Answering key questions about your exposure to identity threats using Push data.
Answering key questions about your exposure to identity threats using Push data.
There are many factors that can make a user account vulnerable to identity-based attack techniques. Using Push data, we calculated how many vulnerable identities the average organization has, showing how different vulnerabilities leave an identity exposed to different methods of account takeover.
Our dataset
This analysis is based on a snapshot of when organizations begin using the Push platform, once enrollment has completed. Data from trial and partially deployed organizations is excluded.
Early adopters of new identity security products like Push are likely to have a higher than average level of maturity in this area – even prior to using Push. So, the findings may not be accurate for all organizations, particularly those with lower awareness of identity security challenges.
It’s also worth noting that passwordless authentication makes up a very small percentage of the overall authentication factors detected. If you’re in the minority of organizations that have widely adopted something like passkeys or biometric authentication, your identity posture will probably look quite different. But, you should still be wary of backup phishable factors and SSO gaps – more on this below.
Identity configurations and how they can be exploited
We analyzed a sample dataset of 300,000 accounts and the associated login methods – this is what we found.
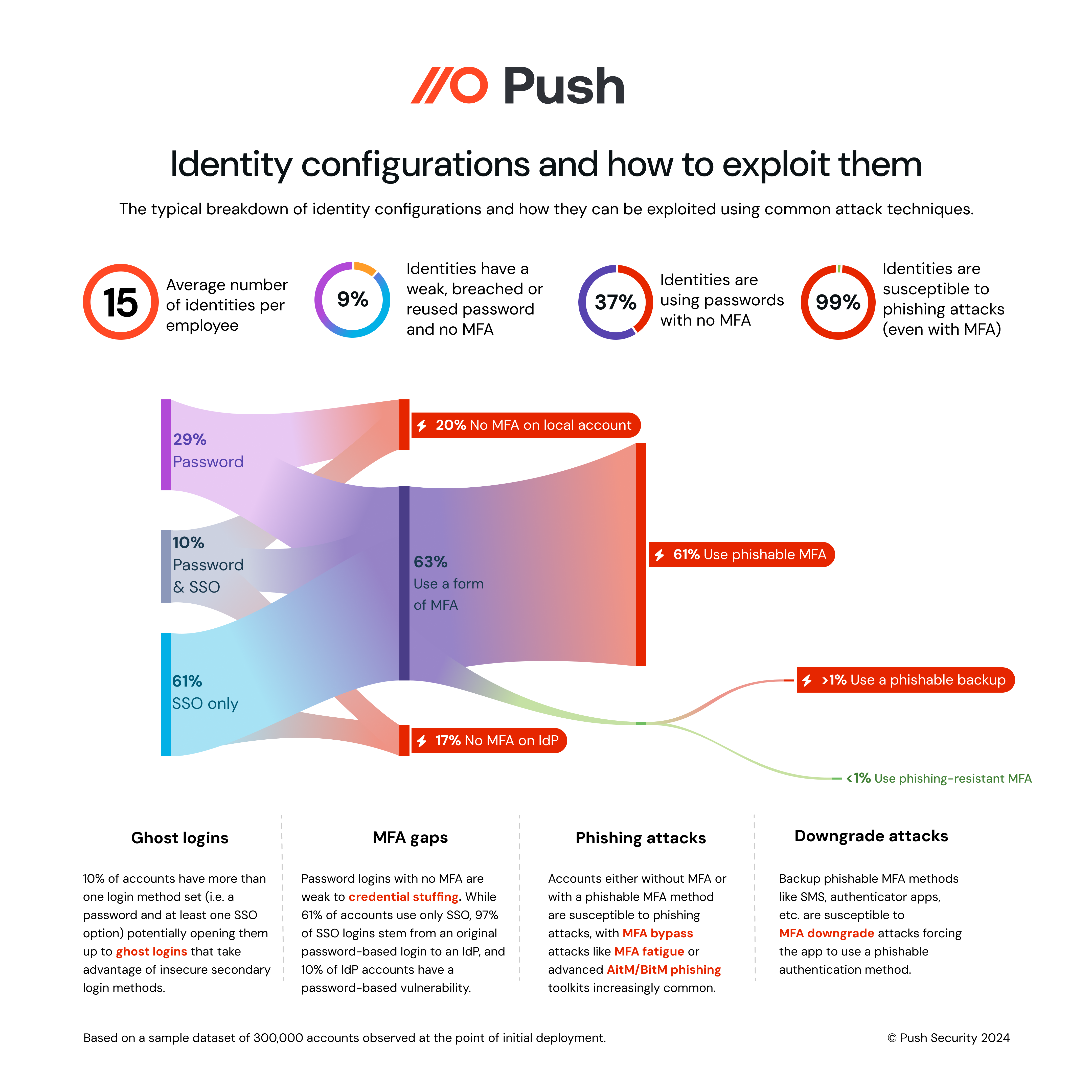
Some of the key insights are explored below.
Organizations are using more apps and identities than they realize
On average, each employee has ~15 identities tied to the business apps that they use, and each organization uses ~220 apps. The number of apps per organization doesn't show a strong correlation with the size of the organization. But, the number of accounts per user does tend to be lower for organizations with a larger employee base.
Many accounts lack the most basic protections
37% of all accounts do not have MFA set, while ~9% of accounts with a password also have a breached, weak, or reused password, making them highly susceptible to account takeover.
This might not seem that high at face value – but it’s enough that attackers can feasibly take over accounts linked to every business app used in the organization just by abusing password vulnerabilities through attacks like credential stuffing. For a 1,000 user organization, this leaves them with 1,367 user accounts that are highly vulnerable to account takeover.
The situation gets worse when a password is the sole login method set, with these accounts lacking MFA in 4 out of 5 cases.
SSO is not a silver bullet
SSO can be used to reduce an organization's susceptibility to password-based attacks, but the vast majority (97%) of SSO logins track back to an original password login to an IdP (due to the marginal use of passwordless authentication) while in 10% of cases a local password login is set alongside SSO – potentially introducing ghost logins.
You might expect these password-based logins to be highly scrutinized due to the criticality of these accounts – but we found that 1 in 5 IdP accounts is missing MFA, and a non-unique password is present for 10% of IdP accounts (meaning that if the same username and password combination is compromised on another app, the risk of a lateral account compromise is much higher).
Since Microsoft, Okta, and Google IdP accounts are the most targeted identities by attackers due to their value if compromised, these accounts are under a huge amount of pressure from attackers – multiplying the risk to single factor authentication IdP accounts.
Pretty much all identities can be phished
Almost all identities (~99%) are susceptible to phishing attacks – either because MFA is missing, or the types of MFA implemented are weak to modern phishing attacks such as Adversary in the Middle (AitM) phishing kits, or techniques such as MFA fatigue. The most common MFA methods are phone call, push notification, and one-time passcode – all of which are phishable or bypassable.
Even in the small number of cases where we identified a passwordless authentication method that is regarded as phishing-resistant (e.g. passkeys, biometrics, etc.) there is a backup, phishable method set for over half of them.
So... what does this mean in real terms?
The main conclusion from the data is that identity vulnerabilities exist almost everywhere. Some are certainly more likely to be exploited than others (e.g. an account with a reused password and no MFA is a higher risk than an account with MFA) but attackers have the means to take over most accounts using widely available tooling and know-how.
To bring this to life, here’s an infographic representing the identity attack surface for a 1,000 seat organization.
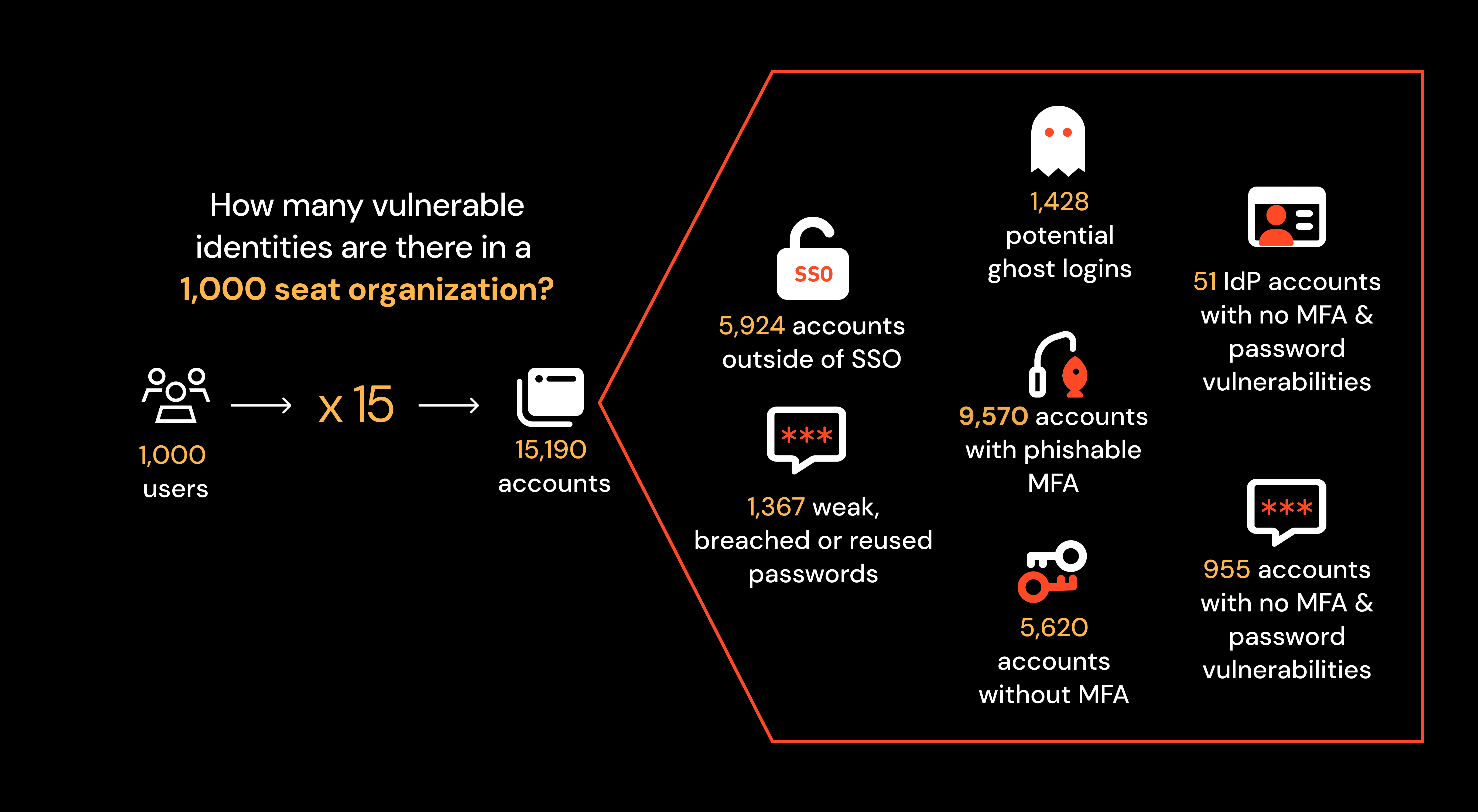
This shows that investing in your identity security baseline only gets you so far – ultimately, you need to be prepared to detect and respond to attacks rather than relying on prevention alone. That said, progress over perfection should always be the aim when it comes to posture management, and shoring up your identity vulnerabilities is an important long-term project.
Detection and response is the key
Looking at the scale of the challenge, it’s pretty clear that completely scrubbing your workforce identities of all possible vulnerabilities isn’t really an achievable goal. A strong baseline is important, but it will only ever get you so far. Rather than playing whack-a-mole, organizations need to prepare to detect and respond to the techniques and tools being used by attackers when they exploit these vulnerabilities.
This is nothing new – this approach has been preached by security operations leaders for more than a decade. But until now, identity security has been much more focused on prevention than detection and response. And with attackers increasingly turning to identity attacks, the sheer volume of identity vulnerabilities (and the rate that they are introduced) means that posture management alone isn’t sufficient.
Like endpoint and network security before, you can no longer rely on prevention alone, and organizations need to ensure they can detect and respond to indicators of identity attacks to be able to manage the risk effectively.
How Push can help
Push helps organizations to detect and prevent identity attacks as they happen, by intercepting and shutting down attacks in the browser. It also provides valuable data to find and fix identity vulnerabilities before they can be exploited. Book a demo here to find out more.


