New finding type for leaked passwords, automatic licensing for new employees, and improved filtering options
New finding type for leaked passwords, automatic licensing for new employees, and improved filtering options
Here's what's new on the Push platform this month:
New finding type for leaked passwords
Automatic licensing option for new employees
Improved filtering options
Easily identify leaked passwords
We’ve added a filter to quickly identify any leaked password findings among your employee accounts. You’ll also see leaked passwords listed as a separate security finding type on an account or employee record in the Push admin console, so it’s easier to distinguish those from other password vulnerabilities.

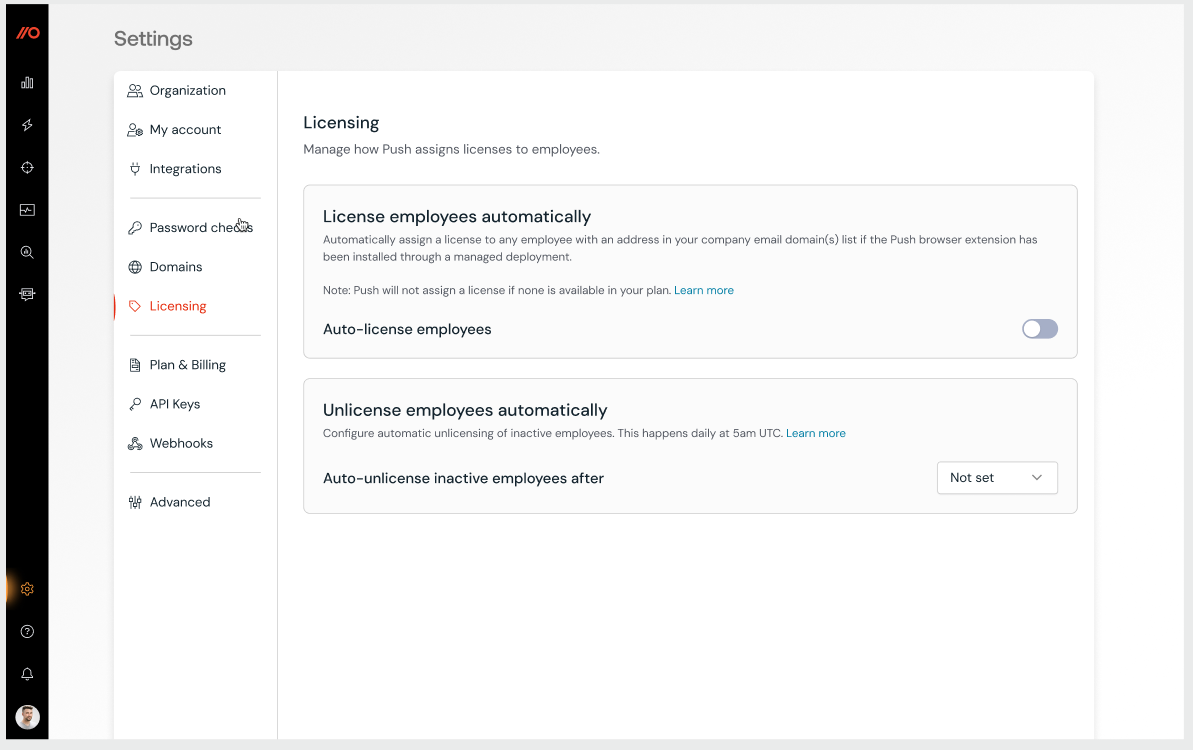
Save time by automatically licensing new employees
Efficiently protect new employees with our new automatic licensing feature. Once you’ve deployed the Push browser extension to employee browsers, Push will identify the user of a browser and then license them on the platform automatically.
Improved filtering options
On the Accounts page, you can now filter by:
Identity provider and login method: This makes it easier to identify accounts using specific IdPs and login methods (SAML, OIDC, or passwords), or any combination of those. We’ve also added timestamps for login methods, which you’ll see on the account details slideout.
App approval status or sensitivity: This makes it easier to find accounts on high-value apps that have vulnerabilities, or see who’s still using unapproved apps.
We’ve also made your selected filters easier to see by displaying them on the page when active.