This article helps you hone in on which SaaS security solutions might be the best to consider for your specific needs, objectives, and environment.
This article helps you hone in on which SaaS security solutions might be the best to consider for your specific needs, objectives, and environment.
When you’re looking to secure your organization’s attack surface, you need to know about all the assets that store or process your data. That includes your corporate-owned assets as well as all the cloud and third-party cloud services your employees use or have used in the past.
Cloud apps are much harder to inventory than corporate-owned assets simply because employees are typically the owners of these assets. They sign up online and start integrating them with their other apps and using them for work, often without IT even knowing about them. In fact, 80% of workers admit to using SaaS apps at work without getting approval first, according to a survey by G2.
Risk #1: SaaS sprawl, Shadow IT and IDs
The lack of central oversight and ease of sign-up, integration, and adoption of SaaS is what leads to SaaS sprawl, which can become unmanageable even for highly sophisticated and well-resourced security teams. That same survey found that “Shadow IT cloud usages are estimated to be 10x the size of known cloud usage.” Shadow identities, the unknown and unmanaged accounts connected to SaaS apps and integrations, are another result of SaaS sprawl.
Attackers also know about these issues and are actively exploiting SaaS sprawl complexity, targeting SaaS account with weak access security controls as an easy way to get into a company’s data or systems. They can simply set up free password scanners to scan for accounts that use the same password as the one they compromised and then drop that information into a data dump. With privileged access gained through those accounts, attackers can potentially access customer data, financial and legal records, deploy and execute malicious code, take control of websites and social media accounts, and so on.
Risk #2: SaaS supply chain
Another prime target for attackers is the SaaS supply chain. Plainly speaking, that’s when an attacker compromises one SaaS app that’s integrated with your core business platforms. They use that access to exploit app permissions to steal sensitive data from other systems integrated with that core platform and/or to create backdoors into your network.
To pull off these attacks, they use those cloud service provider access tokens to compromise the provider’s customers for supply chain attacks. These attacks are purely opportunistic, but can have massive and widespread impact for a large number of organizations.
Finding the right solution
As you begin searching for SaaS security solutions, you’ll likely find that there’s no one set category of product that solves the SaaS sprawl problem, shadow IT and identity, and supply chain problem. Instead, there are cloud access security brokers (CASBs), SaaS security posture management (SSPMs)/cloud security posture management (CSPMs), Shadow IT tools, and even endpoint detection and response (EDRs), all focusing on different areas of SaaS security and solving a variety of problems in this space. With no clear categories, it makes evaluating solutions especially difficult because doing a feature by feature comparison isn’t really possible. The right solution depends largely on what your objectives are, what infrastructure your business is built upon, and what resources you have to drive and manage those solutions.
We’ve written this guide to help you weed through different types of SaaS security solutions to find the right fit for your company. By taking the time up front to set clear objectives, you can hone in which solutions warrant your time to test and evaluate.
In this guide, we’ll help you:
Refine your SaaS security goals
Select which solutions are most likely to meet those goals
Ask hard questions of SaaS security vendors you’re evaluating
Make a case internally for budget by discussing not just the security gains, but how those solutions can help meet broader business initiatives
Learn how Push helps by equipping your employees to use the SaaS apps they want, securely
Another major thing to keep in mind is the larger perspective of the company. After all, whatever solution you pick will need to be adopted and used by the entire company, so understanding if any key business initiatives will be aided by (or harmed by) the SaaS security solution is critical.
One common concern is the costs associated with SaaS sprawl. A recent report found that nearly 40% of all SaaS licenses go unused. Given that most companies spend around $5800 on SaaS apps per employee every year, according to that same report, the potential cost-savings of removing dormant or unused apps is massive.
Of course, the security benefits of removing all those dormant apps shouldn’t be ignored here either – by reducing your attack surface, you’re drastically lowering your risk of attacks through those SaaS apps or through employee SaaS account compromise. It’s a win for the company overall and a huge success for your team.
Now, let’s dig into common security goals for organizations seeking SaaS security platforms. With these goals in mind, you can begin asking your team and vendors you’re evaluating some pointed questions so you know what to expect from each solution.
Security goals
Consider the following criteria when evaluating SaaS security management solutions:
One of the top things you’re probably looking for in a SaaS security solution is visibility into what applications are part of your cloud attack surface, which third-parties have access to your data, and if your employees are using apps securely so you can reduce the risks that SaaS introduces to your business. Now that SaaS is primarily owned by employees, - 73% of SaaS spend and 77% of SaaS applications are controlled by individuals and lines of business - it can be a huge challenge to get full visibility into every app they’re using and connecting to your business data, let alone how securely employees are using the app.
In this section, we’ll present some questions about the solutions you’re evaluating that will lead you toward the right solution for your business:
Visibility
The first step of any SaaS security strategy is getting visibility of every app your employees are using. Knowing that information, you can better understand the scope of risk SaaS presents to your business and hone in on exactly what problems you need to solve to better secure your organization and reduce your SaaS attack surface.
How does the solution find SaaS apps employees are using?
Every solution uses a different data source to discover SaaS use in your company, so when you’re evaluating solutions, understanding both the data source(s) the solution uses and the limitations of those data sources is key. In this section, we’ll explore the pros and cons of each approach and explore any blindspots the approach may have.
On average, companies have 651 SaaS applications in their technology environment, but most enterprises underestimate that amount by two to three times.
Many legacy SaaS security tools, such as cloud access security brokers (CASBs) detect employee SaaS use by inspecting network traffic. They’ll analyze DNS, SASE, VPN, proxy, and firewall logs to get coverage of employee actions. If you’re working in a company that doesn’t allow flexible work environments or remote work and if you require all employees to access work platforms and internet browsers through a corporate VPN, these solutions do a fair job. CASBs come with some downsides and hurdles, though. One is that you may have to install agents on each employees’ device(s) to get coverage if they’re not working from the office and, in a post-pandemic world, that may not scale with your business.

SaaS security posture management (SSPMs) and cloud security posture management (CSPMs) tools can be useful if your goal is to only secure around 20-30 core applications that you’ve already sanctioned and vetted thoroughly. These tools work best if you’re on the highest paying tier for those core business applications because they rely on API data from those core platforms to find a portion of employee SaaS use.
One major concern with these solutions is that they come with fairly large SaaS blindspots. If your SaaS security solution only captures usage data from APIs, you’ll be missing all of the SaaS apps your employees are accessing through the browser. Essentially, you’ll only see the cloud apps and platforms you already know about or those that directly integrate with them. SaaS was built to be accessed through the internet to make it accessible for everyone and easy to adopt and use for even non-technical users. To ignore all SaaS accessed through the browser, then, means you’re accepting blindspots and not really solving the problem of visibility into unsanctioned employee SaaS usage.

The shortcomings of these types of SaaS solutions is that they, according to Gartner, “are still largely focused on the management of non-SaaS applications where an installation is present.” In other words, they’re trying to solve the SaaS sprawl problem by using solutions meant to address on-prem software security issues. They’re tacking on SaaS security as a feature alongside their legacy solutions rather than considering the problem from an entirely new perspective or vantage point.
With that in mind, it’s worth at least exploring modern SaaS security solutions that approach the problem with an entirely different perspective.
We approach the problem of SaaS discovery by using browser data and APIs. That’s because the primary way employees sign up for, login, and access SaaS tools is through their internet browser, so we capture information about what they’re signing into where they’re signing in. We’ll go into more detail about our own solution at the end of this ebook.
Other modern solutions will look at employee email inboxes to find SaaS use by looking for “Welcome to Slack!” types of emails that indicate a new platform has been accessed. The biggest downside of this approach is that it has a very high rate of false positives because the solution will surface every SaaS trial signup and every single-time access. Essentially, it doesn’t distinguish between just SaaS access and SaaS usage.
Can the solution distinguish between SaaS usage and SaaS access?
SaaS discovery and Shadow IT tools often struggle to tell the difference between an employee actually using a SaaS app and them simply accessing the app or app’s website. This point may seem like a minor quibble, but it can quickly become a signal-to-noise problem for your team, as they get burned out by false-positives, unless you know up front what you’re getting into. If the tool uncovers SaaS use by analyzing network-level data about your employees, you’ll need to find a way to determine if that employee is actually using the app (through the browser) and integrating it with business data and platforms (through APIs) before you know whether it’s worth your team’s time to do a third-party app review.
Often, employees will visit a website simply to see if the app can solve their problem or replace another app, but they may never actually create a SaaS account with that app, adopt it, and start using it - they may not even sign up for a trial. If you have 100+ employees at your company, that network-level discovery process will leave you with a lot of false positives that you’ll need to manually wade through. Consider how you would then work with employees to determine if they’re actively using it or if they were just evaluating it.
Will it find third-party integrations connected to your core cloud platforms?
Finding SaaS apps employees are using is a great start, but what about all those integrations they’ve installed and connected to your Google Workspace and Microsoft 365 tenants? Full SaaS visibility includes knowing not just what SaaS apps employees are using, but also knowing what apps they’ve connected to your core platforms. From a security perspective, those third-party integrations present just as much risk as a SaaS app.
Third-party integrations are incredibly powerful tools, but they need to be connected to your business and user data in order to work. That means each one is an additional third-party vendor that needs vetting. That’s a tall order if you have a small team or one who’s already inundated with work. A solution that supports your team will detect risky traits about those integrations, such as if they’re requesting excessive access to your data or if they’ve not been verified by Google or Microsoft in their app stores.
Look for a SaaS management solution that will provide you with context not just about the app, but which employee “owns” or has installed it, how often they’re using it, how important it is to their work, and if they’re using it securely. If the solution doesn’t give you visibility as well as context, you won’t be able to make a sound decision on whether the app can stay or if it should be removed.
Risk and detection
Will it show you if employees are using these applications securely?
What information will it show you about employee SaaS use? Many tools on the market focus on the security of the SaaS app and provide visibility into who in the company is using the app, but they may stop there. Others focus on SaaS user information to help you prevent SaaS account compromise. Those generally provide information not just who is using the app, but also how they’re using it. Additional context about SaaS apps may also be useful for you, such as data around who the app administrator is within the company, if employees are using security features like MFA, whether they’re logging in securely with either social login (Login with Google; Login with Microsoft) or with username and password, and whether that password is strong/weak, if it’s shared with other users, and/or if it’s shared with other apps.
See what data each third party has access to and understand how they protect that data
This level of information is what your team may be manually handling via SaaS app reviews and audit processes, but some solutions will also provide insights into this information to make your manual reviews less time-consuming.
At a basic level, you’ll want to ensure solutions you’re considering give you visibility into what data each third party can access. A modern solution will clearly show what access permissions have been granted to that application, which can help you prioritize which are reviewed first and which are so high risk that they may need to be removed.
You should also consider if the solution(s) give this same level of scrutiny to integrations and OAuth apps connected to each SaaS app employees are using. These are often hiding within the core application and unknown to security and IT teams. However, they can ask for just as many data and access permissions as the core app, so they should be considered as risky, if not higher risk, than SaaS applications. Our suggestion is to find a solution that provides all of this necessary information without drowning you in false positives. We’ll dig into this a bit further later on.
Can it rapidly detect third/fourth/fifth-party data breaches and SaaS account compromise
As soon as a SaaS compromise hits the headlines, you can bet on your leadership team reaching out to ask whether your company is affected or likely to have been compromised. Answering that question can often sidetrack the whole team as they begin investigating.
A strong SaaS security platform can help you quickly and easily answer that question so you can move on, or, if you are affected, move as fast as possible in incident response mode. With a continuously-updated SaaS and cloud inventory at the ready, you’ll know whether you’re using the affected app, which is a big help.
More progressive solutions will also alert the team if there are any strong indicators of compromise from SaaS or employee accounts, in chatops channel messaging. These features help your team be more proactive and less reactive and frenzied when the bosses start asking questions. We’ll be talking more about the impact to your team in the next section.
Complexity and impact to your team
How are these risks presented to you and how will it affect your mitigation process?
You’ll want to understand how this tool will integrate with your current workflows for risk mitigation. Many modern tools on the market focus on SaaS app risk and to do this, they usually create a risk scoring methodology in order to prioritize risks based on severity. These methodologies are somewhat subjective and a solution may not rank risks the same way you would - after all, these tools usually don’t know all of the context around how the SaaS app is used in your company, whether the data stored in or connected to that app is highly sensitive, and so on.
Solutions build risk scores to try to account for those variables, but you’ll want to ensure that their methodology aligns with your own risk tolerance levels for the company. The main question to ask is, “If I had access to the data this tool is using for risk scoring, would I prioritize these issues the same way they have?” If the answer is no, then the risk scoring and prioritization will be relatively useless for your purposes. If you agree with the general methodology, the prioritization can help your team work through the issues they found.
How will it support the remediation of identified issues?
Like many security tools on the market, SaaS management tools often detect and monitor for issues, triage and prioritize those issues, and send alerts to your team when they need to take action. It’s on you to then fix those issues, and even to determine what you need to do to fix them in the first place. In order to shore up your defenses, you need to actually go through the hard work of fixing issues, which usually requires security experts with specialized tools.
Instead, look for a solution that has a built-in way to fix the problems they surface. For SaaS, the most sensible way to do that is to work with employees to get the necessary context about how they’re using the app in order to make better business decisions because we know that SaaS is now mostly owned by employees, not IT. Knowing not just what employees are logging into, but how they’re accessing it, if they’re using security features such as multi-factor authentication (MFA), if they’re admins for the account, if they’re still using the app, and what they’re using it for, helps you determine if letting the app remain a part of your SaaS estate is worth the risk.
The step beyond just getting that context is to work with employees to actually fix issues so the security team doesn’t have to. This is a tricky workflow to get right, but when done well, you get a truly scalable SaaS security solution.
How will it support your third-party app and vendor reviews?
Now that you know what third-party cloud service you’re using, how does the solution help you decide which of them to review first to understand and manage the risk? Some tools provide relevant business insights about the SaaS they discover that will cut down on some of the manual reviews your team needs to do.
Some will also rank and prioritize which need to be reviewed first, based on some of the traits they’ve considered during the risk scoring process. If you have a small team that’s struggling to keep up with vendor and app reviews, you may decide to go with a solution that can provide enough information automatically within the product dashboards that may reduce the need for a full review.
Related, progressive solutions will find apps that are no longer used (abandoned or dormant apps) so you can reduce the number of reviews you need to do at all. If you can quickly or easily delete unused apps, you’re automatically reducing the review workload for your team.
Is your team able to effectively configure, manage, and monitor the solution?
Many SaaS security tools require significant time to configure properly and deploy. Even once that process is complete, your team may need to be dedicated security experts to manage and monitor those tools to derive any meaningful security impact. If you have just a small team of people handling both IT and security at your organization, you’ll need a more streamlined, lightweight solution to get any real value from your investment.
Even if you *do* have a sophisticated security team on hand, remember that retaining them and hiring additional security experts is a challenge for every company, across all industries. All of that makes it worth considering a more automated solution for SaaS sprawl that requires little management, is flexible and will adapt to your needs, and will scale with your business and team.

Consider not just the time spent on deploying a legacy tool such as a CASB, but also resources available to your team. Will this tool require a new security professional who specializes in working with these products? Will your team need to know proprietary languages and have worked with the tool before to actually get it working and fully implemented?
Modern SaaS security tools will often let you give them a test drive so they can earn your trust and prove their immediate value before you ever have to subscribe or sign any contracts. Take advantage of this and let your team play around with some of these solutions to see if they might handle everything you need to enable SaaS securely in your business.
Impact on employees

As you evaluate solutions, consider not just the experience for your security or IT team, but also the employees. With flexible working environments quickly becoming the norm, two-thirds (66%) of Gen Z and over half of (53%) millennial information workers say autonomy to choose the apps, services and devices they use for work is a top priority,” according to a Forrester survey of 10,000 information workers across generational categories. With those younger generations comprising approximately 80% of the workforce, their preferences shouldn’t be ignored.
With that in mind, if the tools you’re evaluating are focused on locating SaaS apps employees are using simply with the goal of blocking them or removing them, consider the potential negative impact for employees as well as the blowback your team might receive as a result. A report from G2 found that when employees aren’t allowed to choose their own tools and are forced to use only company-sanctioned apps, 82% have said they’ve pushed back on IT or management about which collaboration tools should be used. It’s an unpleasant spot to be in as an IT or security team and it absolutely doesn’t have to be that way. But employees aren’t ignorant about the risk - nearly 80% agree that the “biggest threat of introducing new technologies without IT’s approval is risking the security of the company.”
Since employees recognize the risk, they’re likely more willing to help secure their SaaS use than you might think. Rather than taking an old school enforcement approach, think about a more flexible option that can adapt to what employees are starting to expect. Back in 2019, Gartner asserted that “by 2023, 40% of professional workers will orchestrate their business application experiences and capabilities like they do their music streaming experience.” It pays to be ahead of the curve rather than trying to use legacy tools that will need to be replaced in a year or two.
If blocking isn’t your primary goal, then, and security and employee productivity and happiness is your new driver, you may want to evaluate a solution that has progressive controls for SaaS that you can customize to you and your employees’ needs.
Push’s Solution

Push identifies the security issues that arise from your employees’ use of SaaS apps and guides them to self-remediate. This allows your coworkers to continue using their favorite SaaS freely and securely, without creating more work for your security team.
Automate the fix by working with employees
Push provides a scalable way to detect and fix SaaS security issues. We equip your employees to secure the SaaS they own, and improve the cyber resilience of your whole organization - this is user-centric security.
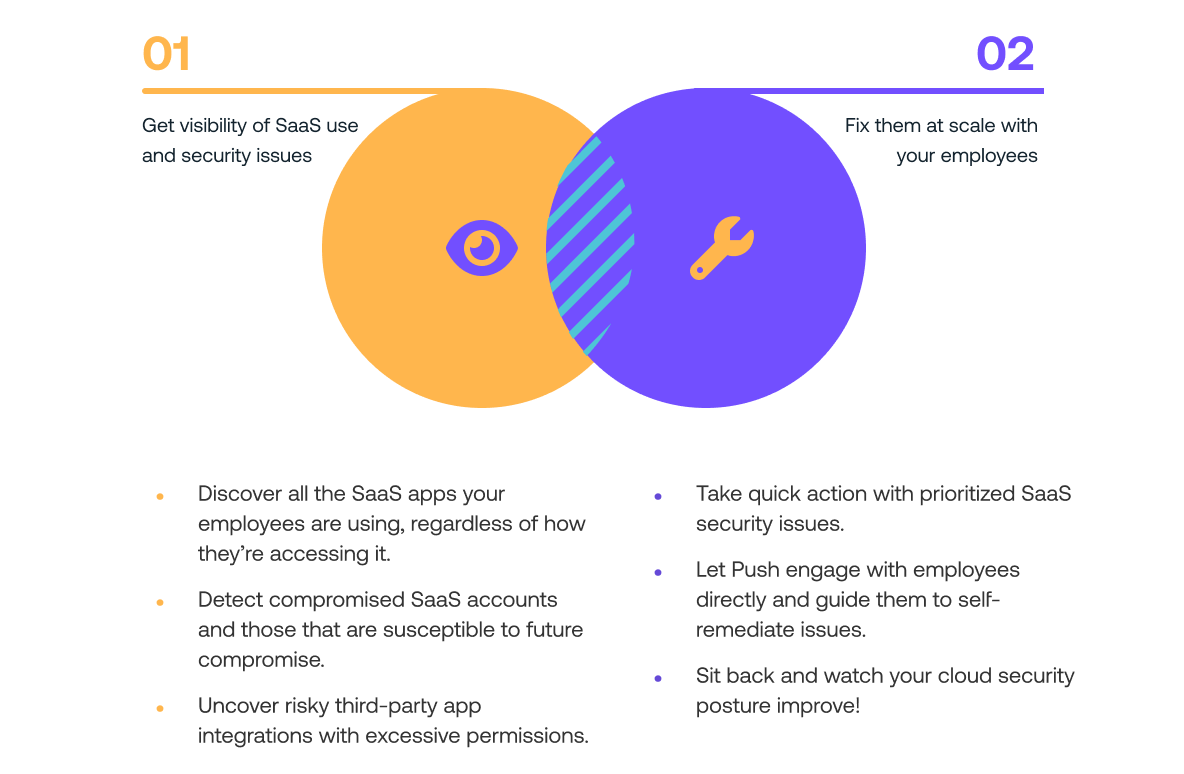
Get visibility of SaaS use and security issues
Discover all the SaaS apps your employees are using, regardless of how they’re accessing it.
Detect compromised SaaS accounts and those that are susceptible to future compromise.
Uncover risky third-party app integrations with excessive permissions.
Fix them at scale with your employees
SaaS security issues are prioritized by risk to the user and your organization.
Push engages with employees directly and guides them to self-remediate issues.
Sit back and watch your cloud security posture improve.
What you get with Push
Improve your cloud security and cyber risk management - Push continuously finds and fixes SaaS security issues so employees can carry on doing what they do best, but without exposing themselves and your company to unnecessary risk. Get visibility and control over where your data is held and how it is secured, and track all your security wins over time.
Generate time and cost savings - We get that all security teams are overworked and under-resourced. We’re here to take things off your plate, not add to it. Push works directly with employees to help them improve their passwords, enable MFA and remove dormant apps so you don’t have to. With full SaaS visibility, you can consolidate your SaaS supply chain to reduce third party security reviews.
Drive positive employee engagement with security - Your security team can be the enabler that allows your employees to safely adopt new SaaS tools that make their lives better. Push provides guidance to employees that is friendly, approachable, and easy to understand so they can both secure their use of SaaS while learning about security risks and best practices.
Make your company more productive and competitive - Businesses that can safely adopt innovative new technology earlier, and benefit from its advantages for longer, will be more productive, efficient and successful. You can make early SaaS adoption a competitive differentiator for your company.
Solution overview
Discover the SaaS your employees are using
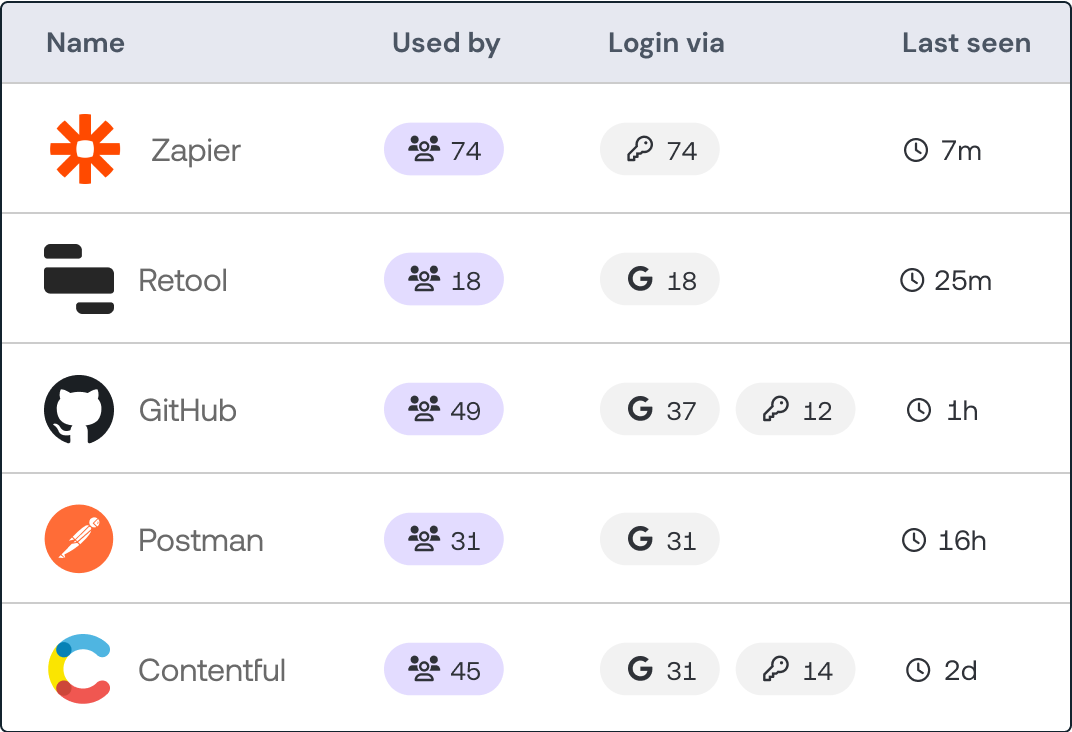
Finding all the SaaS your organization is using forms a critical part of IT asset discovery. There are a few different methods for doing this, from using firewall and proxy logs to buying cloud access security brokers (CASBs) and Shadow IT tools, but they all struggle to provide the breadth and depth of information you need to manage risk.
Push uses a browser extension to discover password-based SaaS use and API integrations with your MS 365 or Google Workspace tenant(s) to discover social login SaaS use. This approach gives you continuous visibility into what SaaS is being used and how securely, no matter how your employees access them. The SaaS dashboard shows you what SaaS is being used, who in your organization is using it, and how securely.
Prevent and detect SaaS account compromise
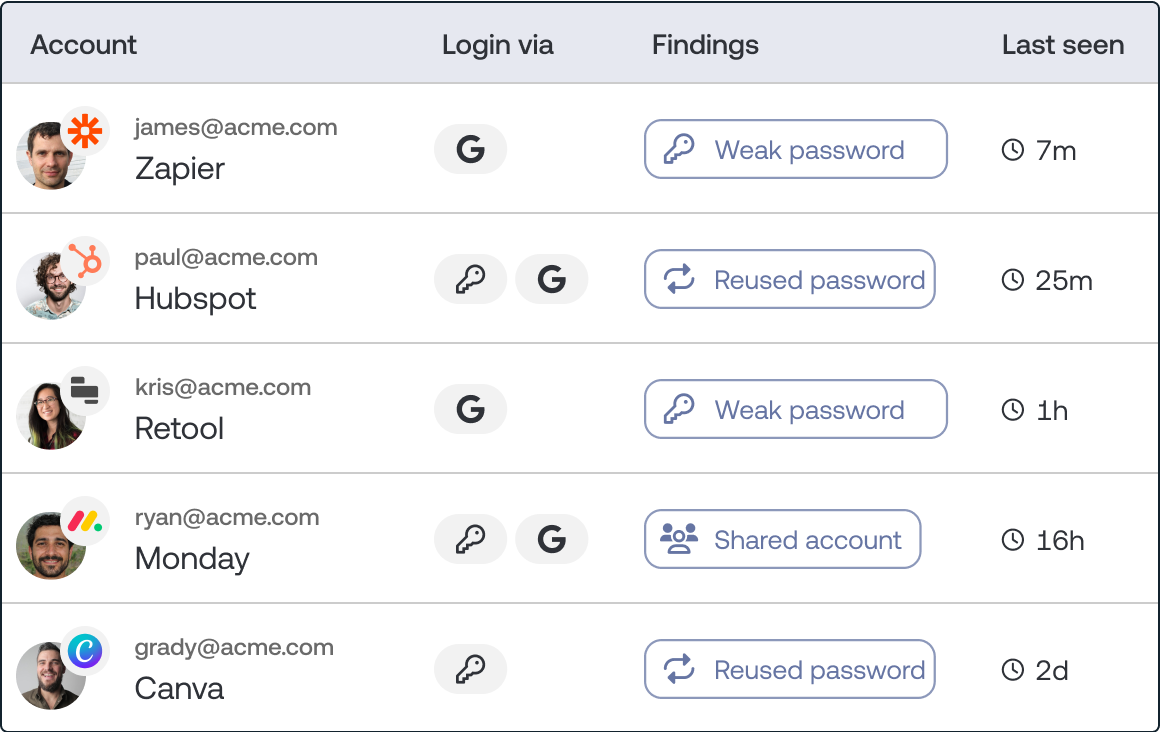
Improving employee SaaS account security is the most effective way to reduce SaaS risk. Using MFA, single-sign on, and strong, unique passwords, are easy ways to protect SaaS accounts. When employee accounts are compromised, you need to quickly detect reliable indicators of compromise to kick off an investigation.
Push shows you what security measures employees are using to protect their SaaS accounts so those susceptible to account compromise can be identified. Push engages directly with employees and guides them to better protect their accounts.
High fidelity indicators, such as the creation of malicious mail rules, are used to detect account compromise. Employees are asked to verify if suspicious activities and logins on their accounts are them or not.
Manage third-party integrations
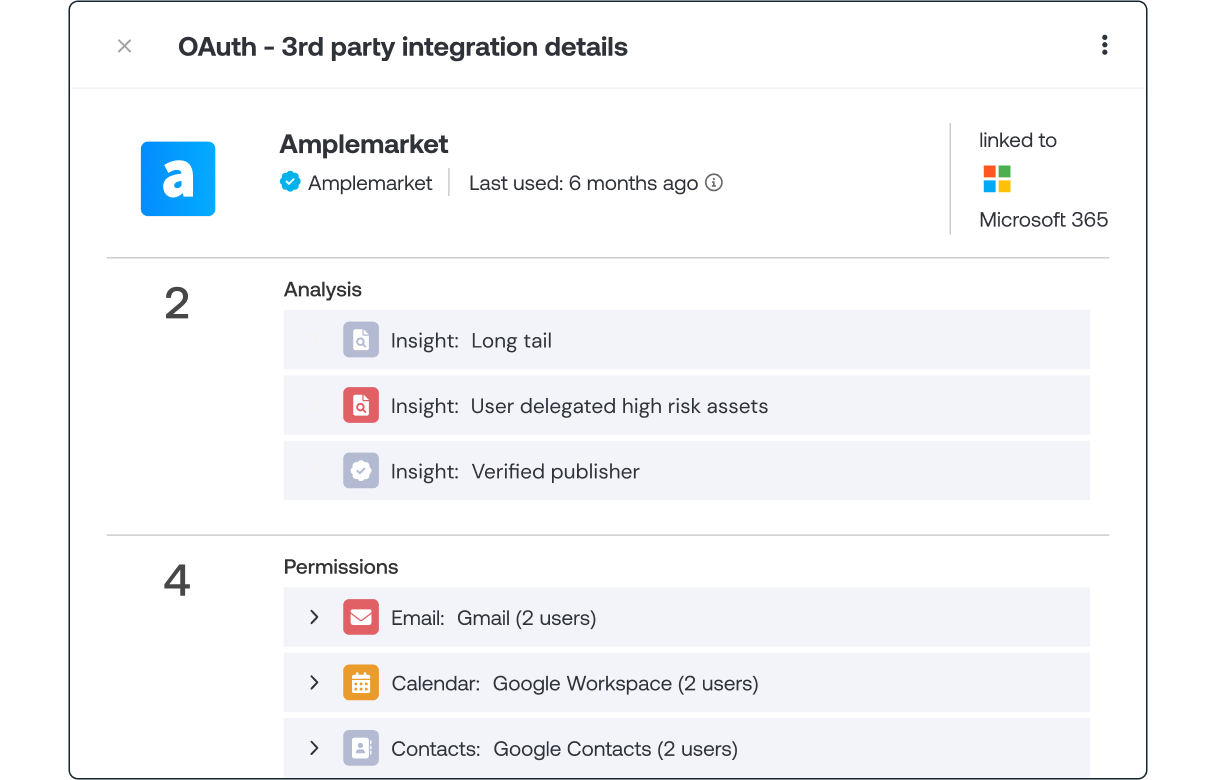
Discovering all the SaaS apps used by employees is hard enough, but what about all the app integrations your employees are connecting to your core work platforms? These integrations permit third parties to access sensitive data - such as OneDrive access or email and calendar ReadWrite - much of which are very attractive for attackers.
Push shows you:
Which apps are connected to your work platform (MS 365 or Google Workspace),
What data they can access,
Which employees have consented to their permissions and
Whether they appear to be risky or suspicious.
Push engages with employees to remove risky or dormant app integrations. If any of these vendors are compromised, you can quickly work out what data they have access to and understand the potential risk to your organization.
Reduce your cloud attack surface and SaaS supply chain risk
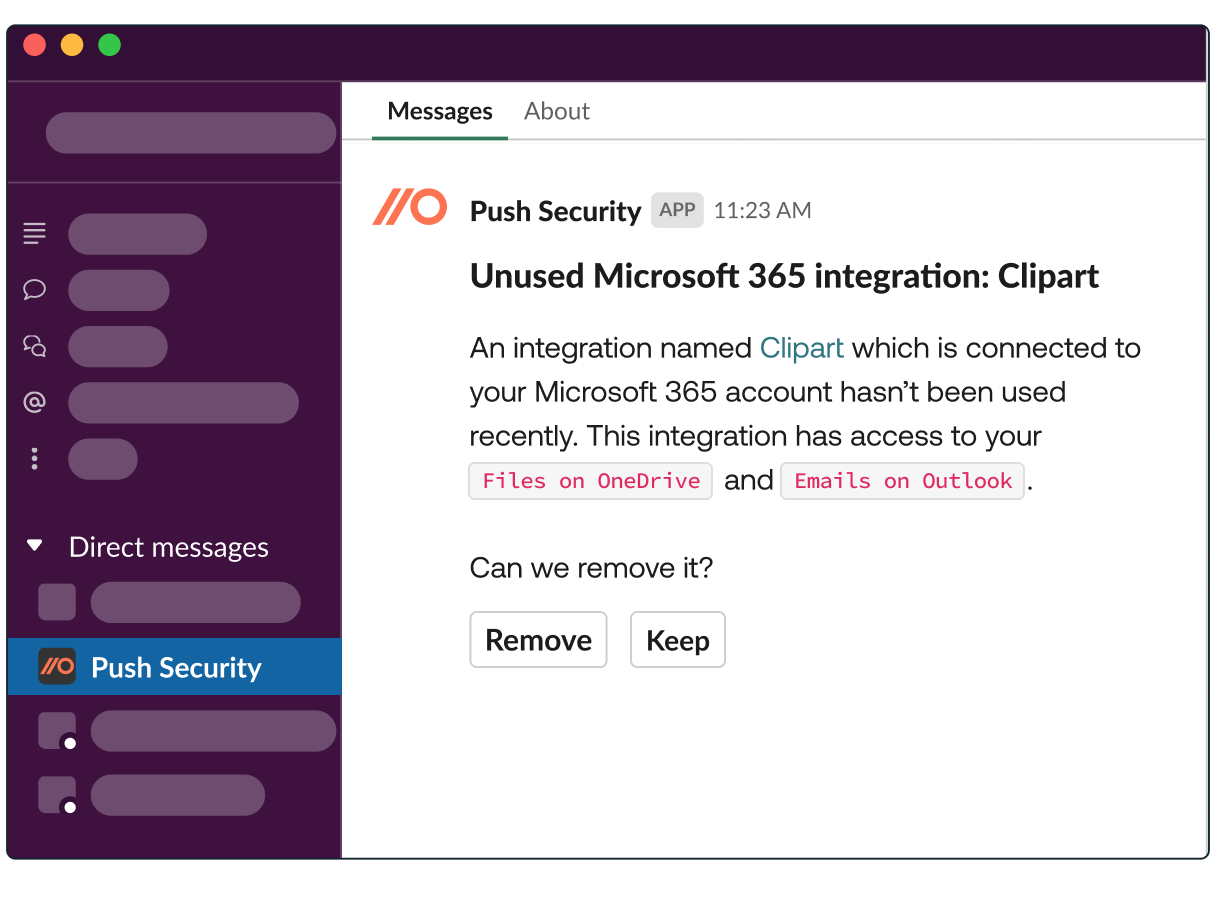
It's hard to maintain real-time visibility of what cloud apps and vendors your business uses, the data they can access and the security controls they have in place to protect it. What's more, SaaS vendors have increased responsibility for protecting your data, therefore requiring greater levels of scrutiny to ensure they can be trusted. The result is a lot of complexity and work for your security team to manage - and considering only 45% of apps are regularly used by employees - most of it could be avoidable if you only knew what you could remove.
Push gives you accurate visibility of all the SaaS third-parties holding your data. Dormant app accounts and integrations can be removed from your attack surface as well as your list of third-party vendors to be assessed.
Push allows you to guide employees to adopt your preferred tool, when you have multiple SaaS apps doing the same job. Consolidating your apps saves the company money and promotes collaboration and productivity across your organization.
How Push works
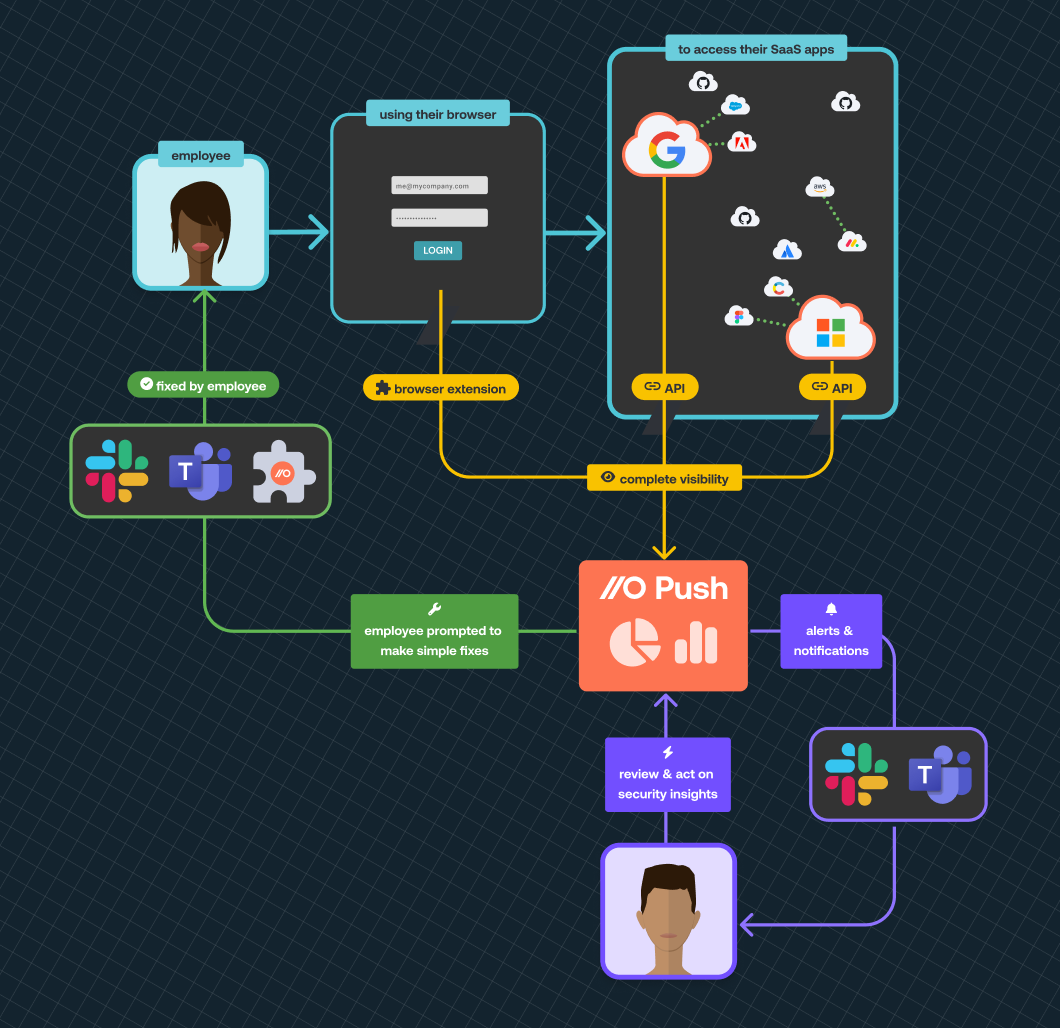
Push comprises four main technical components:
An API integration with your core work platform (MS 365 or Google Workspace) tells us who your employees are, which SaaS apps they are accessing using social logins, whether they are using MFA or not, what mail rules they have set up and which third party integrations they have permitted to connect with your work platform.
A browser extension installed on each employee's browser. This identifies the SaaS apps that your employees are accessing with passwords and usernames, whether those passwords are strong and if they are shared across multiple SaaS accounts.
The Push platform guides you through set up (API integration, browser extension deployment and ChatOps enablement). The platform presents all your processed data and security insights using intuitive dashboards. It is also where you can manage your Push account (licenses, payments etc).
ChatOps is what allows us to engage with your employees to self-remediate identified security issues. We integrate with either Slack or Teams so we can have conversations with your employees.
Deployment
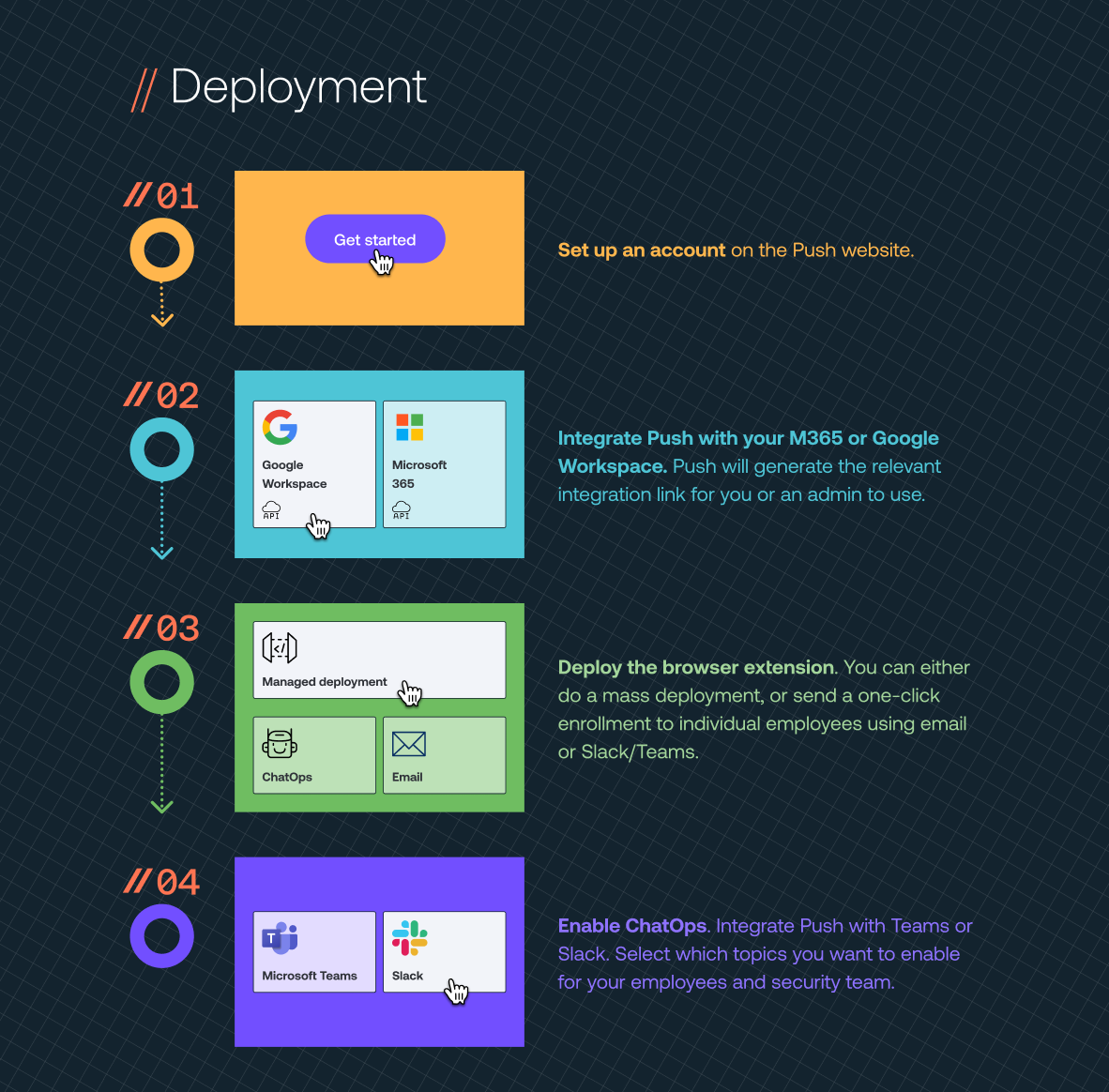
Step 1 - Create a Push account - Head to pushsecurity.com and hit the “Try it free” button. You’ll need to create an account username and password, or continue with Google/Microsoft. We’ll ask you to confirm your email address and whether you’d like to receive product update emails from us. That’s it, you’re in.
Step 2 - Integrate Push with your MS 365 or Google Workspace tenant . You’ll be asked which platform you want to integrate with (you can do both), this will generate an integration link that you or an admin can use. You’ll immediately be able to see a huge amount of SaaS security insights.
Step 3 - Deploy the browser extension to your employees’ browsers - Click on the browser tab and confirm your company email domain that you want Push to monitor. Next select your preferred deployment option; 1) send an enrollment link to each employee over email, they do a 2-click install, 2) send an enrollment link to each employee over slack or teams using Push ChatOps, or 3) a centralized managed deployment to supported browsers using managed chrome, group policy or device management software.
Step 4 - Enable ChatOps - Open the ChatOps page on the Push platform. There you’ll be asked to select either Slack or Teams. This will generate an integration link that you or an admin can use. You can then send yourself a test message to ChatOps work. Head to the employees dashboard, select the employees you want to be engaged with ChatOps and click the “enable ChatOps” toggle.
That’s it. In less than 10 minutes you can be completely set up and taking steps to secure your employees' use of SaaS. You can get started now for free to start discovering SaaS and see if Push will be useful for you and your team.
Sign up and start using for free today!


