Use Push to find and secure workforce accounts using credentials stolen in a third-party data breach.
Use Push to find and secure workforce accounts using credentials stolen in a third-party data breach.
When the media reports that a popular third-party service provider has suffered a breach and stolen credentials are being sold online, it’s inevitable for your security team to get asked, “Are we affected by this?”
Push helps its customers to answer this question in seconds and with absolute certainty. Here’s how.
Step 1: Are we using the breached service?
If this service is IT-managed in your organization, then you can probably answer this relatively quickly – at least for the tenant that is IT-managed. If it’s not, then you're going to need to check.
That’s because end-users increasingly create SaaS accounts and tenants themselves without going through IT. When a third-party data breach hits the headlines, security teams are often surprised to find out that they have people in their organizations using that service.
Push uses a browser agent to track every login to every application made by your employees. It offers ground truth for answering questions like: Are we using the service? Who in the business is using it, and how are they accessing it?
Push can also highlight issues like missing MFA and if an employee is re-using the same password across multiple services — vital information if user credentials for the breached service have been leaked.
There are other data sources that can be used, but they all have their drawbacks:
Network or SWG can show you whose endpoints accessed an app website, but not if they've ever logged into the app.
IdP can show you that you're using an app if it’s accessed using SSO, but if that’s the case then you already know about it. It won’t show you non-SSO apps, tenants, or accounts that are more likely to be compromised using stolen credentials.
Email can be used to quickly tell you if employees have received email from an app – indicating an account might exist – but won’t tell you if they signed up using personal email, when they last logged in or if they are using the same password for everything.
Finance / contract records take time to search through and will only cover the services you pay for (many SaaS products offer a free tier). Obviously these records won’t tell you anything about vulnerable accounts.
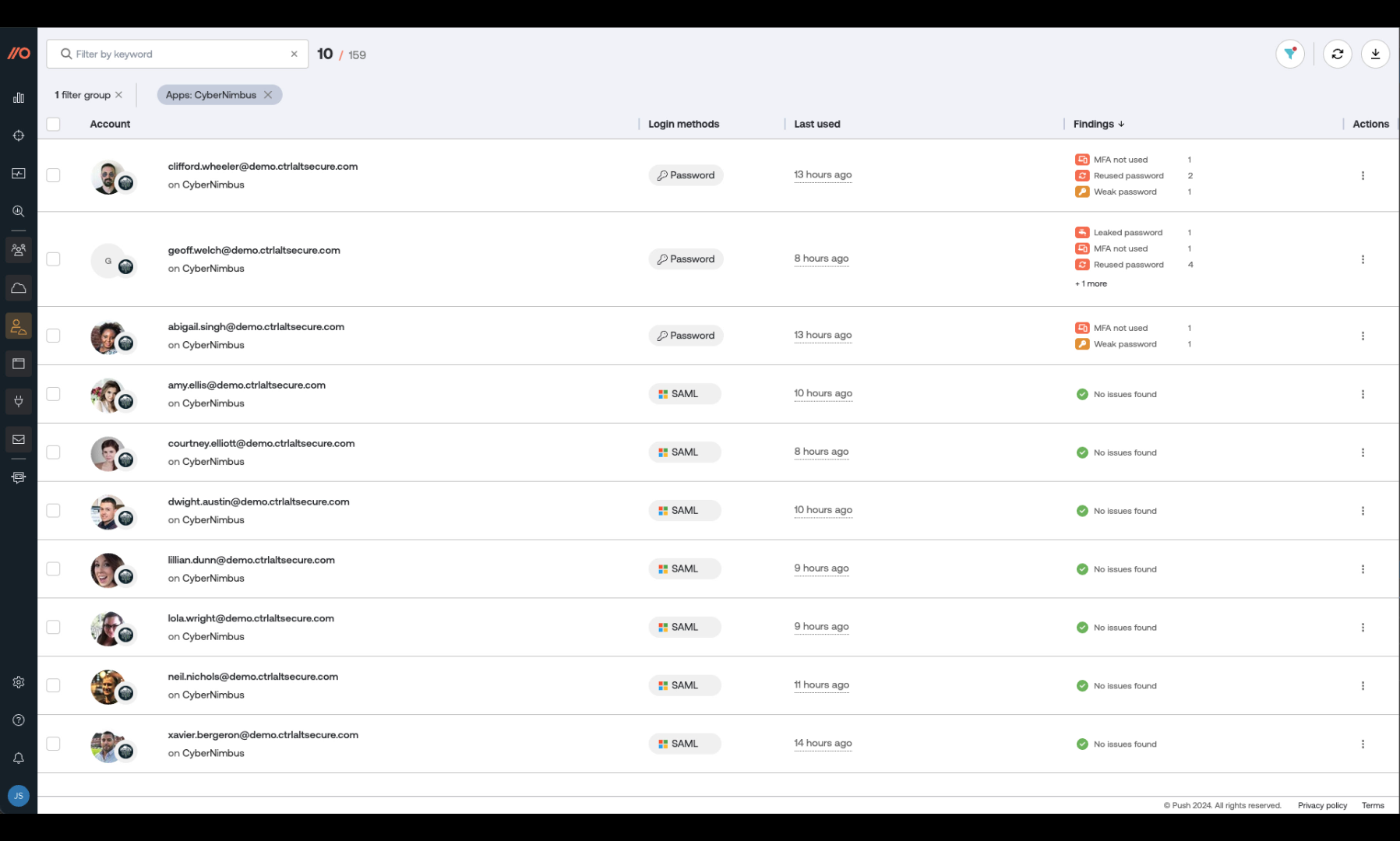
Step 2: Are any of our accounts currently vulnerable to account takeover through stolen creds?
If credentials are being sold on the dark web for a service your employees use, then you need to quickly determine whether any workforce accounts can be accessed using just the stolen credentials. In other words, are any of these accounts using a leaked password and/or missing MFA?
At this point, you might reach for your IdP and make sure that MFA is enforced for all logins to the affected app. But that’s only going to cover apps and tenants already using SSO. To make things more complicated, most apps still allow username and password logins in addition to SSO logins. You need to see accounts with SSO logins and local logins.
The data that Push collects in the browser provides rich web app context. That means Push shows you how your employees are authenticating on every app, whether it’s password, OIDC, or SAML.
When you search for a breached third-party service in Push, you’ll see which employees are using usernames and passwords but missing MFA on their accounts. You can then prioritize these accounts for password resets and enabling MFA to stop any stolen credentials from being used to access those accounts.
As well as highlighting accounts missing MFA, Push fingerprints every password using a shortened salted hash and checks in the browser whether it has been leaked and/or is easily guessable. Armed with this information, you can quickly get these vulnerabilities fixed to reduce the likelihood of an account takeover.
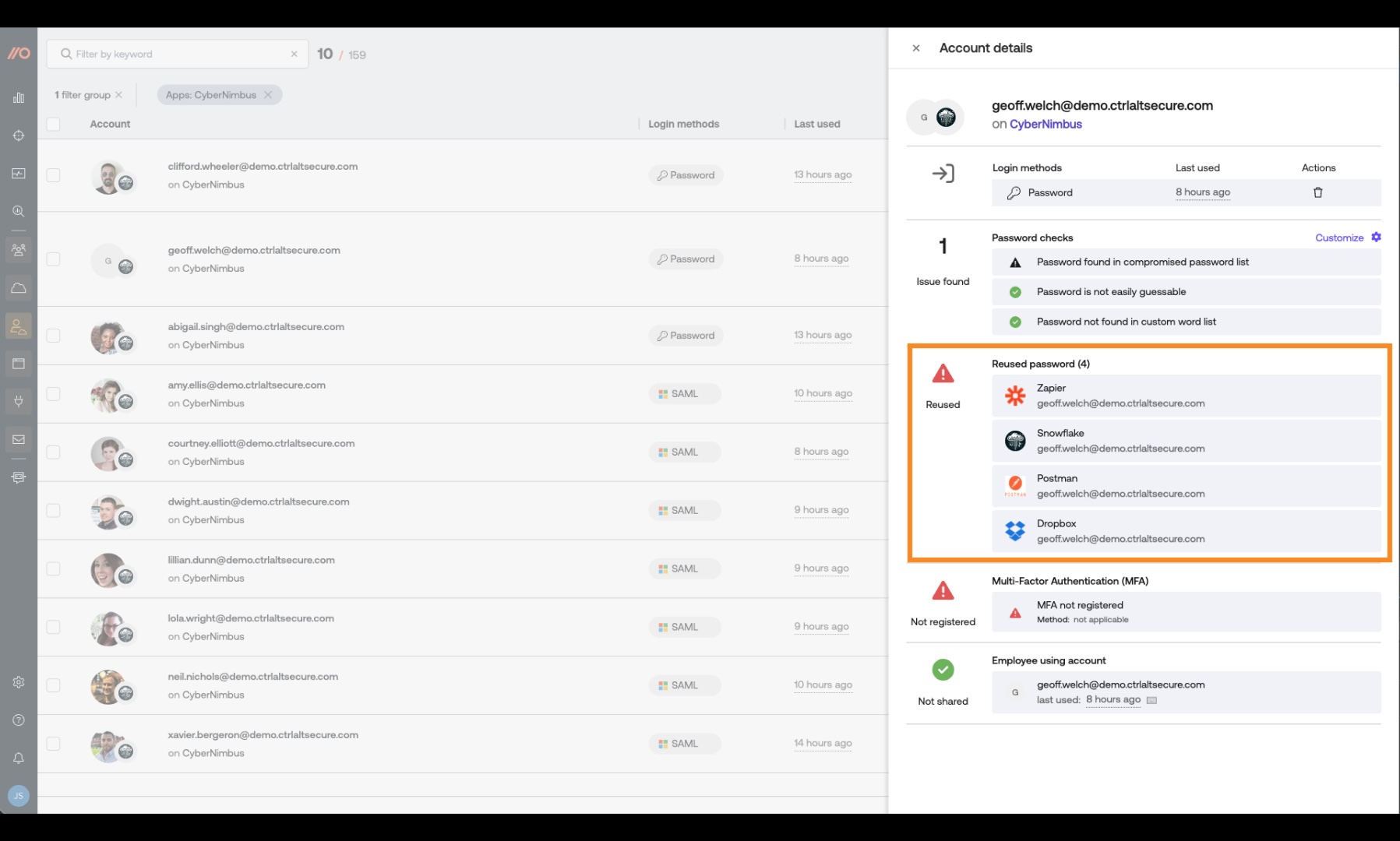
Step 3: Are the stolen credentials being used anywhere else?
The next consideration is whether the stolen credentials can be used by an attacker in a credential-stuffing attack to compromise accounts on other applications.
This is an important, and often overlooked, ring of the third-party data breach blast radius.
Here at Push, we see that on average 1 in 3 users in every business reuse passwords across multiple accounts.
The password checks performed by Push also identify password reuse between applications. So if there’s a chance that a password has been stolen as part of the third-party data breach, you can make sure it’s changed across all applications.
Take action before breaches hit the headlines
The workflow described above takes seconds to perform in Push. It enables you to quickly investigate a third-party data breach to determine if you could have been impacted, and if so, to take targeted action to mitigate the risks.
That said, no one enjoys scrambling to respond to these kinds of incidents. If you use Push, you can actually get out ahead of these issues so you’re not stuck having to react.
Push integrates stolen account threat intelligence and alerts you when employees are currently using the same password that’s being sold on the dark web. This allows you to take action at the earliest possible opportunity and harden vulnerable accounts before any data breach is reported in the media.
What this means for you is that next time you’re asked, “Does this affect us?” you can say you dealt with any issues way before it landed in the headlines.
Do we need to log in to another security tool to do this?
No. Using the Push API, you can quickly gather relevant data to support the response to a third-party data breach in your SIEM or XDR solution.
Why not eliminate the risk of password-based attacks altogether?
Push gives you the ability to react quickly and decisively to a third-party data breach. But it also enables you to take proactive steps to eliminate the risk of password-based attacks altogether so stolen credentials from third-party data breaches no longer pose a threat to your business.
Push does this by:
Stopping your employees from creating accounts with leaked, weak and reused passwords.
Pinning passwords to individual apps.
Helping you to get all apps and accounts behind SSO.
Blocking phishing attacks against your employees so their credentials aren’t stolen.
If you want to find out more about how Push can help you mitigate the risks of employee credentials being stolen in the third-party data breach, then book a demo and we’ll be happy to show you.


