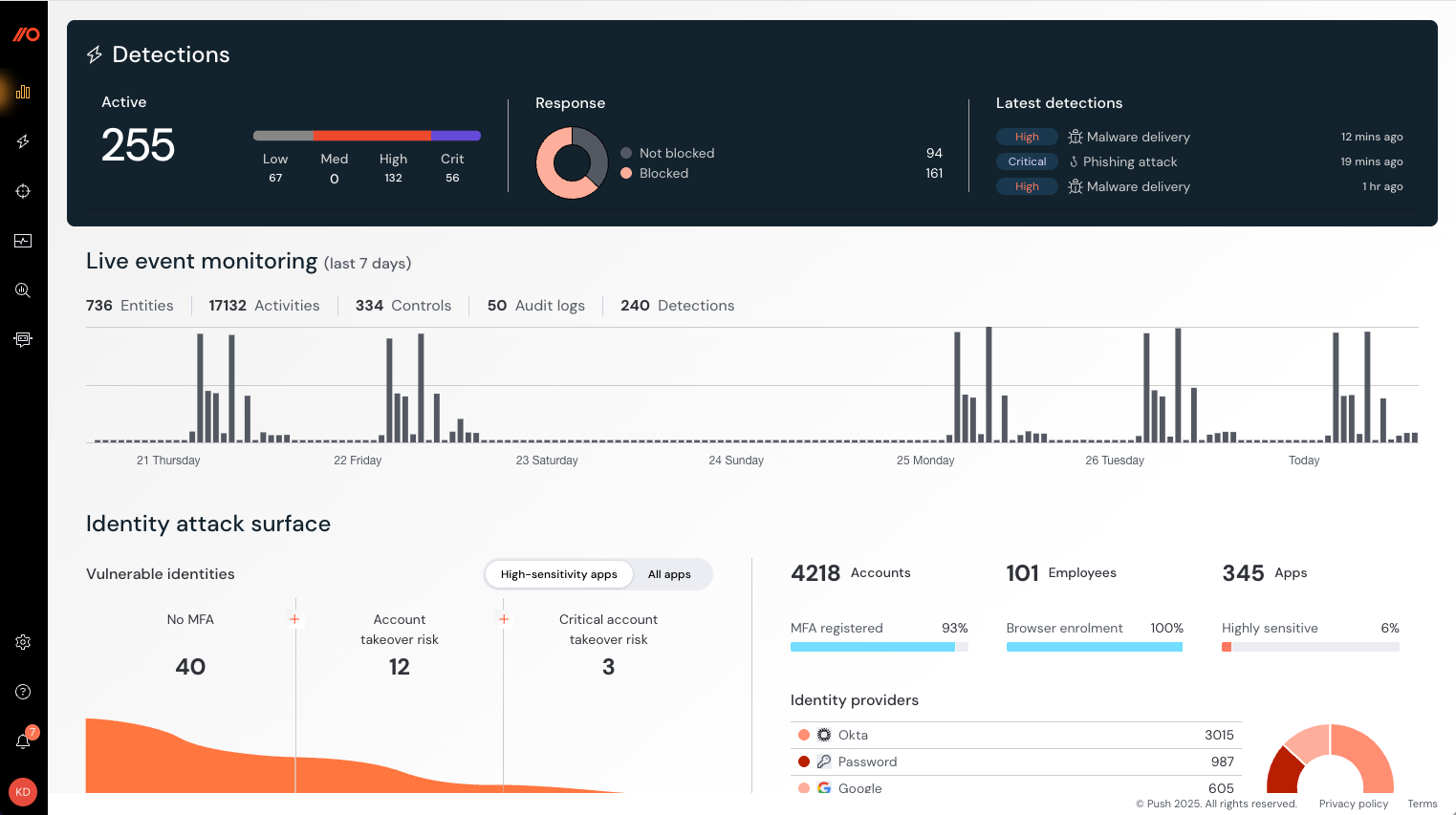
Using the Dashboard, you can see:
Your detections: What Push has detected in terms of phishing attacks, stolen credentials, etc., as well as the response.
Live event monitoring: A snapshot of recent events on the Push platform. See more detail about these on the Events page, or send events to your SIEM.
Your identity attack surface: The accounts, employees, and apps observed by Push, including trends on identity provider usage, MFA registration status across the workforce, login methods trends, browser extension enrollment percentage, app classification, etc.
Vulnerable identities: High-importance security findings, including accounts at critical risk of account takeover because they have stolen credentials in use and no MFA; accounts with no MFA and a weak, leaked, reused, or stolen password; and accounts that lack MFA.
SSO trends: The last 3 months of data on SSO usage (non-SSO vs. SAML vs. OIDC) across all your accounts.
Manage apps: Highlighted findings from your app estate, including high-sensitivity apps with security findings; new apps discovered in the last 30 days; other apps accessed using work identity, etc.
Security findings: An overview of the security findings that have been opened and closed in the last 30 days.
Click into each section to view the underlying data or export it to CSV or JSON.
Detections
Use the Detections page to view detected events, such as suspected phishing or stolen credentials, and their associated telemetry.
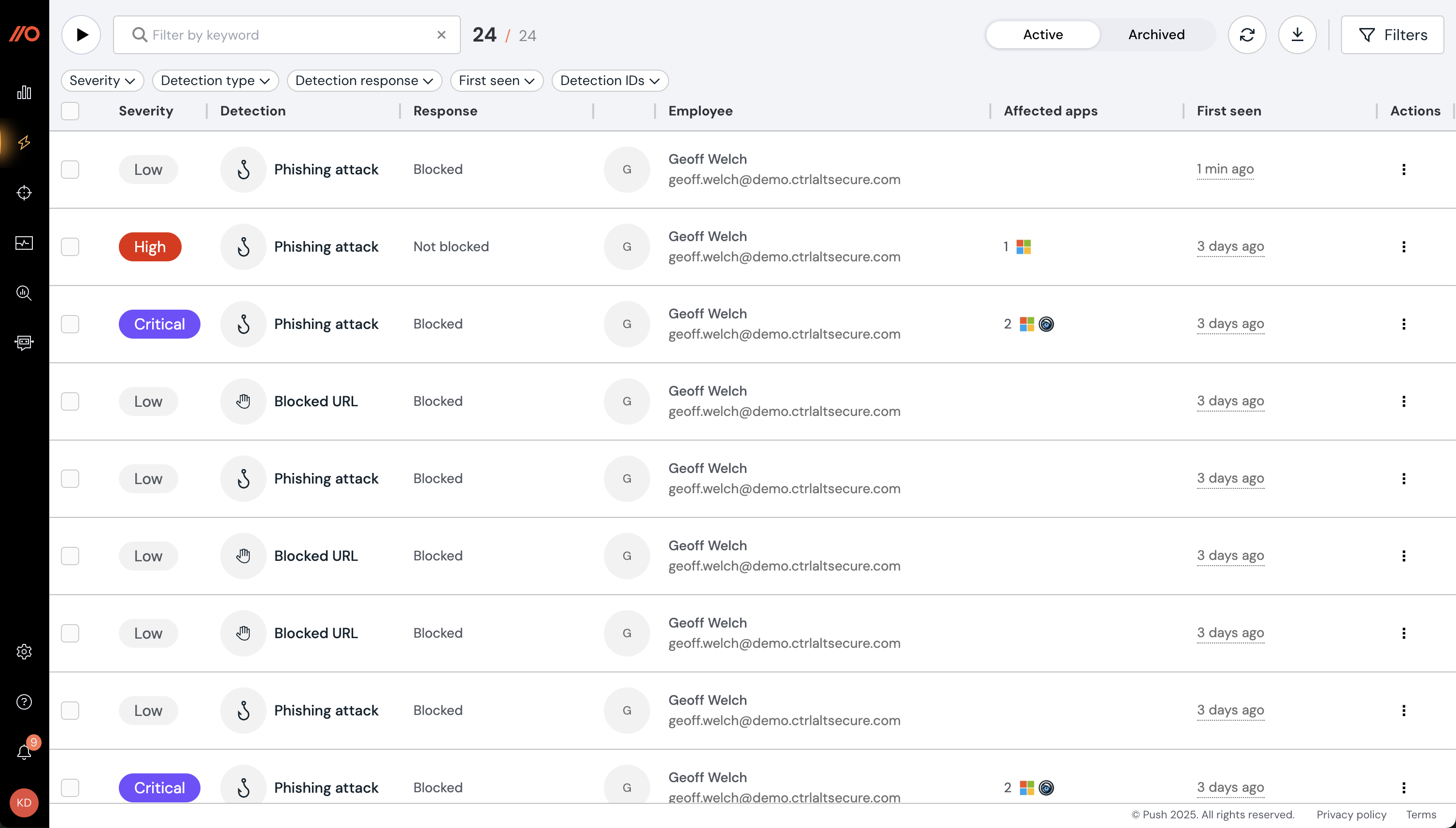
Using the Detections page, you can:
Review and triage detected events, including phishing events, blocked URLs, and stolen credentials.
View additional telemetry about an event, including a timeline of events, screenshots (if enabled), timestamps, detection URLs, referrers, the type of phishkit detected, and what was the response (e.g. blocked).
Share or archive detections.
Filter the list of detections by severity, type, detection response, first seen, or detection ID.
Classify detections to record the outcome of an investigation.
Export the data to CSV or JSON.
Detections can also be consumed via API and webhooks or via Slack or Microsoft Teams by enabling the corresponding security team ChatOps topic.
For a description of how Push assigns a severity level to detections, refer to this help article.
Controls
Use the Controls page to enable and configure security controls, including:
URL blocking: Block access to malicious or unwanted websites and display a customizable block page.
Password protection: Warn against or block when employees reuse important passwords and protect against phishing attacks.
Phishing tool detection: Detect when your employees visit malicious sites containing phishing tools.
Session token theft detection: Inject a unique marker into the User Agent string of sessions to help identify session token theft.
Cloned login page detection: Monitor for cloned login pages designed to steal important credentials, such as SSO passwords.
App banners: Guide employees to securely use apps, selecting from a range of modes, from informing to blocking.
Stolen credential detection: Check if stolen credentials that were posted on the dark web match the ones that employees are using in their browsers.
MFA enforcement: Guide employees to set up MFA on apps where they lack it.
Strong password enforcement: Guide employees to update an insecure password.
Malicious copy and paste detection: Detect the delivery of malware to the host that uses copy-paste techniques like ClickFix or FileFix.
Browser extension blocking: Block malicious or unwanted extensions, or create an allowlist for only allowed extensions in your environment.
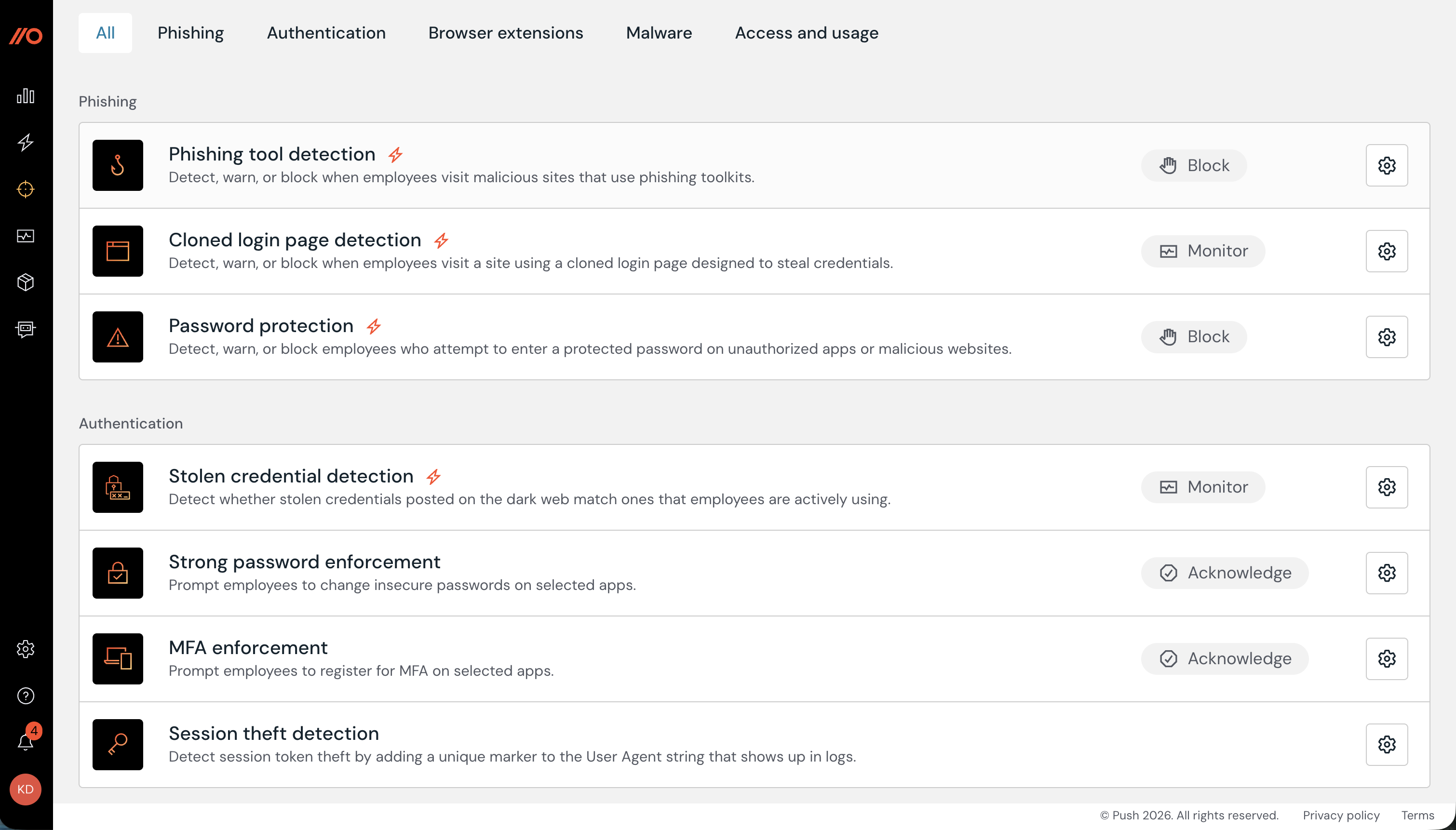
Learn more about security controls.
Events
The Events page provides a rolling 7-day snapshot of all the events generated in your environment. You can use the Events page to help you understand event attributes and gauge event volume before sending events to a third-party tool.
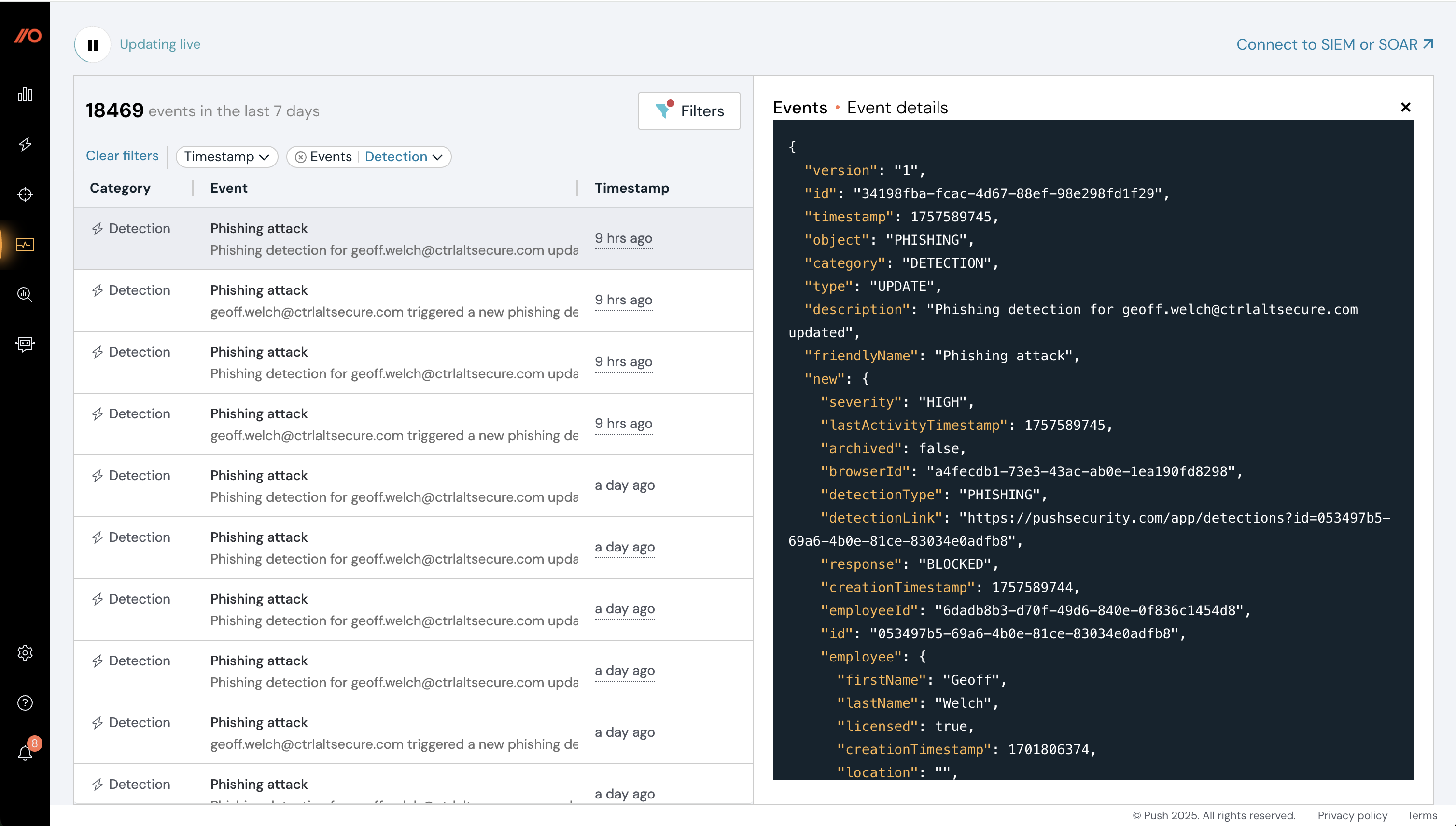
Learn more about the Events page and how to send Push data to third-party solutions such as a SIEM or SOAR.
Employees, Apps, Accounts, Browsers, Browser extensions, OAuth apps, and Mail rules
In these sections, under Inventory, you can view detailed data tables for all the objects monitored by Push:
Employees: View enrolled employees and see an overview of their accounts and security findings.
Apps: View all apps discovered by Push, the login methods used to access them, and security findings. Classify apps according to their approval status and sensitivity level.
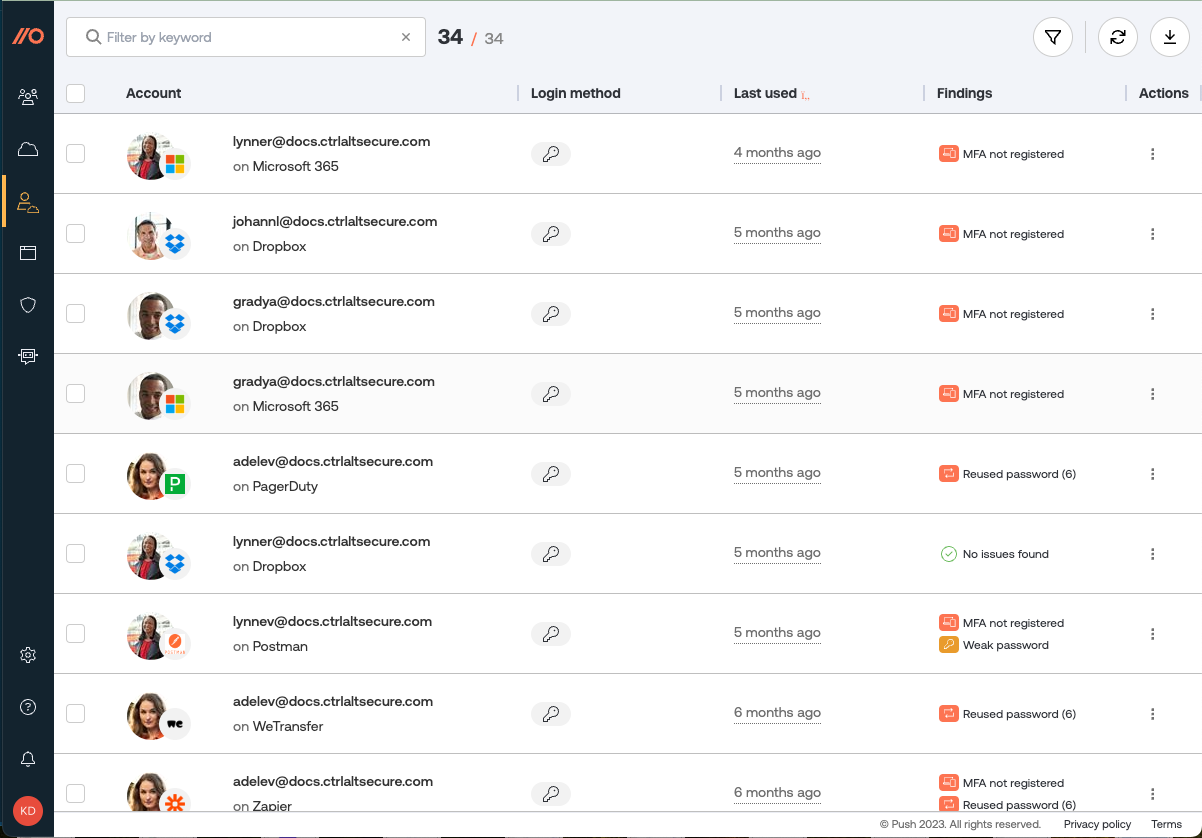
Accounts: View all individual accounts used by enrolled employees, their login methods and identity providers, and their security findings.
Browsers: View all enrolled browser profiles and view an employee’s extension version, OS, and deployment method.
Browser extensions: View all the browser extensions installed across your environment, their installation method, permissions, and who's using them.
OAuth apps: See and manage the third-party OAuth integrations connected to your synced identity provider platform. View permissions they’ve been granted, and delete integrations you do not trust.
Mail rules: Identity mail rules in employee inboxes that forward messages to non-company domains, a potential indicator of suspicious activity.
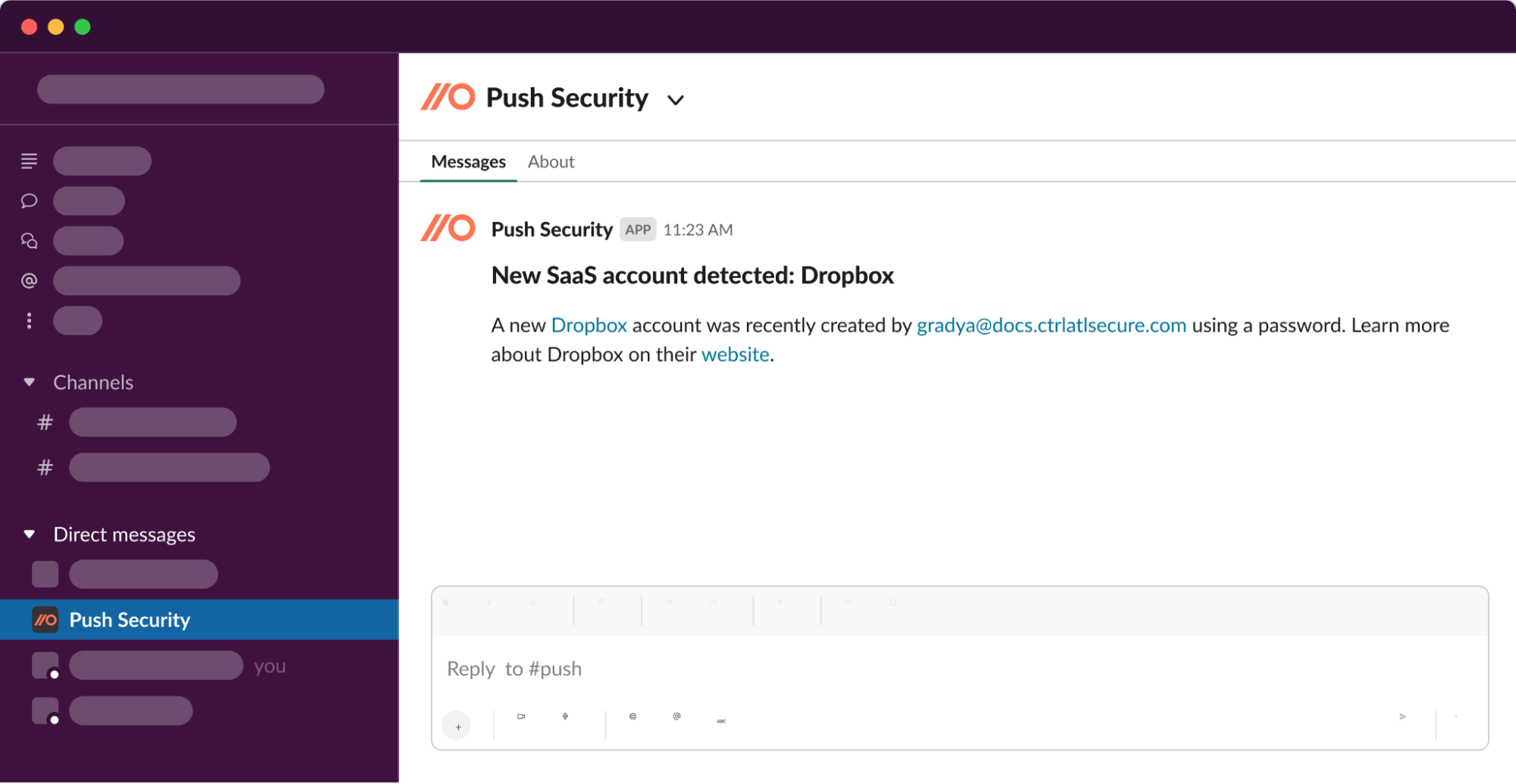
ChatOps
Integrate with Slack or Microsoft Teams to set up real-time notifications for your security team channel when Push observes detections, security findings, or new apps, accounts, and third-party integrations in your environment.
Settings
View and configure the settings for your Push tenant on the Settings page.
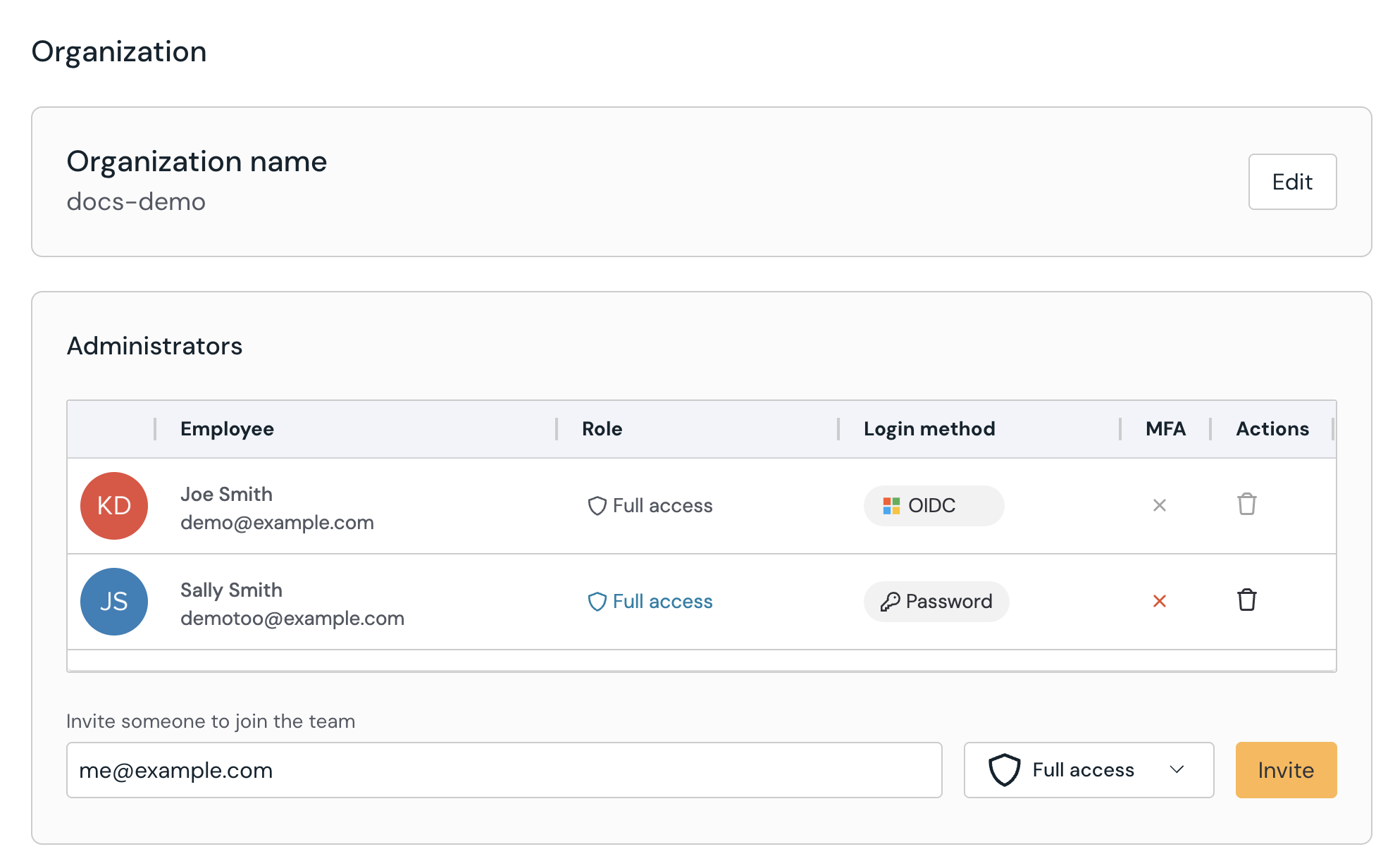
Organization
Edit your organization (tenant) name, add or remove Push administrators, and delete all data associated with your Push tenant. You can also configure SAML here, and assign role-based access to administrators.
Account
Manage your Push administrator account, including enabling MFA and email or desktop notifications for changes to your Push tenant, such as adding a new admin.
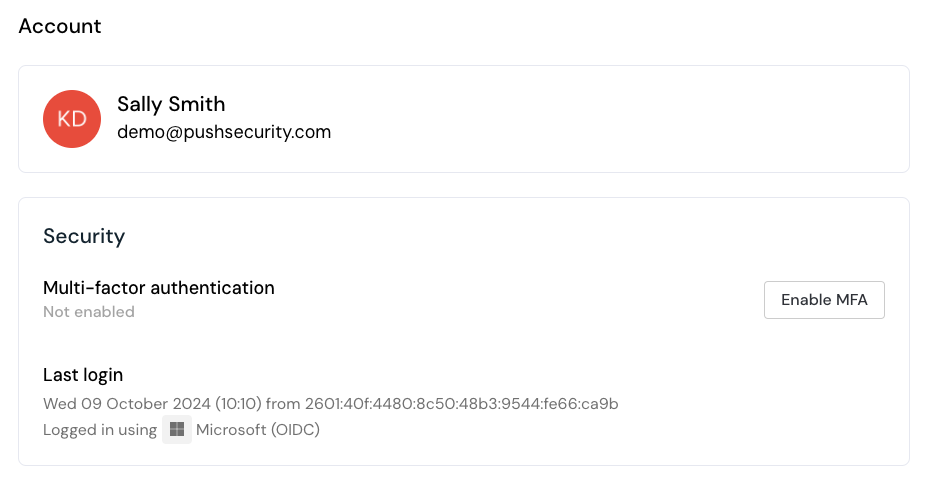
You can also delete your administrator account from this tab.
Integrations
View the integrations connected to the Push platform, and add or remove them.
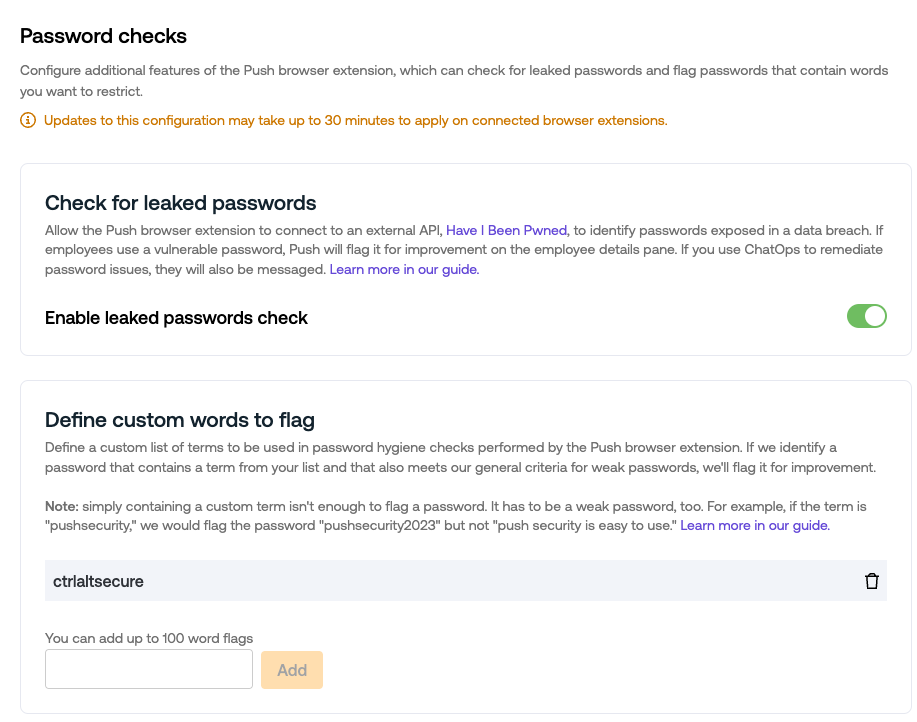
Password checks
Configure how the Push browser extension performs additional security checks for password logins. You can enable Push to check for leaked passwords or define custom words to flag when they are used in weak passwords, such as company names and terms.
Domains
Configure the list of company-owned domains you want Push to defend. The Push browser extension will observe logins and signups for user accounts linked to these domains. When checking for suspicious email forwarding rules, Push will treat these domains as trusted.
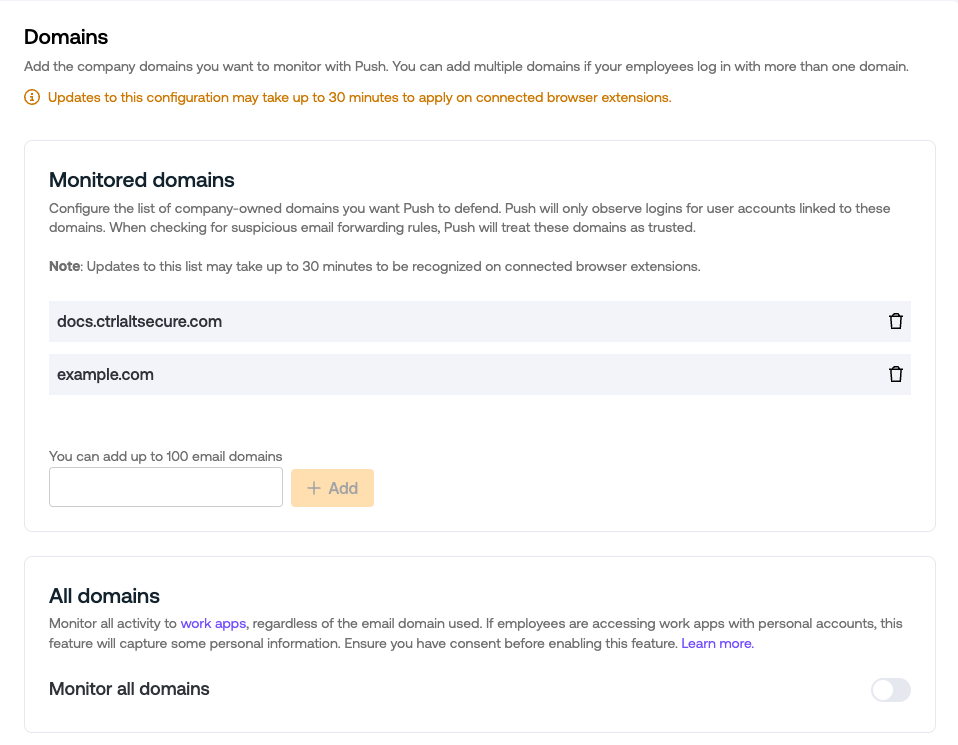
All domains option: If you wish to monitor all activity for work apps used in your environment, regardless of the email domain used, you can enable monitoring of all domains. Ensure you have consent before enabling this feature. Learn more.
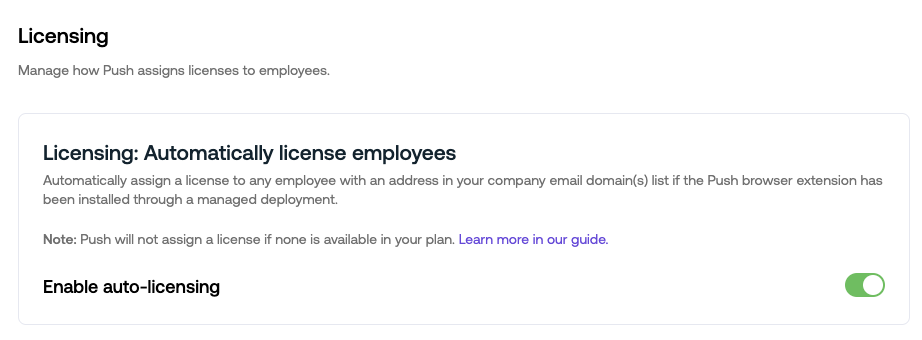
Licensing
Enable auto-licensing to allow Push to automatically assign a license to any employee with an address in your company email domain(s) list if the browser extension has been installed through a managed deployment.
Plan & Billing
Push is billed on a per-license basis. Licenses are assigned to individual humans, not number of accounts. You can manage your billing plan or buy more licenses from the Plan & Billing section.
API Keys
Add and manage API keys from this section. API keys are used to interact with the Push REST API and share your Push data with other platforms. Learn more about the Push API.
Webhooks
Add and manage webhooks from this section. Outgoing webhooks can be used to send Push events in real time to external services and custom integrations. Learn more about Push webhooks.
Advanced
Configure advanced settings, including an exclude list for websites that the Push extension should not monitor. More about excluding websites from monitoring. On this tab, you can also add custom login URLs for your identity provider or other apps that use a custom login URL so that Push can detect and defend them.
Admin audit events
Get visibility of actions taken by administrators on the Push platform using admin audit events, such as:
Admin enabled MFA
API key added or removed
Security controls configured
License added or removed
And more
View recent events on the Events page by filtering by the event category of Audit.
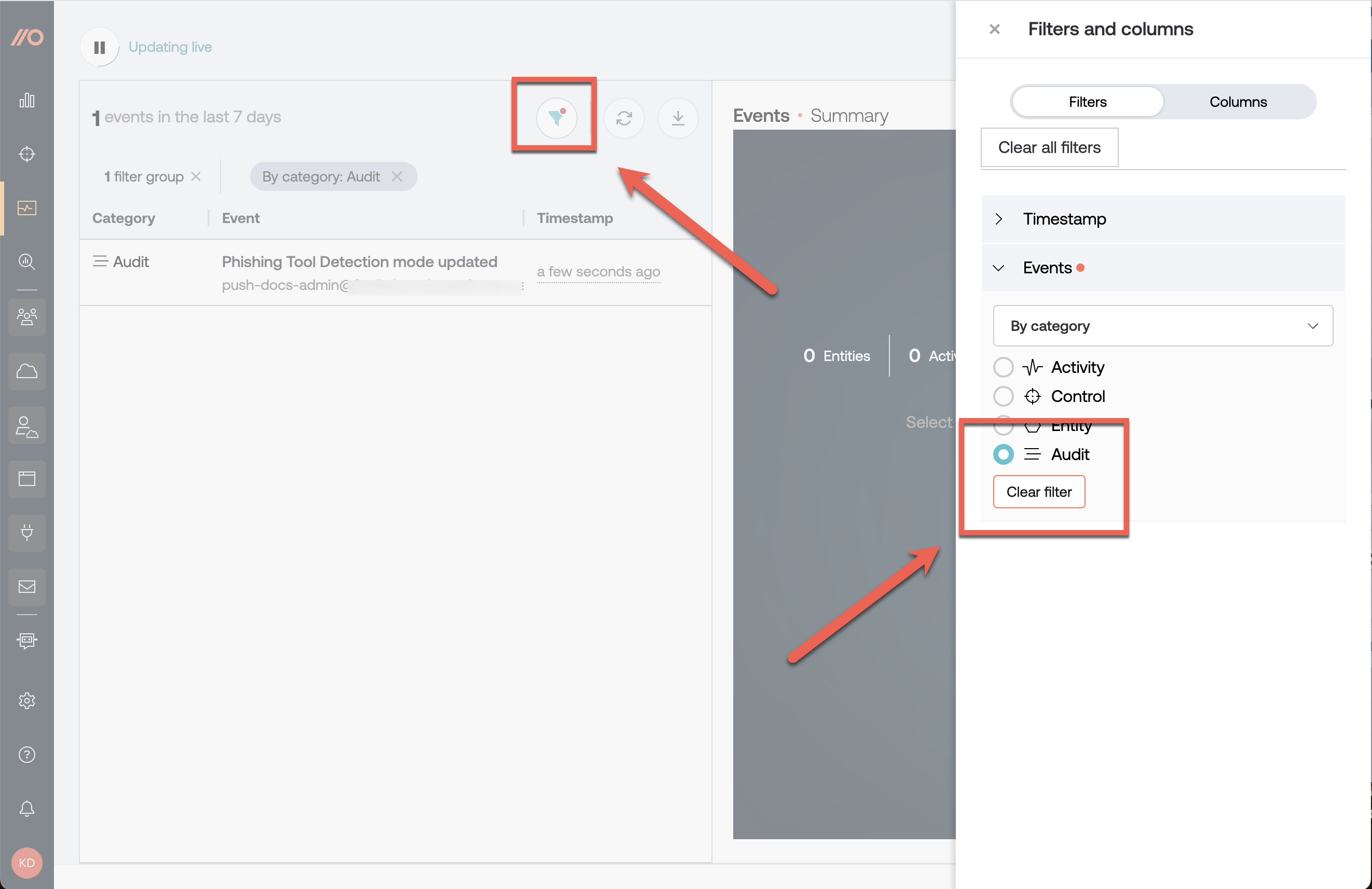
To consume an ongoing log of admin events, use Push’s webhooks.
Extended admin audit logging
If you wish to enable more verbose admin audit logging, enable Extended admin audit logging in the Push admin console by going to Settings > Advanced > Extended admin audit logging.
This extended logging will emit an event each time an admin visits (or refreshes) an admin console page that contains user data, including the filters that were applied:
Events
Employees
Apps
Apps (Other)
Accounts
Browsers
Browser extensions
OAuth apps
You can consume these events via webhook, too. Learn more in our developer documentation.