Consent phishing is an emerging technique attackers are using to compromise user accounts, even if they have Multi-factor Authentication (MFA or 2FA) enabled. Consent phishing is particularly effective because it doesn’t exhibit many of the indicators that traditionally expose phishing attacks. However, there are sensible controls available.
Consent phishing is an emerging technique attackers are using to compromise user accounts, even if they have Multi-factor Authentication (MFA or 2FA) enabled. Consent phishing is particularly effective because it doesn’t exhibit many of the indicators that traditionally expose phishing attacks. However, there are sensible controls available.
With more platforms adding support for Multi-factor Authentication (MFA) and users increasingly adopting it to secure their accounts, attackers are adapting and moving to new methods of compromising user accounts. In this post we’ll take a look at consent phishing and how it is being used to bypass MFA and also skirt key attributes of phishing that are taught in traditional user awareness campaigns, such as links to untrusted domains.
Imagine yourself sitting down at your desk first thing on a Monday morning, cup of coffee steaming next to your keyboard as you click through your backlog of emails. You open the below email and you see that Karl has shared a financial report with you.
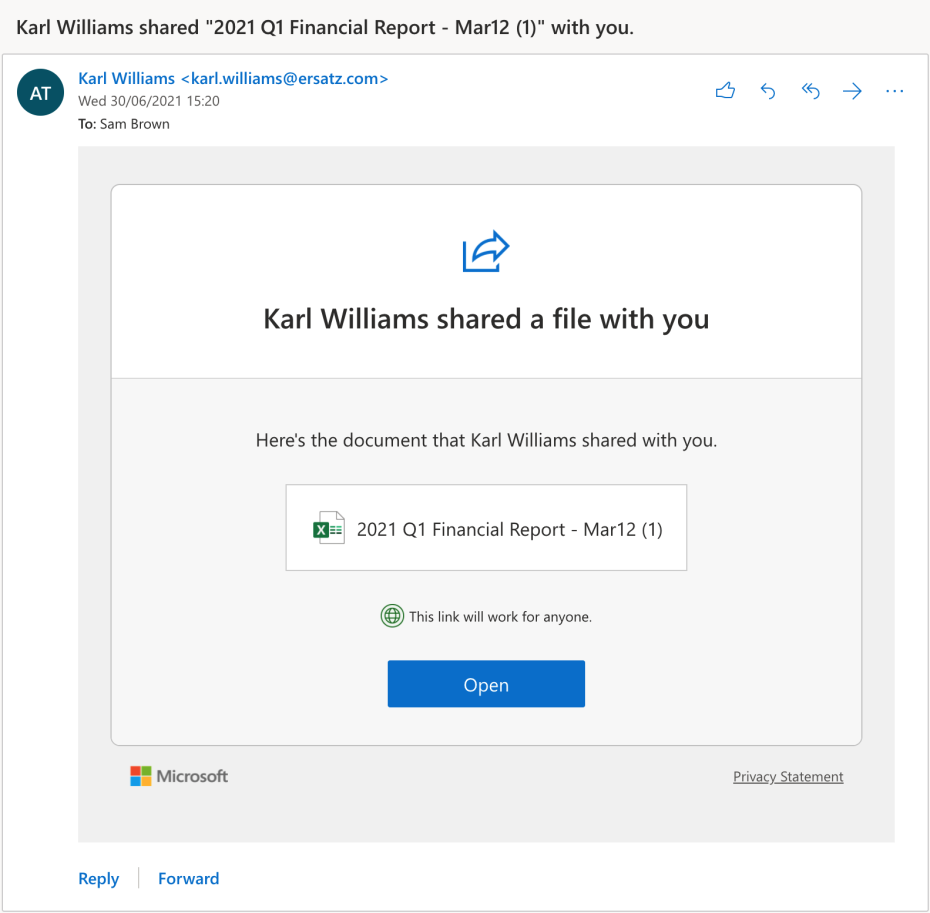
Maybe you’ve been waiting for the latest financials or you suspect this was sent erroneously but you’re curious and want to take a peek. When you click the link you are presented with a prompt that with your Monday brain looks just like the “Yes give me access” prompt you’ve clicked through a thousand times. I mean, it's a microsoftonline.com domain, it's https and there’s a green tick in the corner so everything looks fine.
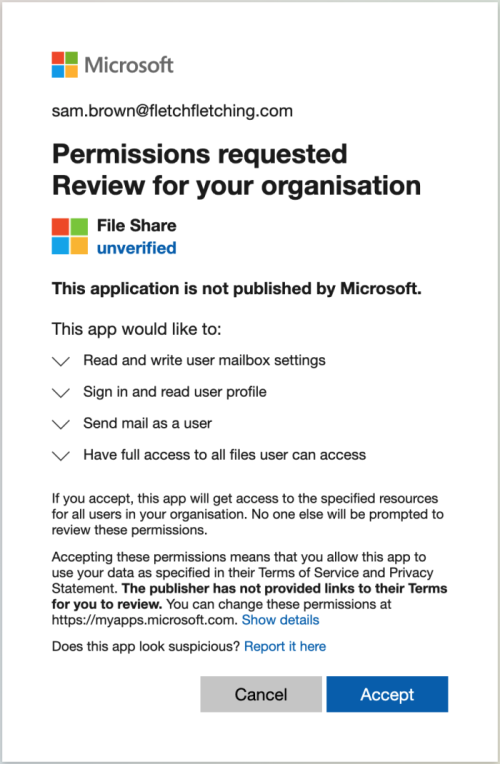
If you’d looked closely you may have noticed that this was in fact asking you to approve access rather than granting you access. But with your muscle memory in full control you click “Accept” before even glancing at the screen. You wait for the spreadsheet to open but are presented with a generic “File does not exist” error page. Oh well, apparently Karl realised his mistake and deleted the file or revoked your access. Onto the next email.
And just like that you’ve been consent phished. You’ve just granted the attackers permanent access to your account, which they retain even if you change your password or have MFA enabled. Chances are the attacker’s tools will immediately start downloading every piece of data you just granted them access to, which they can then explore at their leisure.
To spot this you need to audit the apps you’ve approved, something you are doing regularly, right? Seriously though, this isn’t something many people check. These integrations are designed to be as seamless as possible and not to get in your way. But if this has piqued your interest you can check what access you have personally granted on Google Workspace and Microsoft 365.
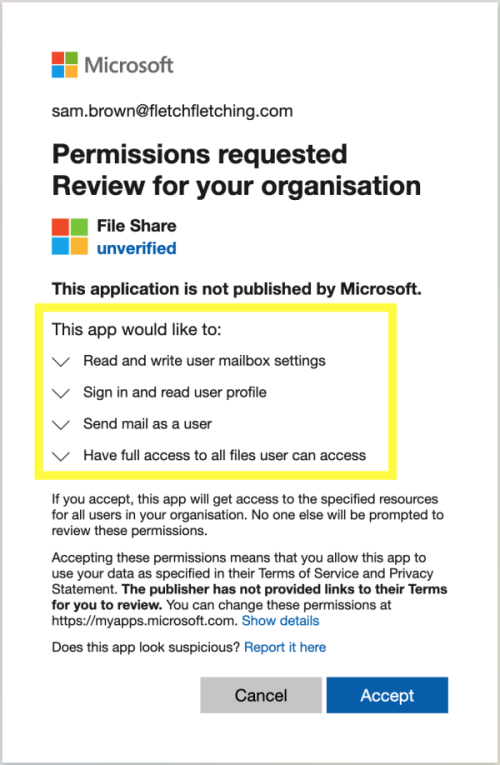
If you’d been paying attention when you clicked “Accept” you might have noticed that you were granting some pretty serious permissions here. These permissions allow the attackers to read and write any files you have access to - they could download all these files and then delete them. The attackers also got permission to send emails as you. They could send emails to your colleagues from you and phish them too, this isn’t impersonation where the email just “looks” like it came from you, the email DID come from you. Lastly the attackers asked for permission to manipulate your Outlook settings, with this they could set up a mail forwarding rule so that they get copies of all your emails forwarded to them directly without even having to log in. And all of this happens until you delete the underlying OAuth app.
In a blog post Microsoft warns that these attacks are on the rise. One notable example of this comes from the SANS Institute. They reported in August of 2020 that they had fallen victim to one of these attacks. As part of the investigation they produced a report with details on how the attackers managed to convince an employee to install a malicious Microsoft 365 add-in to gain access.
So what can you do about this threat today? The only fool proof method of preventing this kind of attack is to prevent users from granting access to third party apps. This is terrible for users though, and you’ll be missing out on all the productivity benefits these apps can bring. A more balanced approach is to let users find and request apps, but have administrators approve the apps. More and more platforms (including Microsoft 365 and Slack) are offering built-in “admin consent” workflows to make getting a second pair of eyes on new apps even easier. You can also make it even easier for users by pre-approving widely used apps from trusted publishers and users won’t even notice there is new protection in place 99% of the time. We are also actively working on this problem and if you would like to join our early access program please get in touch.
Consent phishing is still an emerging technique and we believe that it has not reached peak usage by attackers yet. We are actively researching this attack technique as it continues to evolve. Follow us on Twitter @pushsecurity, LinkedIn or subscribe to our mailing list below to get the latest updates and tips for managing this for your users.



