How does Push detect stolen credentials?
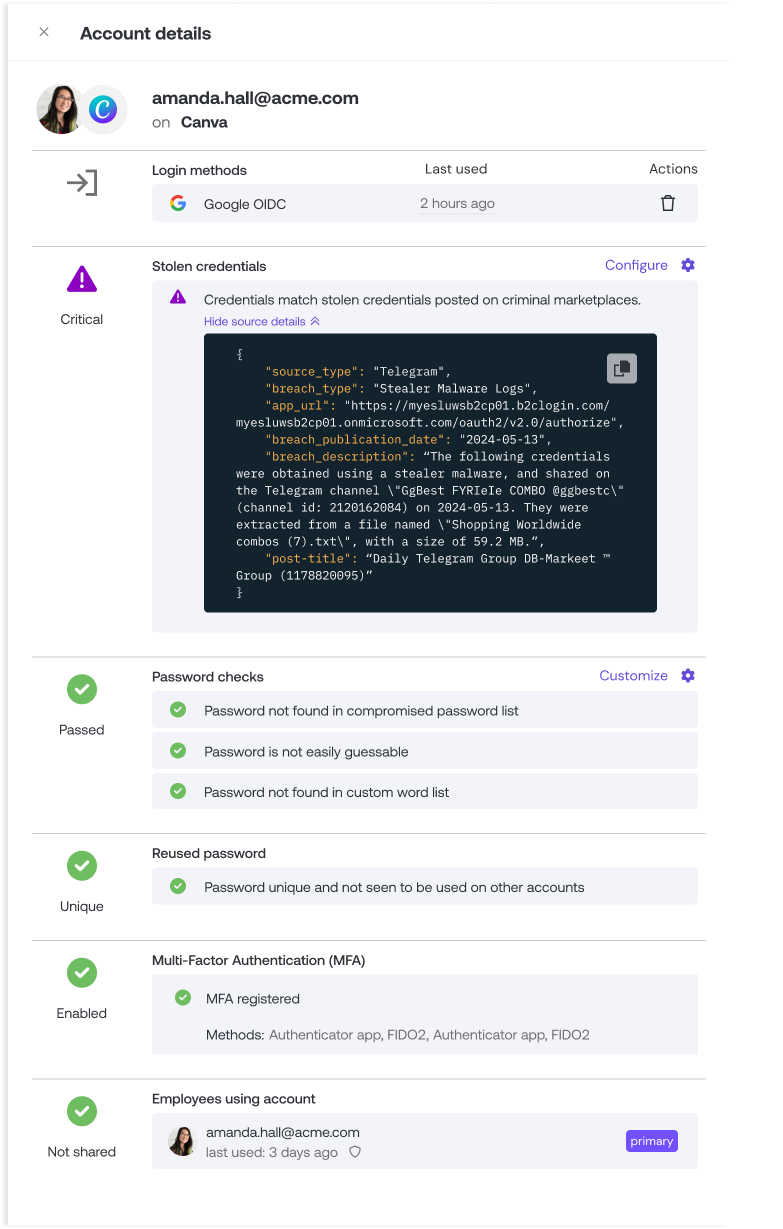
The Push platform detects stolen credentials in use across your workforce identities by ingesting threat intelligence data and then verifying which credentials flagged by TI sources are still being used by employees.
As described in this related help article, the Push browser extension creates truncated, salted SHA256 hashes of employee passwords in order to perform password strength assessments. These are known as password fingerprints. These k-anonymized fingerprints are never seen by Push’s back-end and exist only in local browser extension storage.
Using these password fingerprints, Push can also verify which credentials from the TI feed match those still being used in your environment.
Here’s how it works:
Push receives TI on stolen credentials from vendor feeds. You can also bring your own TI to the Push platform using the Push REST API. This allows you to share stolen credential reports from vendors you already subscribe to and task the Push browser agent with finding the ones still in use by employees.
For each customer environment, Push checks for customer domains in the data set.
When suspected stolen credentials for a customer domain are present, Push hashes and salts the passwords and then sends those fingerprints to the relevant browser agents for comparison.
If the stolen credential fingerprint matches a known credential fingerprint observed to be in use by the Push browser agent, the platform returns a validated true positive alert.
You can choose to receive alerts for this detection via webhook, ChatOps notification, or in the Push admin console.